PHDays VII: To Vulnerability Database and beyond. Last Tuesday and Wednesday, May 23-24, I attended PHDays VII conference in Moscow. I was talking there about vulnerability databases and the evolution process of vulnerability assessment tools, as far as I understand it.

But first of all, a few words about the conference itself. I can tell that since the last year the event got even better. I’ve seen lot of new faces. Some people I didn’t know, but they knew me by my blog and accounts in social networks. What a strange, strange time we live in! I was very pleased to see and to talk with you all, guys! 🙂
PHDays is one of the few events that truly brings all Russian community of security professionals together. I’ve seen people I have studied with in university, colleagues from the all places where I have been worked, and nearly all researchers and security practitioners that I follow. Big thanks for the organizers, Positive Technologies, for such an amazing opportunity!
It is also a truly international event. You can see speakers from all over the world. And all information is available both in Russian and English. Almost all slides are in English. Three parallel streams of reports, workshops and panel discussions were dubbed by professional simultaneous interpreters, like it is a United Nations sessions or something, recorded and broadcast live by the team of operators and directors. Final result looks really great.
Video of my presentation:
I was talking too fast and used some expressions that was hard to translate. The translator, however, did an awesome job. He is my hero! 🙂 If you didn’t understand something on video, I made a transcript bellow.
A version without translation for Russian-speakers is here.
Slides:
Unfortunately gif animation is not working in the Slideshare viewer.
Today I would like to discuss vulnerability databases and how vulnerability assessment systems has been evolving. Prior to discussing vulnerability databases I need to say that any vulnerability is just a software error, a bug, that allowing hacker to do some cool things. Software developers and vendors post information about such vulnerabilities on their websites. And there are tons and tones of vendors, and websites, and software products, and vulnerabilities.

