ERPScan SAP security scanner. 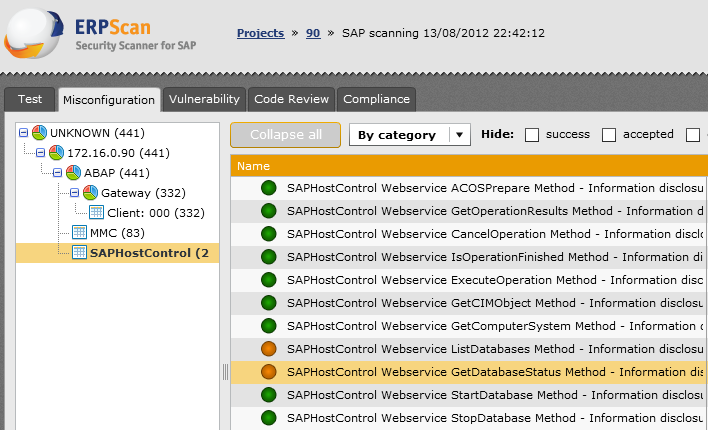
I had a chance to see presentation and live demo of ERPScan – automated SAP scanning solution, and it made quite an impression on me. ERPScan has interesting scanning features. The most spectacular, in my opinion, is ability to run exploits for found vulnerabilities directly from the scanner.
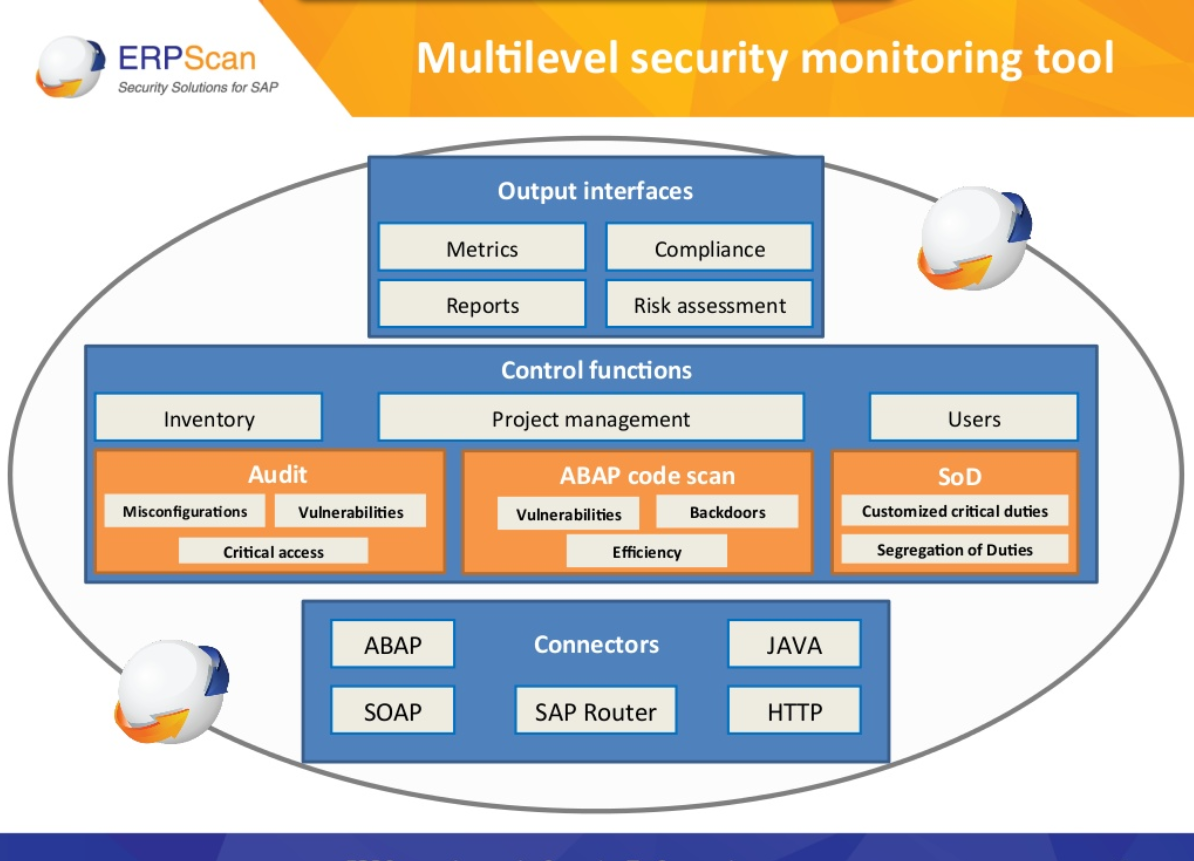
Some other pleasant things:
- You can add tags to the scanning tasks. Seems useful when you have hundreds of different tasks
- You can check account, that will be used for credentialed scanning and in the same window will be shown minimal information about the system
- You can change or even accept risk level for vulnerabilities and misconfigured user accounts
- You can mark vulnerability as false positive and you can attach comments to it
- You can associate vulnerability with email of responsible system administrator and he will get messages about this vulnerability
I was pleased to see a nice form of report – automatically generated PowerPoint presentation for C-level executives with diagrams, animation, etc.
Interesting feature “Threat Map”, unfortunately I haven’t seen it in live demonstration.
“Threat Map functionality can save your time by providing you with an information about how systems are interconnected, you can eventually use it for privilege escalation and pivoting.”
ERPScan can also patch vulnerable systems automatically. I haven’t seen how it works in real life, but it’s intriguing.
I haven’t found any real cons yet. Of course it would be better to use universal vulnerability scanner, not only for the SAP. But on the other hand, this specialization allows ERPScan team to achieve good results.
Another pretty specific need for me is managing scanner via API. ERPScan developers say that API support will be released later. It is certainly possible to make regular scan, and take the results from the shared folder, but it is not that cool.
And the solution is not cheap. I will not say the cost, because I do not really know, but it is not Nessus level at all. =)
(pictures from the public sources)

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Remediation capabilities of Vulnerability Management products | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Gartner’s view on Vulnerability Management market | Alexander V. Leonov
Pingback: Kenna Security: Analyzing Vulnerability Scan data | Alexander V. Leonov
Pingback: PRYTEK meetup: Breach and Attack Simulation or Automated Pentest? | Alexander V. Leonov
Pingback: Tadviser пишет, что менеджмент российского SAP-а отказался выкупать компанию | Александр В. Леонов
Pingback: Итак, вы решили начать разработку своего Vulnerability Management решения | Александр В. Леонов
Pingback: U.S. sanctions against Russian cybersecurity companies | Alexander V. Leonov