Altx-Soft ComplianceCheck against cryptolockers and ransomware. ComplianceChecker is a free Compliance Management tool made by Altx-Soft, a security product company from Moscow Region, Russia. Altx-Soft is known abroad mainly as a Top OVAL Contributor, they have been on award-list every quarter since 2012. Their flagman product, RedCheck, is a SCAP-compatible vulnerability and compliance scanner. They also produce family of “Check”-products for controlling and managing Windows operating systems.
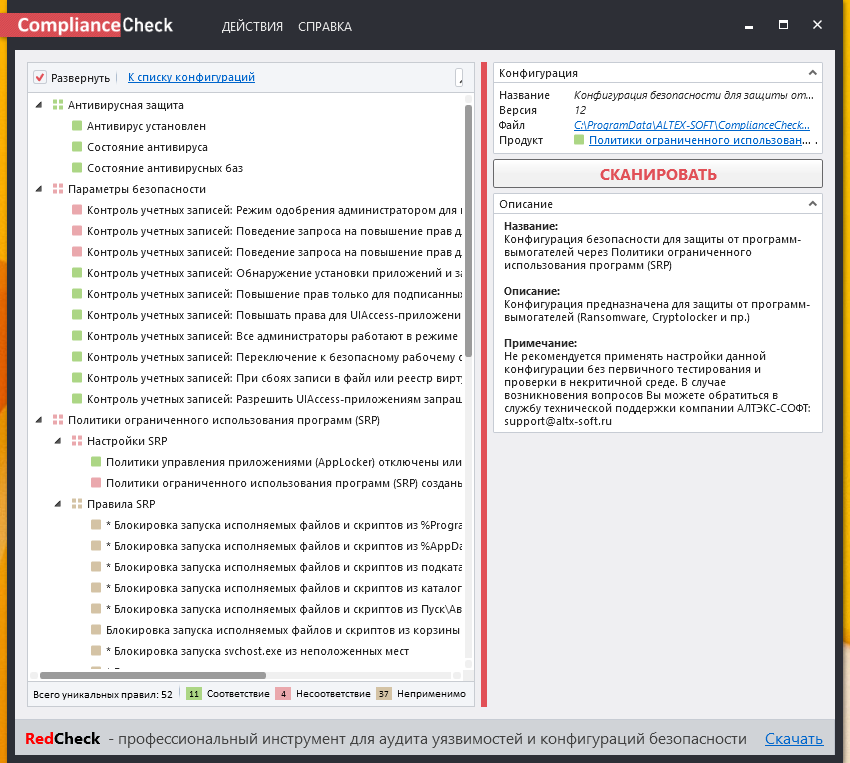
ComplianceChecker is a promo product for the potential RedCheck buyers. It similar to RedCheck with the most management features cutted off. It can scan only the localhost.
ComplianceChecker is positioned mainly as an utility for SOHO/Home users and it’s not a secret, that on this market Compliance Management solutions are still an exotic. How could they attract the attention of an ordinary people? Altx-Soft took the hottest security topic of 2014-2015 – cryplockers and ransomware, that nowadays are the real threat for literally all kind of platform and especially Windows desktops. Altx-Soft tried to spread the message, that the best way to protect operating system from this kind of malware is to configure it properly. And it’s hard to disagree. So, they made a tool for the security assessment – ComplianceChecker, and made some other tools configure to operating systems (free for RedCheck users).
I have downloaded Compliance Checker here: http://www.altx-soft.ru/files/download/cc.zip
It’s a bit a strange to describe in English a tool, that is available only in Russian. Yep, unbelievable, but there is no English language support at all. I hope, that this post could maybe somehow motivate Altx-Soft to translate it 😉 But don’t be afraid. Interface of the tool is trivial and I will do my best to describe what is happening on the screenshots.
Let’s see the basic functionality.
Installation process is straightforward. You just need to press second Next (“Далее”) button. No attempts to install bloatware or anything like this.
Start the installation… “Начать”
And it is finished! “Готово”.
There are two policy checks available:
- Configuration against ransomware through Software Restriction Policies (SRP)
- Configuration against ransomware through Application Management Policies (AppLocker)
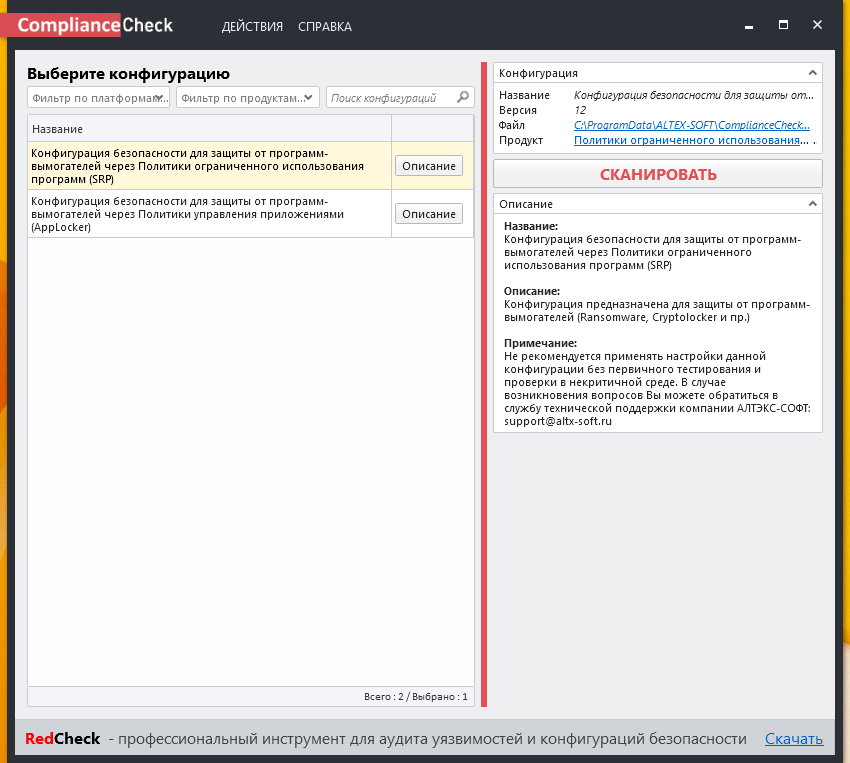
Choose one policy and press button with red letters. To scan: “СКАНИРОВАТЬ”. And then the window with control statuses will appear. Scanning takes 1-2 seconds.
For SRP:

The same for AppLocker:
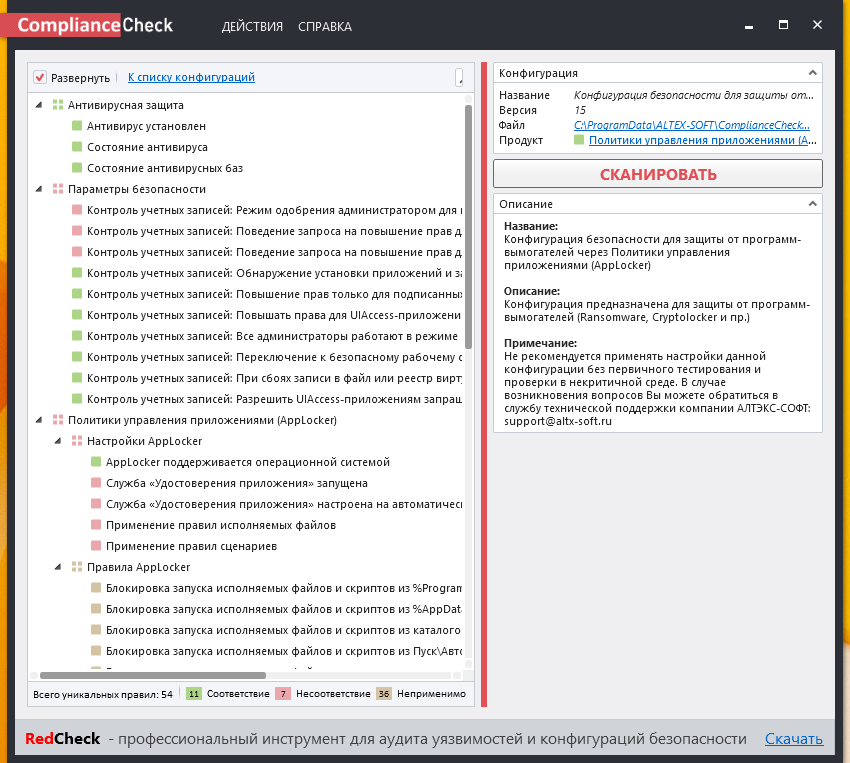