If vendor’s approach to vulnerability accounting is proper, it goes to MITRE corporation to say: “look, vulnerability in my software product was identified, give me please an identifier for it”. So, it won’t be just a yet another RCE in Firefox, for example, but some CVE-2017-1234567. And you can refer to it in exploit databases and media publications, and CERTs will write about the importance of this very critical vulnerability.
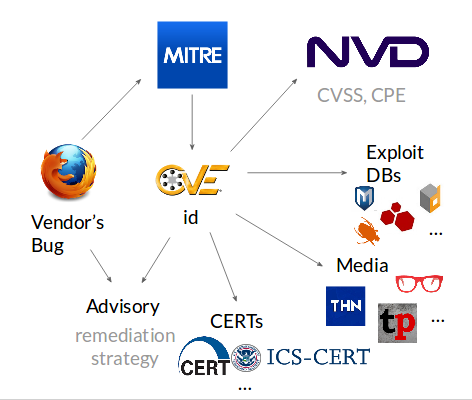
And so what should an ordinary security analyst do in this situation given that he or she is expected to protect some company. He or she needs to write tones of parsers to deal with all those sources, to put them into the database and somehow to analyze it with some scripts.
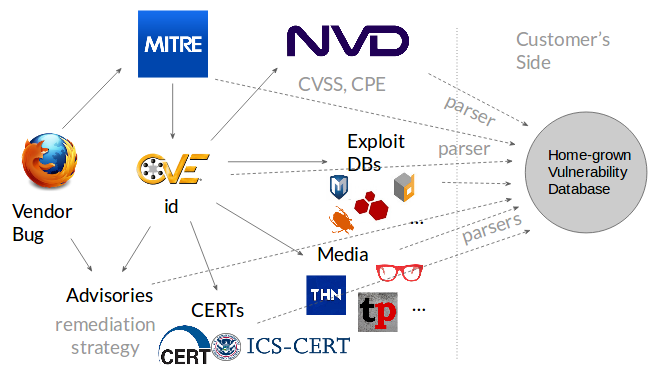
If there is such a need, that for sure will be commercial offers to satisfy it. They will have the same parsers that will collect the data, put it into the database and somehow offer it to the users. And it won’t be just some files that customer can download. Vendor comes to the costumer and ask: “what functionality you need to use our database at ease”?
- They may need, for example, a search engine, to search vulnerabilities in Google-style. And so we get a Vulnerability Search Systems.
- However, it’s not cool to look for vulnerabilities manually. We may want to enter search query once and get new results as soon as they will appear in the database. And so we will get a Vulnerability Notification Service.
- Customer may say, that they don’t fully understand what they want or need.Why you just show us those critical things on your own. And here we are with Vulnerability Intelligence Service, whatever it might mean.
- It would be also great if this vulnerability data could be integrated with other Enterprise systems. And here we are with API for vulnerability database.
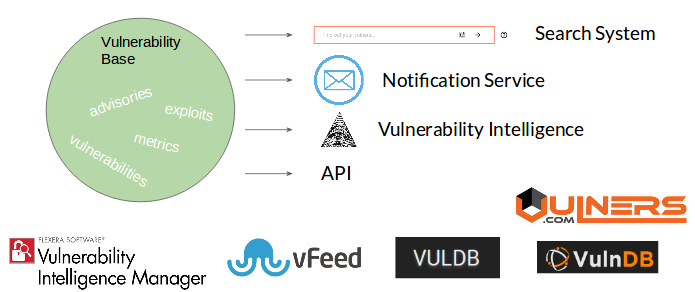
There are plenty of such databases:
I prefer Vulners.com because it contain security objects of different type and nearly all functionality is free. You can retrieve all of the database free of charge!
But we can go even further. User may come to a Vulnerability Base developer and say: “it’s not enough for us to see this vulnerabilities in the world, we want to see vulnerabilities that exist in our particular infrastructure”.
- Vendor would say I can arrange detection rules for SOME PART of vulnerabilities and make transports that will get information from the hosts. And here we are with Vulnerability Scanner, like Nessus and OpenVAS.
- And then Vendor may add all those dashboards, task trackers and call this a Vulnerability Management solution, like Qualys Cloud Platform and Tenable SecurityCenter.
- Vendor may also add some context, criticality of assets ans so on, and we get Threat/Risk Management solution, like Skybox Security products.
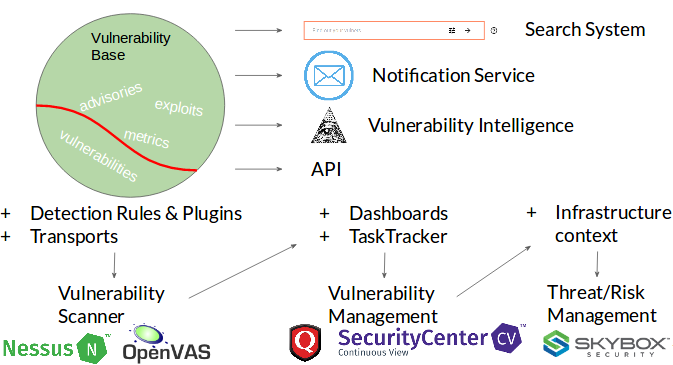
But we should not forget that it’s still a Vulnerability Database. And when you are looking to purchase a solution to deal with vulnerabilities:
- Make sure that your solution knows as many vulnerabilities as possible.
- You should always know what is in there, and (much more important!) what is not. And why.
- You should understand what can be detected automatically, and (much more important!) what can’t be detected automatically. And in what mode it could be detected: during authenticated scan, unauthenticated scan, by agents, using some for form of integration with third-party systems, etc.
- If anything could be detected automatically, you should know about frequency of detection plugins updates.
NB: Vulnerability Management solution is a critical asset of any organization and a great goal for an attacker. It stores credentials for authenticated scanning, it has access to any host, firewall ignores scanning activity from this system. That’s it must be carefully protected. I highly recommend an awesome report by Oleksandr Kazymyrov “Jumping from Tenable’s SecurityCenter CV to production environments” presented on the same PHDays VII conference. He showed nearly all weaknesses of SecurityCenter and how hackers could use it in attacks on your organization. Very inspiring! And most of the ideas are relevant for Vulnerability Management solutions of other vendors.
The main task of any Security Analyst in any company is to know at all times what systems may need patching. For this task no scanner may be required. You may just get information about update from some source on a regular bases, some subscription service. Read more about it at my post “Vulnerability subscriptions in terms of business“.
Subscriptions may even work better than a Vulnerability Scanner. For example, if your organization use some Linux software installed from the sources or from self-built packages with some non-standard versions, Vulnerability Scanner (Nessus, OpenVAS, Qualys, etc.) will not detect vulnerabilities of this software correctly. But if I know when the software was updated last time by our IT guys, for example 2017-01-01, I can easily get vulnerabilities in this software since this date:
published:[2017-01-01 TO 2100-01-01] AND type:centos AND title:openssh
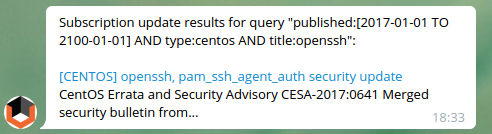
And I can subscribe to a new vulnerabilities using vulnersBot (read more about it at “New vulnersBot for Telegram with advanced searches and subscriptions“):
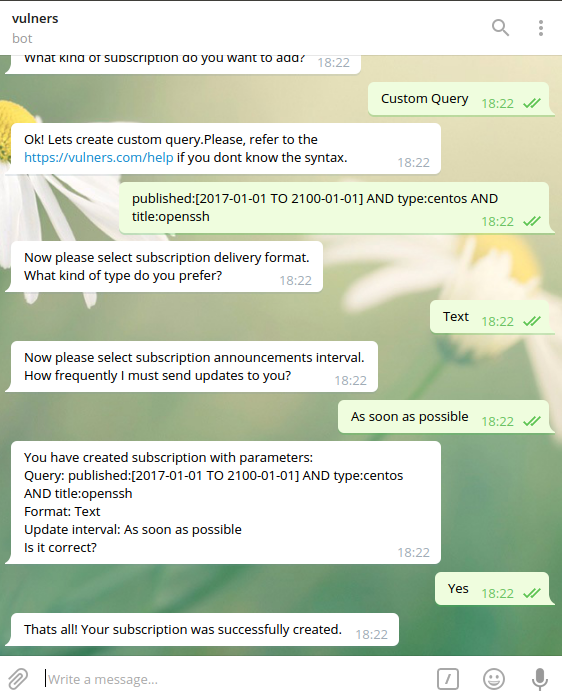
And get new results as soon as they will appear on Vulners.com
The next big question how to distinguish important and not important vulnerabilities. Actually this part is about my concept of Vulnerability Quadrants. You can read more about them and watch the video in “Vulnerability Quadrants” post.
The only new example I added for this event was for WannaCry SMB v.1 Vulnerability:
Here you can clearly see that the vulnerability is not particularly dangerous. Well, how can dangerous can be a vulnerability, for which a patch was available immediately. And you can also see media madness that began with epidermic of WannaCry ransomware since May 12. Read more and see the video in “WannaCry about Vulnerability Management” post.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.


Hi Alexander,
nice post. Thank you. May I ask you to advise what is most best framework for managing corporate vulnerability database and lifecycle of vulnerabilities from different resources (scanners, open databases, etc)?
Does this solution exist? Or its still need to use bunch of scripts and maintain your own local db?
Pingback: ZeroNights 2017: back to the cyber 80s | Alexander V. Leonov
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov