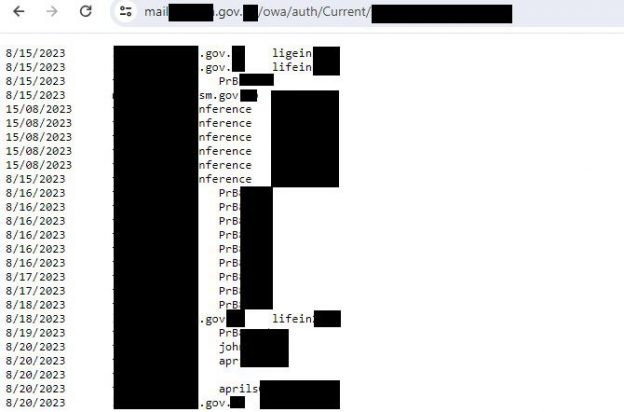
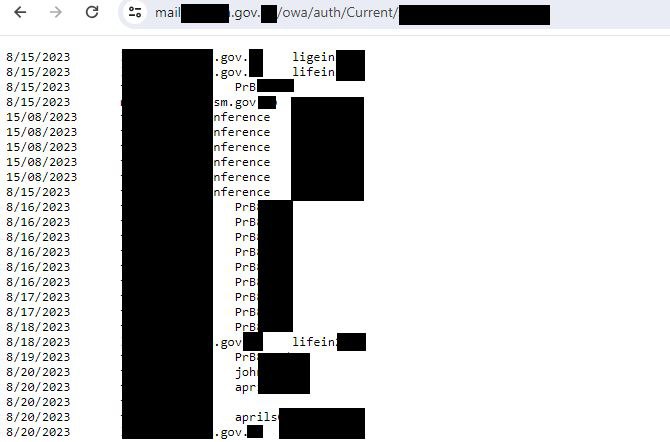
My colleagues from PT ESC discovered a previously unknown keylogger for Microsoft Exchange OWA. The injected code collects the logins/passwords that users enter to access the Exchange web interface and stores them in a special file. This file is accessible externally. Thus, attackers simply collect credentials to access confidential information and develop the attack further. 🙂
👾 The malware is installed by exploiting an old ProxyShell vulnerability (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207).
🏛 A total of 30 victims were discovered, including government agencies, banks, IT companies, and educational institutions.
🌍 Countries attacked: Russia, UAE, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, Lebanon and others.
🕵️♂️ The fact of compromise can be determined by a specific line in the logon.aspx file.