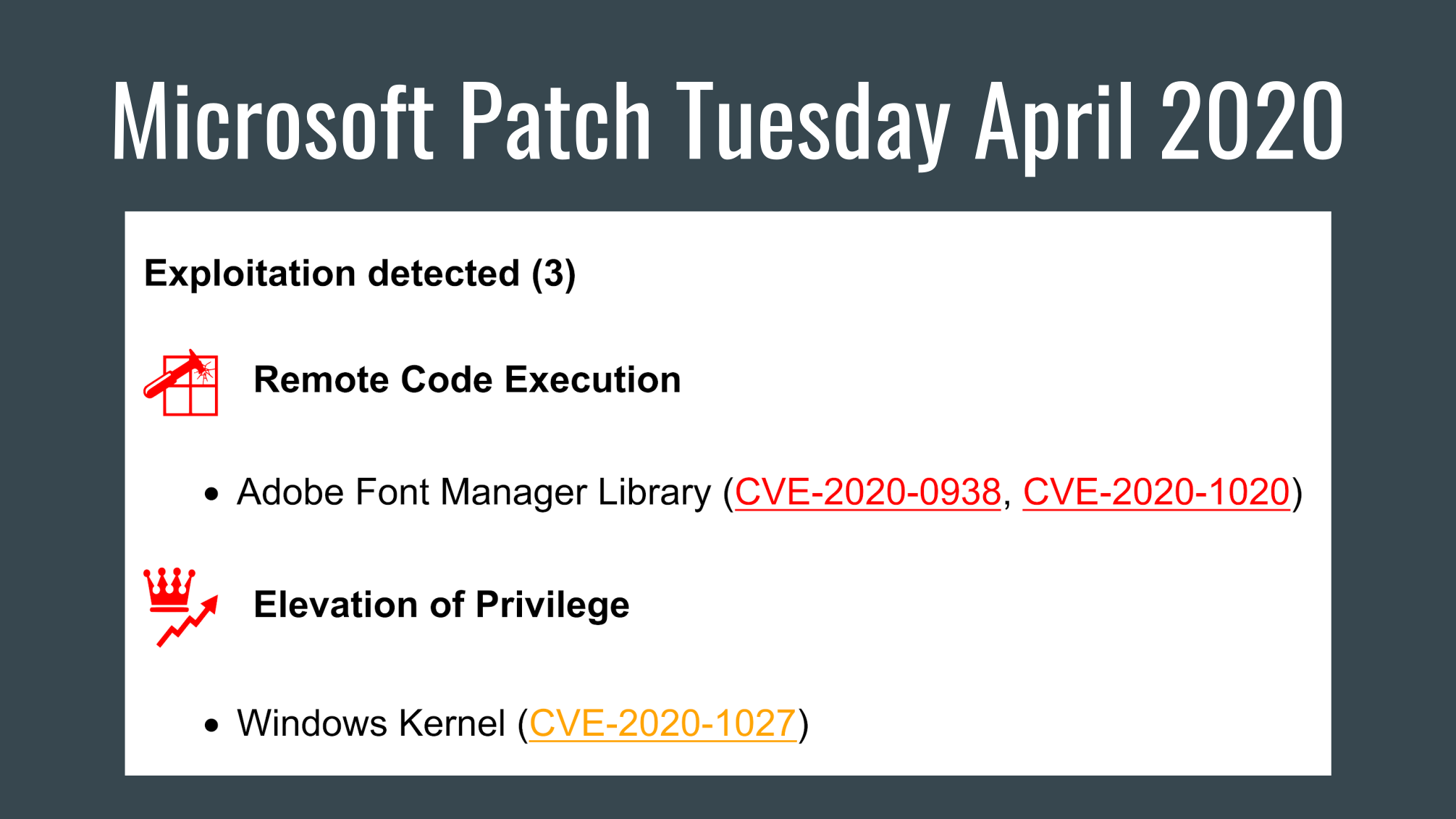
This episode is based on posts from my Telegram channel avleonovcom, published in the last 2 weeks. So, if you use Telegram, please subscribe. I update it frequently.

Barapass update
I recently released an update to my password manager barapass. BTW, it seems to be my only pet project at the MVP stage, which I use every day.
What’s new:
- Now I am sure that it works on Windows 10 without WSL. And you can run it beautifully even with the icon. ? Read more about installation in Windows in this file.
- Not only “copy the next value to the clipboard” (or “revolver mode” ) is now possible in the search results section. You can also get the previous value or copy the same value one again if it was somehow erased in the clipboard. Previously, I had to retype the search request each time to do this, and it was quite annoying. By the way, I unexpectedly discovered that the user input history inside the application magically works in the Windows shell (using up and down arrows) without any additional coding. On Linux it does not.
- You can set a startup command, for example, to decrypt the container.
- The startup command and quick (favorite) commands are now in settings.json and not hard-coded.
- settings.json, container files and decrypted files are now in “files” directory. It became more convenient to update barapass, just change the scripts in the root directory and that’s it. I divided the scripts into several files, now it should be more clear how it works.
So, if you need a minimalistic console password manager in which you can easily use any encryption you like – welcome! You can read more about barapass in my previous post.
Continue reading