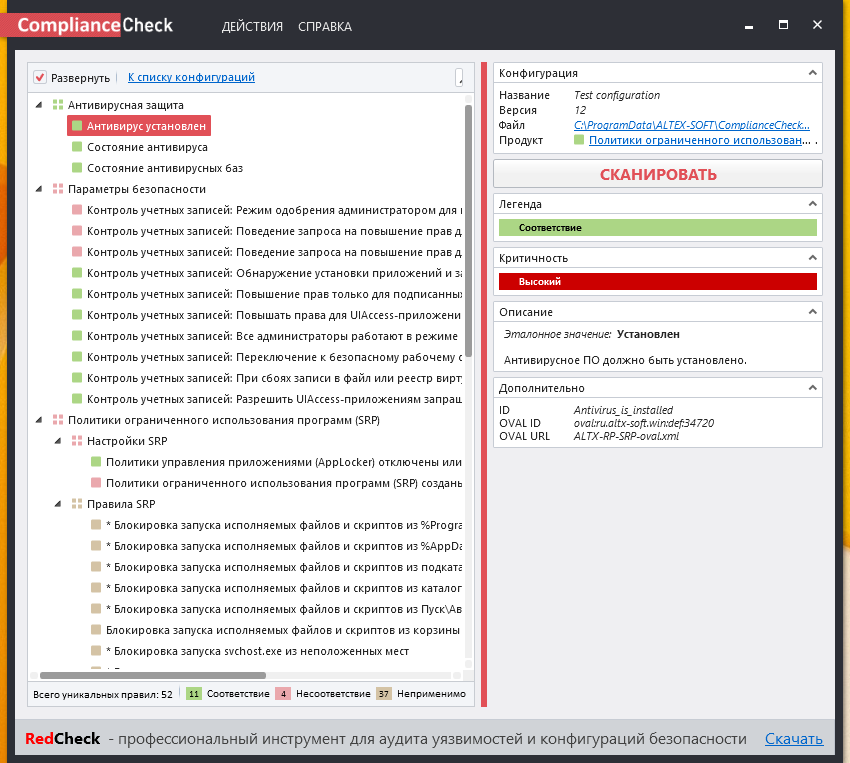
When you press on the security control you will see control description on the right panel.
At the bottom you can see statistics for the controls: pink – non-compliant, green – compliant, gray – not applicable.
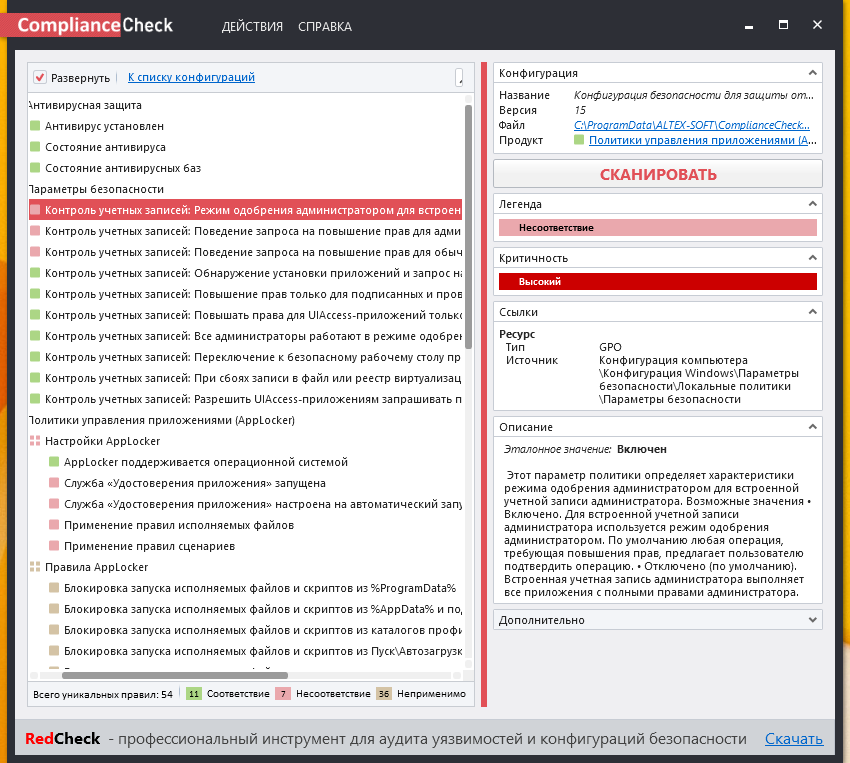
SRP and AppLocker are not configured in my system, so all those controls are in “not applicable” state. But some controls: antivirus configuration, account management configuration are checked correctly.
Security content content is stored here:
C:\ProgramData\ALTEX-SOFT\ComplianceCheck\Data\Benchmarks\
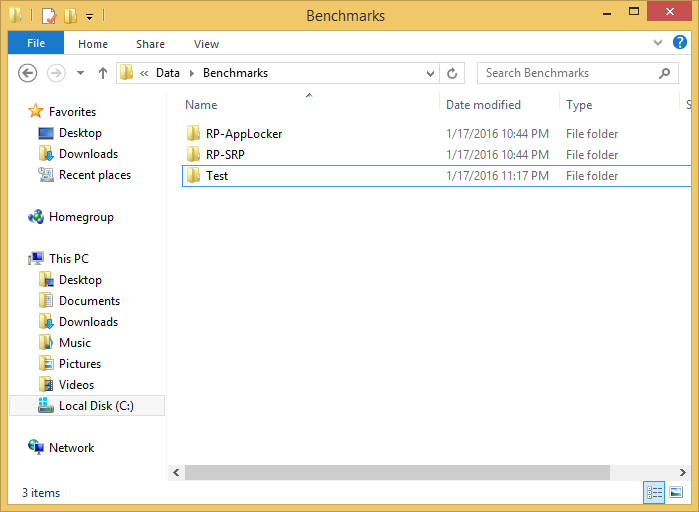
I have copied folder RP-SRP folder as Test. You can see standard SCAP feed inside:
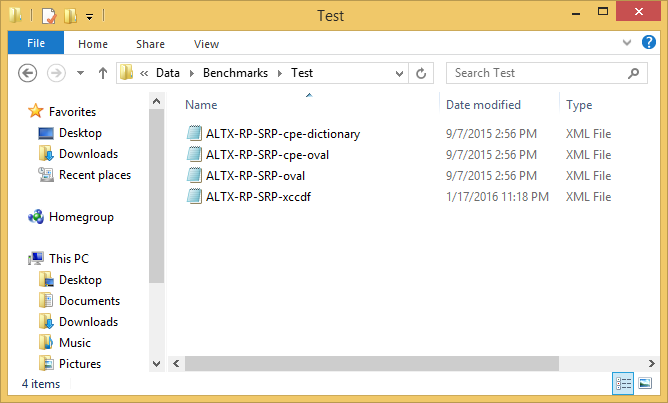
I have changed title in xccdf file.
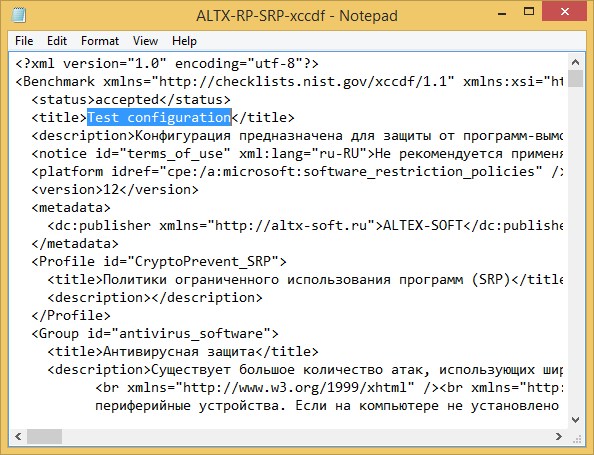
Restarted application. New configuration policy appeared.
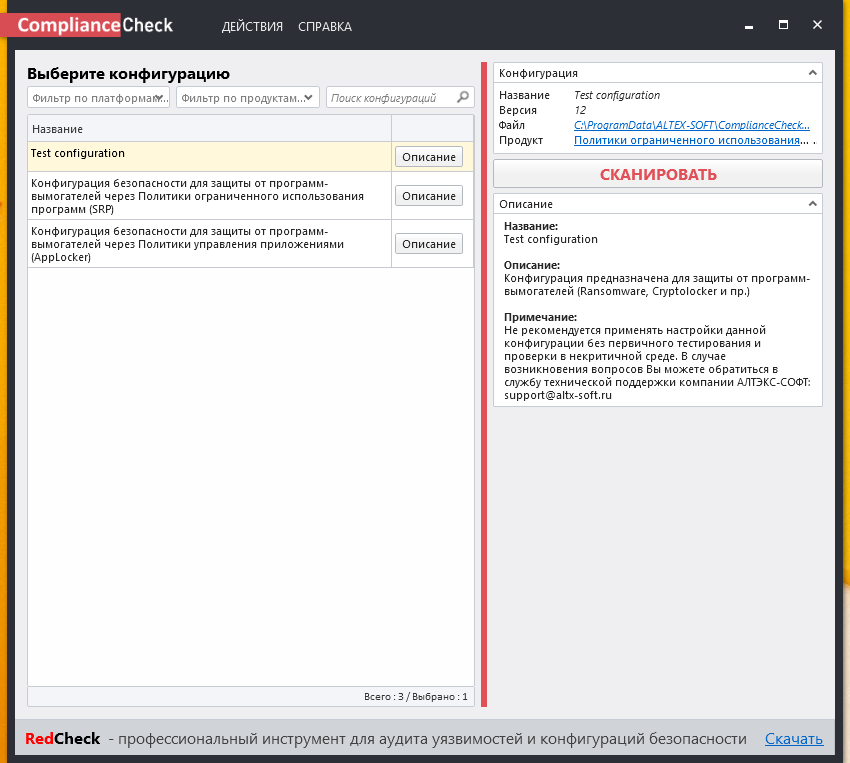
And this policy is scannable.
Ok. Let’s try something more interesting. I have downloaded DISA STIG content for windows 8 and put it in the same folder.
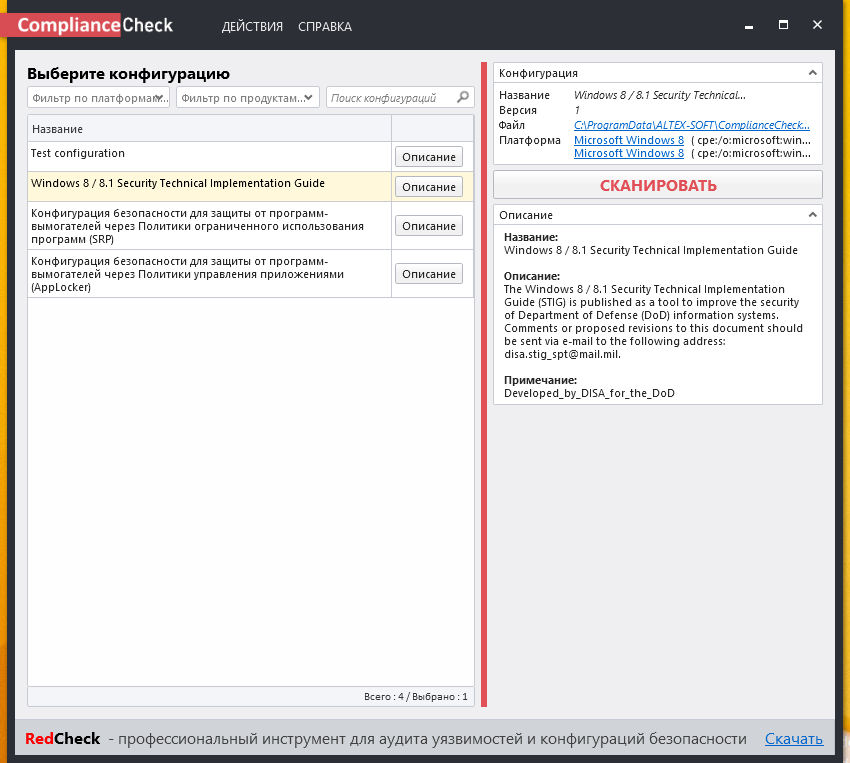
Scanning took about 5 minutes. And in It works!
