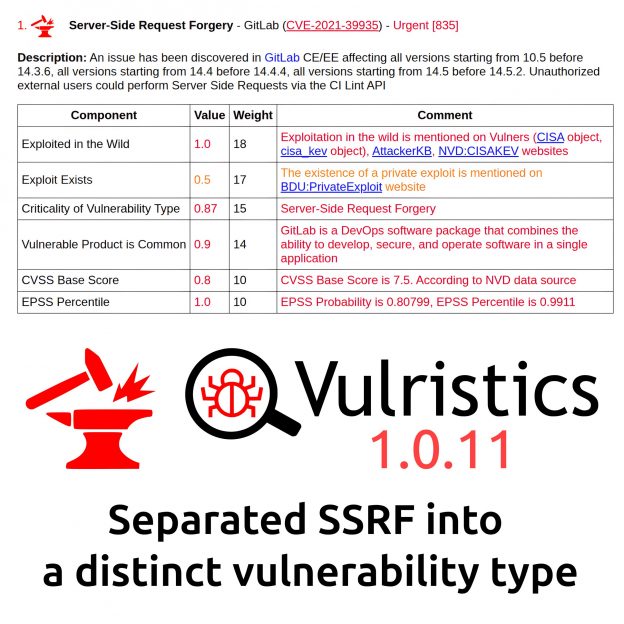
February Linux Patch Wednesday. In February, Linux vendors addressed 632 vulnerabilities – 1.5× fewer than in January, including 305 in the Linux Kernel. Two vulnerabilities show signs of in-the-wild exploitation:
🔻 RCE – Chromium (CVE-2026-2441)
🔻 InfDisc – MongoDB “MongoBleed” (CVE-2025-14847)
Public exploits are available or suspected for 56 more vulnerabilities. Notable ones include:
🔸 RCE – OpenSSL (CVE-2025-15467, CVE-2025-69421, CVE-2025-11187), pgAdmin (CVE-2025-12762, CVE-2025-13780), DiskCache (CVE-2025-69872), PyTorch (CVE-2026-24747), Wheel (CVE-2026-24049)
🔸 AuthBypass – M/Monit (CVE-2020-36968)
🔸 EoP – Grafana (CVE-2025-41115, CVE-2026-21721), M/Monit (CVE-2020-36969)
🔸 AFR – Proxmox Virtual Environment (CVE-2024-21545)
🔸 SFB – Chromium (CVE-2026-1504), Roundcube (CVE-2026-25916)