Somebody is watching you: IP camera, TV and Emma Watson’s smartphone. Today I want to talk today about privacy in a most natural sense. You probably have an internet-connected device with camera an microphone: smartphone, tablet, smart TV, ip camera, baby monitor, etc.
– Can it be used to record video/audio and spy on you?
– Of course, yes!
– Only government and device vendor has resources to do it?
– Not really

The sad truth is: most of internet-connected devices have security problems, and, unlike traditional desktops and servers, it’s much harder to patch them. Even if the vendor fixed the issue. The customers, average people, just don’t bother themselves to do it. Each week it’s become easier to access user data and even get full control over device. Hackers and pranksters may do it just for lulz, because they can.
Let’s see it on concrete examples.
IP/Surveillance cameras
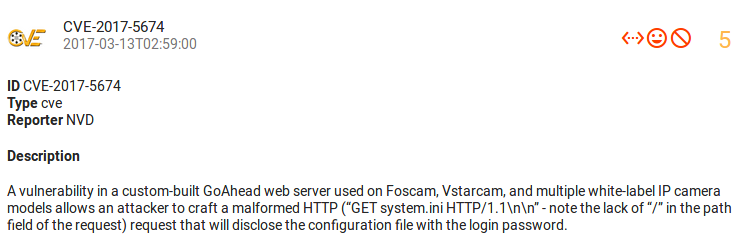
On this week Cybereason disclosed critical vulnerability in Foscam US, VStarcam, and multiple white-label CCTV IP Cameras.
You can get configuration file with the login and password with only one request:
GET system.ini HTTP/1.1\n\n
What does this mean? Several million webcams will not disappear from the Internet anyway. Some of them show children. Some of them will destroy families. In many cases, the recorded content will be used for blackmailing.
And it’s real. Just watch tons of IP camera pranks on youtube!
If this vulnerable camera is watching you at your workplace, it’s the problem of responsible person in your organization. But if you use IP camera to control your home, to watch for your children – it’s your problem and only you can deal with it.
TVs
Well, I don’t know why modern TVs should have built-in camera and mic. You can use your smart TV for Skype conferences but it’s a bit it still a bit weird and potentially dangerous. Something in Orwell style.
Last week Wikileaks published information on “Weeping Angel” malware. It can transform smart TV’s into microphones:
Samsung smart TVs, which previously drew criticism for their always-on voice command system, are vulnerable to Weeping Angel hacks that place the TVs into a “Fake-Off” mode. In Fake-Off mode, the TV owner believes it is off when it is actually on, allowing the CIA to record conversations “in the room and sending them over the Internet to a covert CIA server.”
However, this malware will not work on latest Samsung smart TV firmware. So, update it!
Smartphones and Tablets
Mobile phones vulnerabilities on this week should be illustrated with recent Emma Watson’s incident.

As you probably heard, some amount of private photo/video content leaked yesterday. Well, it’s not clear how the attackers got this contents. In pretty similar cases three years ago Apple iCloud access was obtained with some social engineering. But for sure, mobile devices and cloud services are not the best way to store sensitive data.
Once you took a photo with your smartphone, it can leak, simply because some malware was installed on the device. One of the main reasons why malware can work on the device is that the device is not updated and has some critical vulnerabilities. And how can it be updated if the manufacturer is not required to release updates even for most critical vulnerabilities, like Stagefright? And you can only put the latest version of Android on a very small amount of expensive smartphones, like Nexus and Sony Open Devices. The rest of the Android users are forced to use the affected devices, because the vendor does not update promptly.
Moreover, malware can be preinstalled even on a a new device. For example, two days ago Check Point Software Technologies found 38 Android handsets were infected with adware, information-stealing malware and ransomware, a collection of malicious code as sundry as the number of different manufacturers. Malware was pre-installed somewhere along the supply chain.
In conclusion
Vulnerability Management and Vulnerability Intelligence are not only for big companies anymore. Every person, every household is like a “microcorparation” with own IT assets, sensitive data and risks. If you don’t want your private staff become public and you don’t want somebody frightened your child at night using remote access to the baby monitor (and you can find this kind of “pranks” on youtube as well) YOU, customer, should care about all this boring technical stuff:
- How vendor of your internet-connected device patches vulnerabilities?
- How to figure out that your device is vulnerable?
- How to figure out that somebody can get control of your device?
- How to update your device?
- What to do if it can’t be updated?
Or just don’t use connected devices with mics and camera. Or stick tape camera and microphone like FBI Director James Comey and Mark Zuckerberg. It’s of course not an option for devices, where permanent audio/video recording is the main function.
Welcome to a brave new world!

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
