First steps with Docker: installation in CentOS 7, vulnerability assessment, interactive mode and saving changes. Docker and containerization are literally everywhere. IMHO, this changes the IT landscape much more than virtualization and clouds. Let’s say you have a host, you checked it and find out that there are no vulnerable packages. But what’s the point if this host runs Docker containers with their own packages that may be vulnerable? Add to this the issues with complex orchestration systems, such as Kubernetes, completely different DevOps subculture with their own terms, slang, beliefs, priorities, and the situation begins to look like complete IT Hell. 🙂
But it seems that Docker will be here for a long time, so we will have to live with it. 😉 Here I will not write what Docker is and how it works. There are many publications about this. I personally interested in what actually we can do with these weird “virtual machines”, how can we run and assess them.
Installation
I created a CentOS 7 virtual machine “DockerHost” with 30GB HDD from minimal iso with Minimal installation profile. I configured network interfaces for Host Network and NAT using nmtui and then updated the host with yum upgrade.
The next step is to install docker. I use the official manual at docs.docker.com.
I go to the server:
$ ssh vmuser@192.168.218.5
vmuser@192.168.218.5's password:
Last login: Tue Mar 5 16:03:09 2019 from 192.168.218.4
[vmuser@localhost ~]$ su
Password:
[root@localhost vmuser]# I add the repository with docker-ce:
# yum install -y yum-utils device-mapper-persistent-data lvm2
# yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repoOutput:
...
repo saved to /etc/yum.repos.d/docker-ce.repoNow I can install Docker CE (Installed size: 241 M) and start it:
# yum install -y docker-ce docker-ce-cli containerd.io
# systemctl start dockerAnd finally testing docker installation by running hello-world image:
# docker run hello-world
Unable to find image 'hello-world:latest' locally
latest: Pulling from library/hello-world
1b930d010525: Pull complete
Digest: sha256:2557e3c07ed1e38f26e389462d03ed943586f744621577a99efb77324b0fe535
Status: Downloaded newer image for hello-world:latest
Hello from Docker!
This message shows that your installation appears to be working correctly.
To generate this message, Docker took the following steps:
1. The Docker client contacted the Docker daemon.
2. The Docker daemon pulled the "hello-world" image from the Docker Hub.
(amd64)
3. The Docker daemon created a new container from that image which runs the
executable that produces the output you are currently reading.
4. The Docker daemon streamed that output to the Docker client, which sent it
to your terminal.
To try something more ambitious, you can run an Ubuntu container with:
$ docker run -it ubuntu bash
Share images, automate workflows, and more with a free Docker ID:
https://hub.docker.com/
For more examples and ideas, visit:
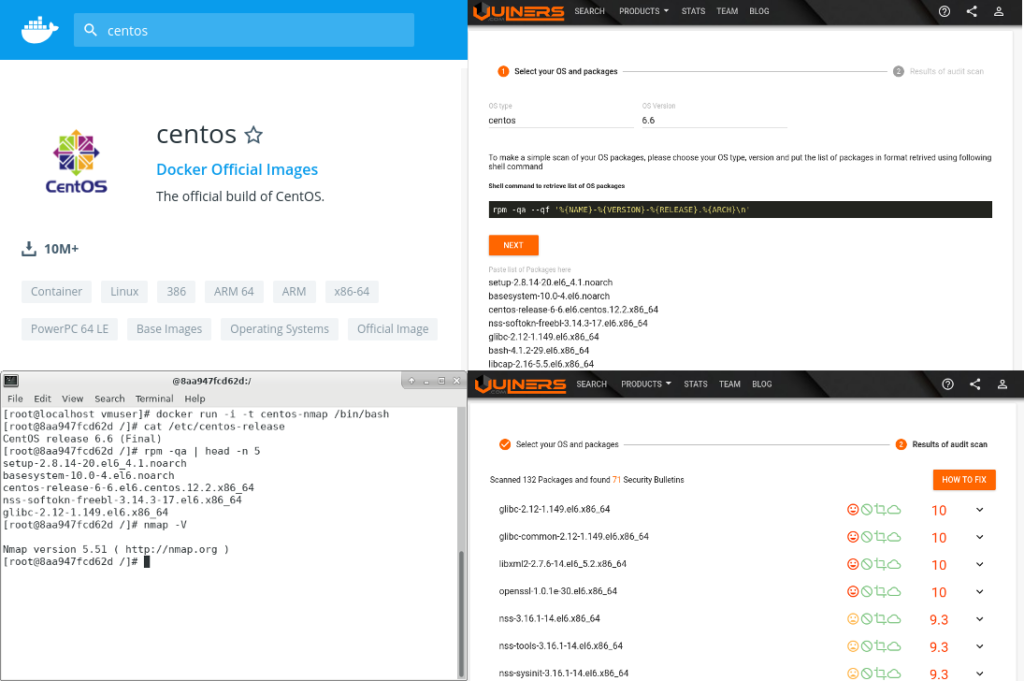
https://docs.docker.com/get-started/CentOS 6.6 image
Great! It works. I wanted to get something vulnerable, so I chose CentOS 6.6 image with minor version tags at the Docker Hub. These images DO NOT recieve updates as they are intended to match installation iso contents.

# docker pull centos:6.6So, now we will have these images:
# docker images REPOSITORY TAG IMAGE ID CREATED SIZE hello-world latest fce289e99eb9 2 months ago 1.84kB centos 6.6 4e1ad2ce7f78 4 months ago 203MB
NB. The image can be deleted with docker image rm -f fce289e99eb9
CentOS vulnerabilities
By default docker launches the container, executes some command and shuts down the container. For example, we can get version of the distribution and the list of installed packages:
# docker run centos:6.6 cat /etc/redhat-release
CentOS release 6.6 (Final)
# docker run centos:6.6 rpm -qa --qf '%{NAME}-%{VERSION}-%{RELEASE}.%{ARCH}\n'
setup-2.8.14-20.el6_4.1.noarch
basesystem-10.0-4.el6.noarch
centos-release-6-6.el6.centos.12.2.x86_64
nss-softokn-freebl-3.14.3-17.el6.x86_64
glibc-2.12-1.149.el6.x86_64
bash-4.1.2-29.el6.x86_64
libcap-2.16-5.5.el6.x86_64
...Status of the container:
# docker container ls -all
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c529711c4f4e centos:6.6 "rpm -qa --qf %{NAME…" 2 minutes ago Exited (0) 2 minutes ago wonderful_gangulyUsing this data we can get vulnerabilities at Vulners.com Audit (read more at “New Vulners.com services for Linux Security Audit and Vulnerability Alerting“):
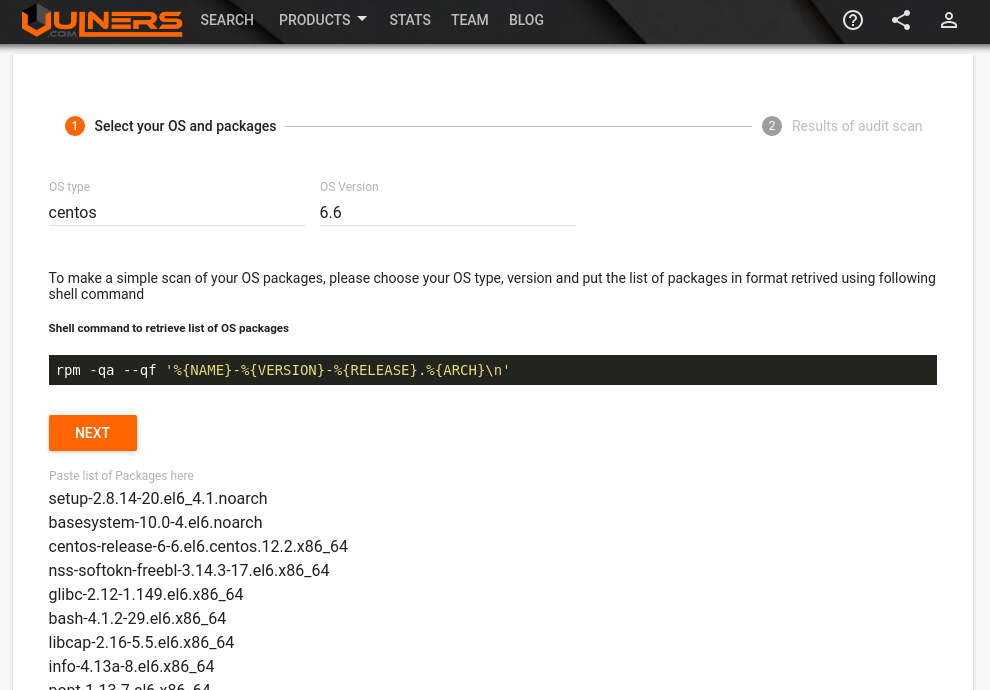
You need to input the packages and OS version and get the list of vulnerable packages and related vulnerabilities:
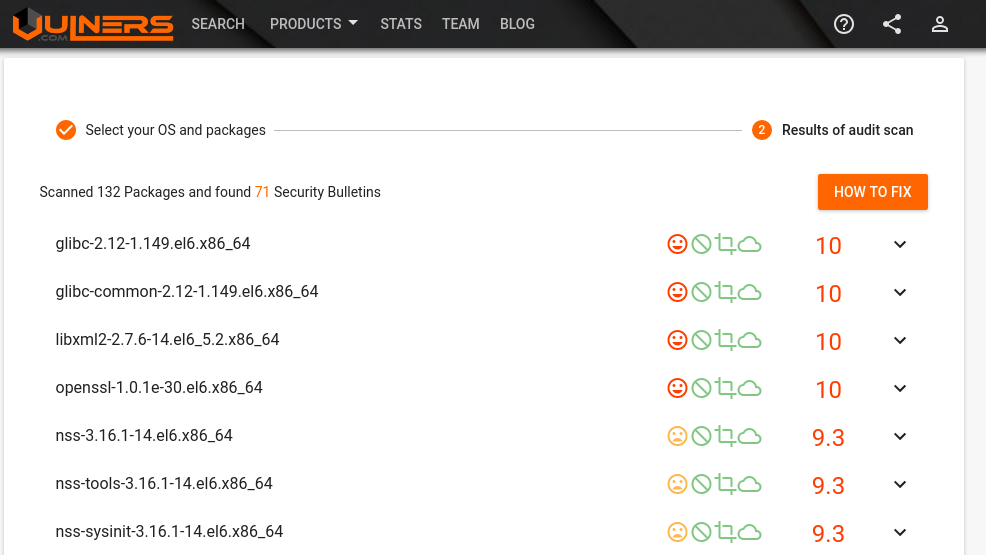
I tried to do it for python:3.7 and python:3.6.5 images and there was no vulnerabilities, because they are based on the latest Debian 9.
Interactive mode
We can also run docker container in interactive (-i) way with a terminal (-t):
# docker run -i -t centos:6.6 /bin/bash
[root@d0de0c4191b8 /]# ls
bin dev etc home lib lib64 lost+found media mnt opt proc root sbin selinux srv sys tmp usr var
[root@d0de0c4191b8 /]# cat /etc/redhat-release
CentOS release 6.6 (Final)
[root@d0de0c4191b8 /]# exit
exitChanging the image
But if you will install something to this container using yum, the changes won’t be saved. So, how to save it? There is a commit command for this.
# docker run -i -t centos:6.6 /bin/bash
[root@83d667883e99 /]# yum install nmap
...
[root@83d667883e99 /]# nmap localhost
Starting Nmap 5.51 ( http://nmap.org ) at 2019-03-06 01:41 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000070s latency).
Other addresses for localhost (not scanned): 127.0.0.1
All 1000 scanned ports on localhost (127.0.0.1) are closed
Nmap done: 1 IP address (1 host up) scanned in 0.07 seconds
[root@83d667883e99 /]# exit
# docker commit 83d667883e99 centos-nmap
sha256:40418e5db5daae6224899ef9e100665893ac28e96c0d7c58bfb5e7a0fad7af28Now we will have a new image:
# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
centos-nmap latest 40418e5db5da 8 minutes ago 261MB
hello-world latest fce289e99eb9 2 months ago 1.84kB
centos 6.6 4e1ad2ce7f78 4 months ago 203MBAnd we can run the commands in it:
# docker run -i -t centos-nmap /bin/bashl
[root@4391ff830aab /]# nmap -V
Nmap version 5.51 ( http://nmap.org )In conclusion
It became clear for me how to find vulnerabilities in docker images based on CentOS, Debian and Ubuntu. But it’s still and open question for me what should we do with images based on OS without Security Advisories, for example Alpine Linux. Next, I’m interested in how to use docker images to build Linux packages in the Packabit project and for hosting web applications, for example vulnerable ones.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