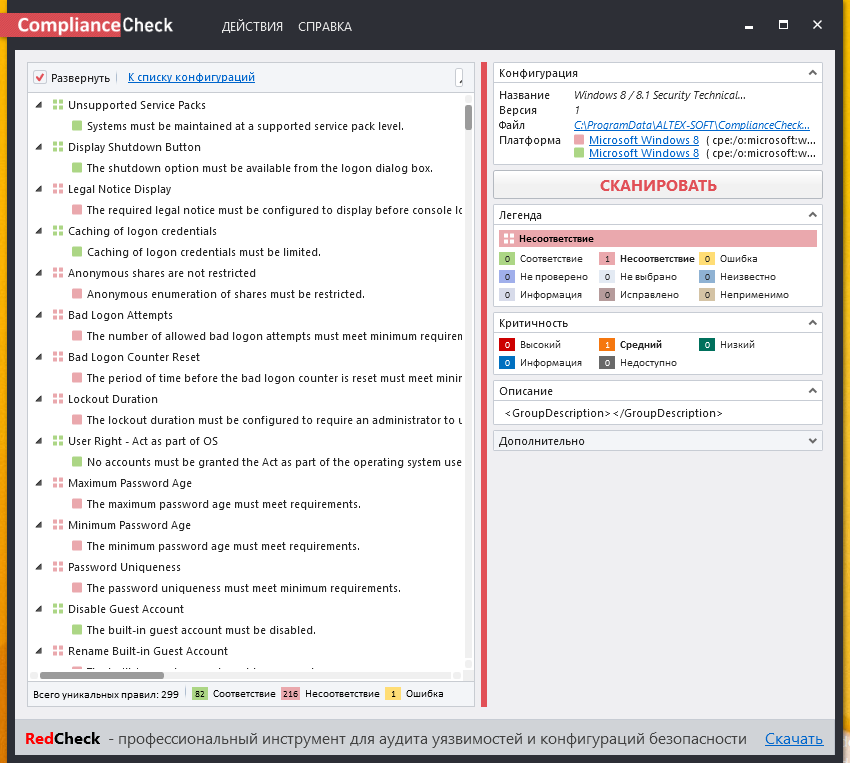
A bit sad, that there is no option to save scan results. But we have OVAL definition result file in Temp folder:
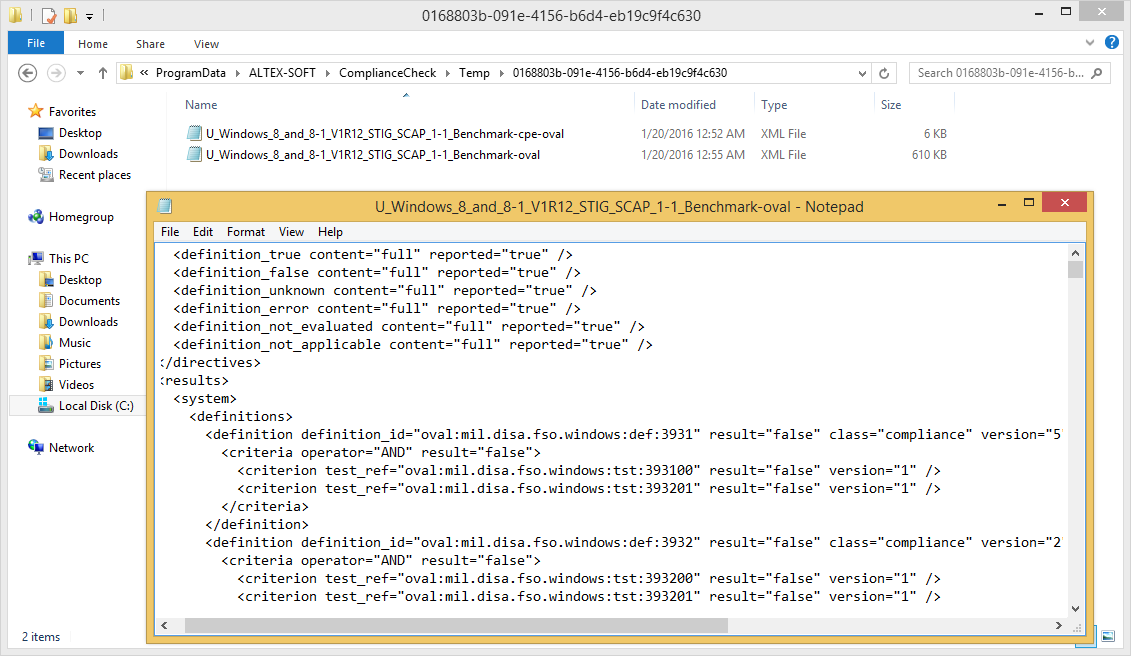
In conclusion: Even basic functionality of the tool, compliance checking against cryptolockers and ransomware, is very interesting and useful. But, I think the ComplianceChecker has even bigger potential as a free universal compliance framework. Right now it is highly customizable and has an ability to run DISA STIGS and other SCAP content as is. It is free, it is fast. It seems good for testing and developing new security content, especially in situation when ovaldi development is stopped.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Vulnerability Management vendors and massive Malware attacks (following the BadRabbit) | Alexander V. Leonov