PRYTEK meetup: Breach and Attack Simulation or Automated Pentest? Last Tuesday, November 27, I spoke at “Business Asks for Cyber Attacks” meetup organized by PRYTEK investment platform. The event was held at the PRYTEK Moscow office in a beautiful XIX century building of a former textile manufactory.

The goal of the meetup was to talk about new approaches in Vulnerability Analysis and how they can reduce the Information Security costs for organizations.
There were two presentations:
- The first one was by Doron Sivan, Cronus CEO. He talked about his company’s product.
- The second was mine. I criticized traditional vendors of vulnerability scanners, talked about things that work in companies, and things that don’t work, and what you should pay attention to when choosing a Vulnerability Management tool.
For the most part this was my report from the last ISACA VM Meetup. The only difference was in the conclusions, since the topic of this event and the audience were different.
I stressed that the Attack Simulation tools, like Cronus, that analyze vulnerabilities and network connectivity of hosts can be very helpful. They allow you to assess the criticality of each vulnerability better and help to justify the need in prompt patching for IT Team (see “Psychological Aspects of Vulnerability Remediation“).
I mostly liked Doron Sivan’s speech. It’s always interesting to see how different companies sell the need in Vulnerability Management. According to vendor’s description, Cronus CyBot is a network agentless Vulnerability Scanner for infrastructure and web applications, that operates mainly in authenticated mode. It also analyses host connections and can produce attack path scenarios: potential ways that attacker can use to reach critical targets in the organization.
So, that’s why it can be called a Breach and Attack Simulation solution in terms of Gartner.
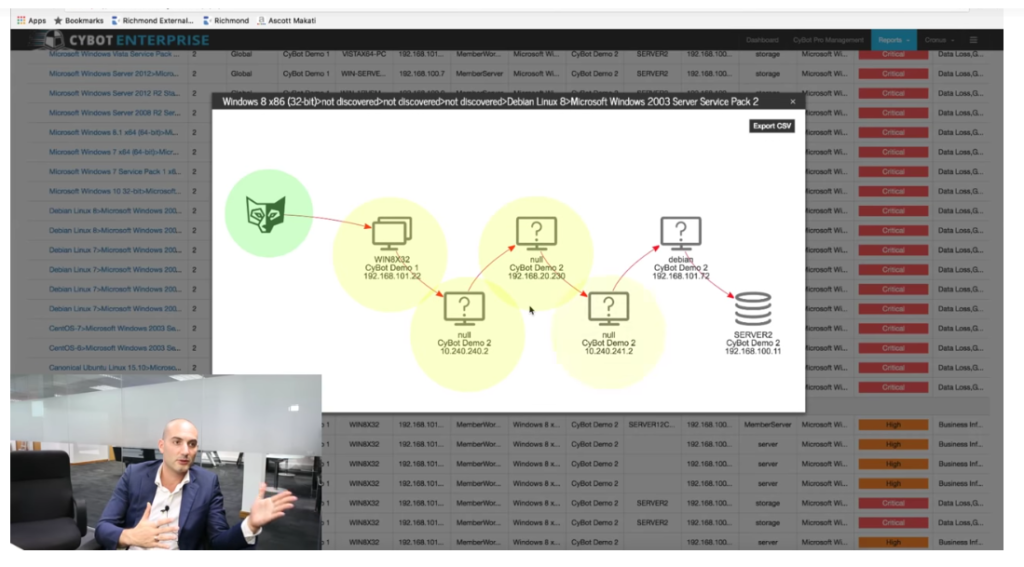
Screenshot from the video “Cronus Cyber Technologies: CyBot overview and demo“
It can also be integrated with Splunk, watch it on the video from “VB-Trend 2018 Splunk Conference” since 6:15.
The only thing I didn’t like was that Cronus was presented as Automated Pentest solution, as a “pentest that can be done every day”. And the price of the Cronus was compared with the price of traditional pentest.
I see a substitution of concepts here. Cronus doesn’t actually run the exploits on the host. So, it looks pretty much like traditional Vulnerability Management tool.
What are the features of Penetration Testing:
- Pentest is about the actual exploitation of vulnerabilities in a real environment. And if this exploitation does not occur, then this is not a pentest, even if this vulnerability has been tested somewhere in the laboratory.
- The goal of pentest is to find a chain of exploitable vulnerabilities in a particular limited scope. It can be the only one chain. It may not be directly related to technical vulnerabilities and include elements of social engineering for example. But it must be very clear and practical. Each step of penterster in the infrastructure requires an approve from the customer, because it can be dangerous.
Vulnerability Management, in it’s turn, is about regular and rapid detection of ALL existing vulnerabilities (even potential and theoretical), their analysis and remediation.
Vulnerability Management and Pentest are very different processes with very different goals, focuses and scopes, and they should not be mixed.
On the other hand, I certainly understand why it was presented in this way. It is very difficult for a new Vulnerability Management vendor to safe place on the market, and therefore it’s better to distance as much as possible from the competitors, positioning the solution as something completely new.
And it could really look like an analogue of pentest or as a framework for pentest, if the solution was a combination:
- Vulnerability Scanner (supported in Cronus)
- Host connectivity analysis (supported in Cronus)
- Exploitation module a la Metasploit (is NOT supported in Cronus)
- Automated profiling of the type and role of the host (most likely is NOT supported in Cronus)
In this case, I would have no more questions. I hope that they will develop in this direction.
NB. Vulnerability exploitation from the scanner is possible, for example, in ERPScan.
After the speeches there were many specific questions about Cronus. For example, we learned that it does not detect yet vulnerabilities in the third-party software for Windows (they plan to release this in January). There is no option to disable checks. You can choose IP scope, scheduling settings, infrastructure scan, choose a web or a web with injection scan. It turns out in the UK, you can not scan with an injection, even if the customer has allowed this.
To the credit of the event organizers, I was able to convey all my thoughts about the Cronus, as well as other criticism regarding the VM vendors. For such vendor-centric event this is very rare and valuable. And I think it created a more objective view of the solution and was useful for everyone. Thanks to the organizers for the great and interesting event!

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: CISO Forum 2019: Vulnerability Management, Red Teaming and a career in Information Security abroad | Alexander V. Leonov
Pingback: Настоящий Automated Pentest | Александр В. Леонов