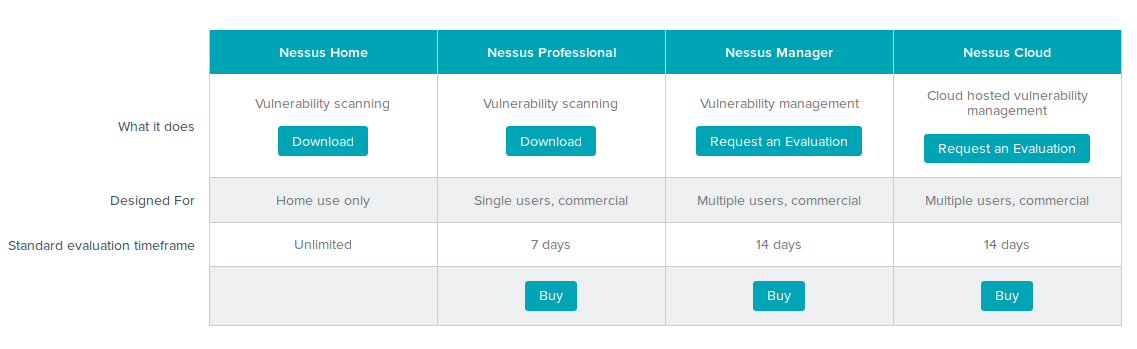
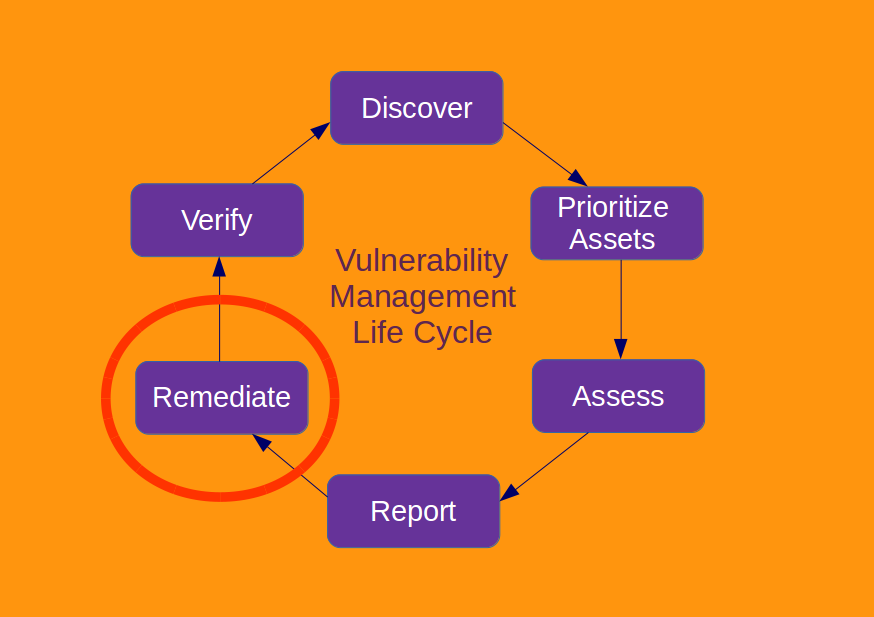
Tenable Nessus: registration, installation, scanning and reporting. It’s a bit strange that I wrote in this blog about some relatively exotic vulnerability management solutions and not about the one I use every day. It is, of course, Nessus. The legend of vulnerability scanners. It would be fair to say that Nessus has become a synonym for vulnerability scan itself as Xerox for photocopy. First version of Nessus was developed by Renaud Deraison in 1998 as a free and open-source product. In October 2005 the license was changed to proprietary. The last version of GPL source codes became the base for the great open source vulnerability scanner – OpenVAS (btw, see my post “openvas_commander for OpenVAS installation and management”).
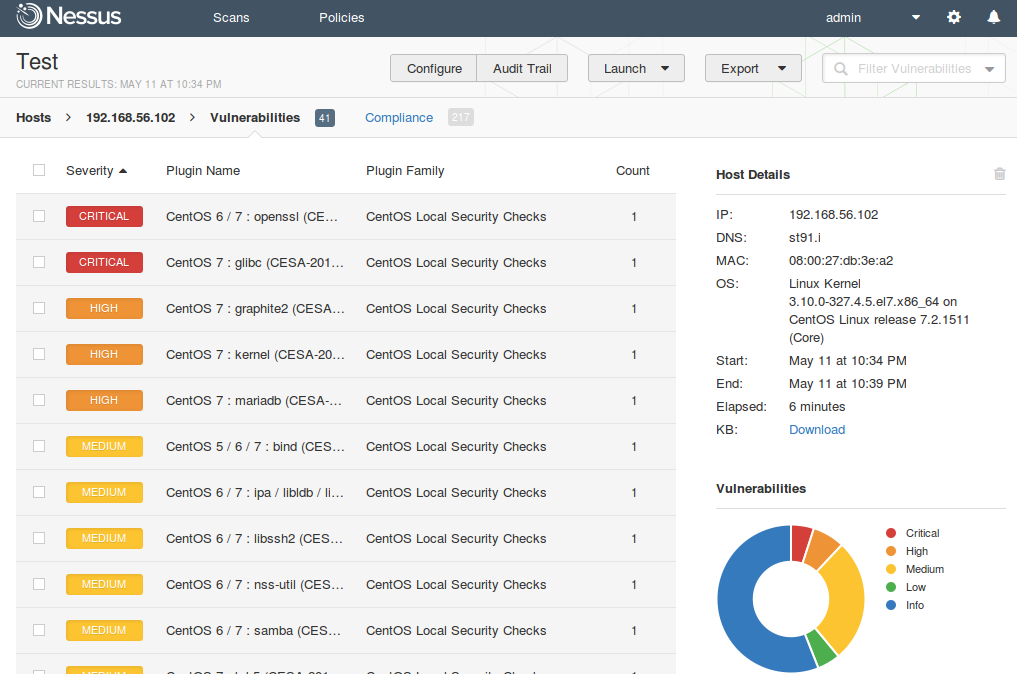
I am glad that Tenable still keeps Nessus mostly in UNIX-way. Nessus is a vulnerability scanner and makes one thing good – finds vulnerabilities on network hosts. If you need dashboards, advanced user management, advanced reporting capabilities, etc. use Tenable Security Center that works above the Tenable separate products: Nessus, Passive Vulnerability Scanner (PVS) and Log Correlation Engine (LCE).