What’s inside Vulners.com database and when were security objects updated last time. As I already wrote earlier, the main advantage of Vulners.com, in my opinion, is openness. An open system allows you to look under the hood, make sure that everything works fine and ask developers uncomfortable questions why there were no updates for a long time for some types of security objects.
You can do this by using the https://vulners.com/api/v3/search/stats/ request, that I already mentioned in “Downloading entire Vulners.com database in 5 minutes”
First of all, let’s look at the security objects. This will give us an understanding of Vulners.com basis.
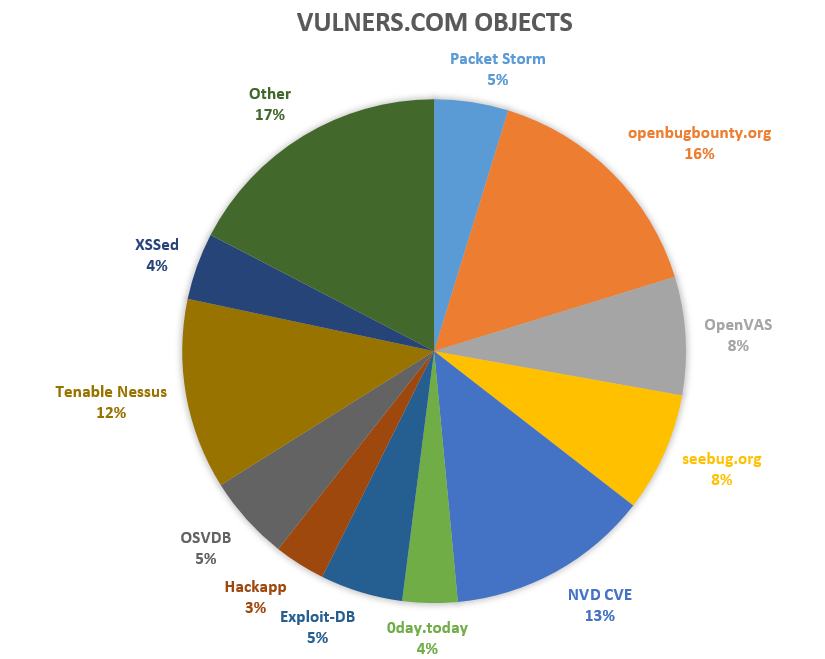
| Object | Amount | Procent, % |
|---|---|---|
| Packet Storm | 34441 | 4 |
| openbugbounty.org | 112131 | 15 |
| OpenVAS | 54901 | 7 |
| seebug.org | 55596 | 7 |
| NVD CVE | 94218 | 13 |
| 0day.today | 25572 | 3 |
| Exploit-DB | 38373 | 5 |
| Hackapp | 23860 | 3 |
| OSVDB | 39560 | 5 |
| Tenable Nessus | 88731 | 12 |
| XSSed | 31160 | 4 |
| Other | 125788 | 17 |
As you can see, the biggest parts are the National Vulnerability Database and plugin bases of Tenable Nessus and OpenVAS vulnerability scanners. Also, a large role is played by openbugbounty.org.
Vulners supports many relatively small exploit databases. But if we construct a diagram for the object types (families), we will clearly see that the distribution is approximately by 1/4: NVD CVE + unix + other software vulnerabilities, scanner detection plugins, exploits, bugbounty programs. Remaining 9% are different sorts of media resources.
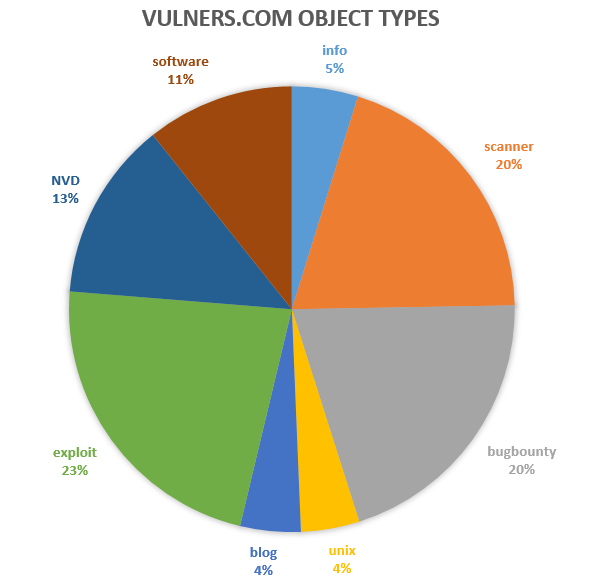
| Object Type (family) | Amount | Procent, % |
|---|---|---|
| info | 34711 | 4 |
| scanner | 144360 | 19 |
| bugbounty | 147613 | 20 |
| unix | 30763 | 4 |
| blog | 31788 | 4 |
| exploit | 163271 | 22 |
| NVD | 94218 | 13 |
| software | 77607 | 10 |
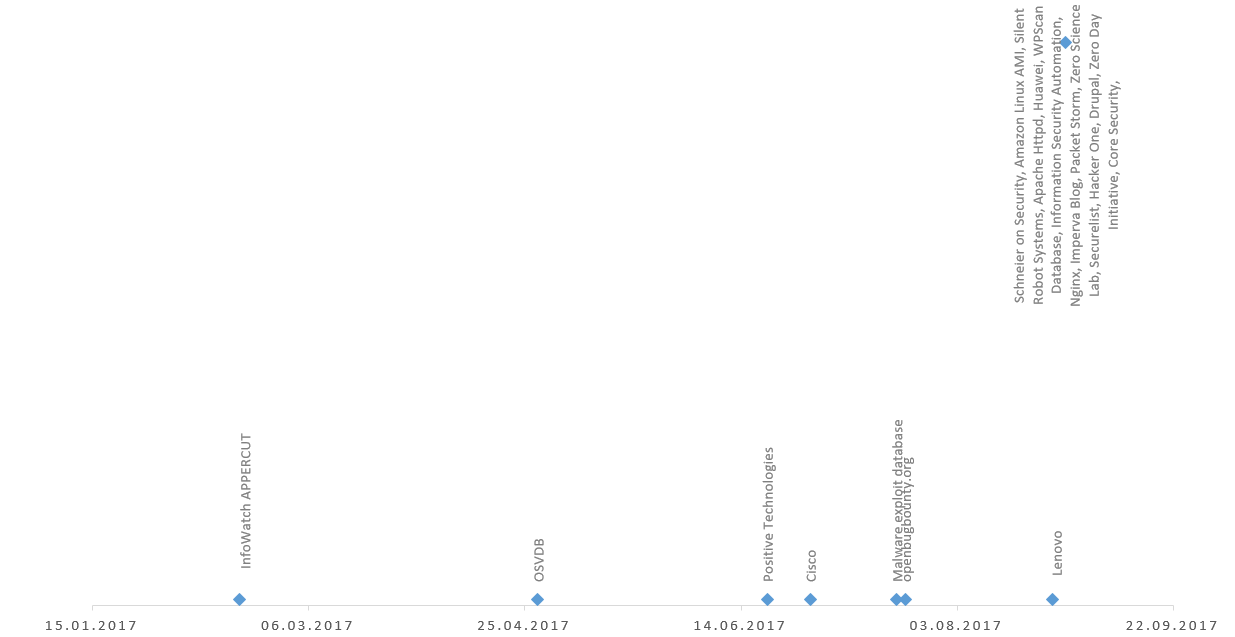
Finally, let’s see when were these objects updated last time.
| Date | Amount | Object |
|---|---|---|
| 2017-02-18 | 1 | InfoWatch APPERCUT |
| 2017-04-28 | 1 | OSVDB |
| 2017-06-20 | 1 | Positive Technologies |
| 2017-06-30 | 1 | Cisco |
| 2017-07-20 | 1 | Malware exploit database |
| 2017-07-22 | 1 | openbugbounty.org |
| 2017-08-25 | 1 | Lenovo |
| 2017-08-28 | 93 | Schneier on Security, Amazon Linux AMI, Silent Robot Systems, Apache Httpd, Huawei, WPScan Database, Information Security Automation, Nginx, Imperva Blog, Packet Storm, Zero Science Lab, Securelist, Hacker One, Drupal, Zero Day Initiative, Core Security, White Hats – Nepal, rdot.org, OpenVAS, Into the symmetry, Rapid7 Community, ownCloud, seebug.org, Krebs on Security, Binamuse, Palo Alto Networks, Microsoft Malware Protection, SUSE Linux, DSquare Exploit Pack, Wired Threat Level, NVD CVE, Symantec, Vulnerability Lab, Immunity Canvas, Talos Blog, VMware, TYPO3, 0day.today, KoreLogic Security, W3AF, Node.js, Debian Linux, Oracle Linux, Samba, NMAP, Trend Micro Simply Security, Filippo.io, Talos Intelligence, Mozilla, Anand Prakash’s blog, Atlassian, Gentoo Linux, Hackapp, Web Security Log, Opera, Wallarm Lab, The Hacker News, Ivan ‘d0znpp’ Novikov, Xen Project, PenTestIT, Akamai Blog, Tenable Nessus, Exploit-DB, High-Tech Bridge, Carbon Black Blog, Metasploit, Richard Bejtlich’s blog, XSSed, FireEye, Malwarebytes, Qualys Blog, OpenWrt, Slackware Linux, myhack58.com, ThreatPost, Ubuntu Linux, HackRead, OpenSSL, RedHat Linux, FreeBSD, ERPScan, Kaspersky Lab, Cent OS, ICS, Joomla!, F5 Networks, Arch Linux, PostgreSQL, CERT, Microsoft Vulnerability Research, SAINTexploit™, IBM AIX, Japan Vulnerability Notes |

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.