Psychological Aspects of Vulnerability Remediation. In my opinion, Remediation is the most difficult part of Vulnerability Management process. If you know the assets in your organization and can assess them, you will sooner or later produce a good enough flow of critical vulnerabilities. But what the point, if the IT team will not fix them?
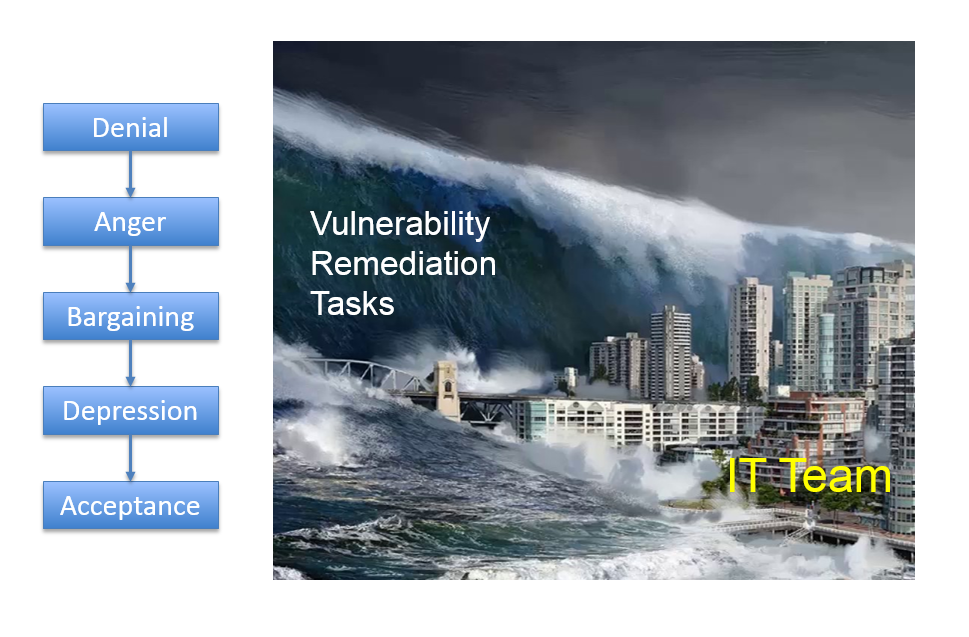
Kübler-Ross model and Tsunami of Vulnerability Remediation Tasks
Just think about it. The only thing that your colleagues from IT team see is an unexpected tsunami of the patching tasks. They most likely don’t understand WHY they should do it. They most likely don’t know about the concepts of Attack Surface minimization and Attack Cost maximization. From their point of view it’s just some stupid requirements from InfoSec team imposed with only one goal – to make their life miserable.
So, they may think that denial and pushing back can solve all their problems. And, frankly, this may work. There are countless ways to sabotage Vulnerability Remediation. Most main and common are the following:
- I don’t understand how to patch this.
- I already patched this, there should be a false positive in the scanner.
- Why should we patch this? The vulnerability is not exploitable. Or it is exploitable in theory, but not exploitable in our particular infrastructure. Or this server is not critical and, even if it will be compromised, there won’t be a huge impact. So, we will not patch it.
In each individual case Vulnerability Analyst can describe and proof his point, but doing this for each vulnerability will require insane amount of time and efforts and will paralyze the work. It is basically the Italian strike or work-to-rule.
So, keep it in mind and try to distinguish the cases where your colleagues really don’t understand something or your Vulnerability Prioritization is not good enough and the cases when they start to deceive you.
When the problem is on your side
It’s relatively easy to deal with. You should invest more efforts in Vulnerability Analysis and develop the criteria for what you think are the most critical vulnerabilities. It’s not a good idea to give your IT a raw Vulnerability Scanning reports just filtered by CVSS. 😉 You should also produce the Remediation tasks that will be convenient for the IT team. But this is for another post.
When the problem is on the side of IT
It’s much harder. In this case there are two main strategies:
Strategy 1. Keeping things formal
This way seems quite convenient for me personally. 😉 If something does not work in the organization, we need new policies and the ways to control them:
- Create a Patch Management and Vulnerability Management policies and set the KPIs
- Enforce policies and KPIs in the organization
- Create the metrics
- Produce regular reports
- If the IT team don’t make their work well, escalate the issue
Unfortunately in the real organization this most likely will not work. 🙁 People are not the robots, you know. They don’t like pressure. Especially when it is formal and comes from some “external” part of the organization. It may even look like some kind of disrespect. As I wrote earlier, there are numerous ways to sabotage the process. So, your very active and aggressive position may just create a toxic environment in which you won’t be able to do anything.
Strategy 2. Maximum cooperation
The idea is to show your competence to the IT team and to describe the risks related to unpatched vulnerabilities.
- Try to stand by their side and help them establish effective and automated Patch Management and Security Hardening process.
- Try to convince them that Vulnerability Management process is not a threat. That it can proof that IT team makes a great job.
- Try to convince them that InfoSec can actually help IT team to get more resources (software and people) for remediation tasks. Because only InfoSec truly understands how critical and how hard this job is.
However, if you will be playing too much on IT side, there is a chance that they will start to deceive you. They will not do their part of the job and therefore Vulnerability Management process in organization will fail.
The Art of the Deal
As you can see, there is no universal solution that will work in any case. It’s necessary to understand the current situation:
- When it’s time to be formal and to be informal.
- When you need to push and argue, and when it’s time to agree and fall back.
- When it’s time to escalate the issue.
Basically, to do this right, you need to understand the people, to be a good manager, psychologist and negotiator.
I have seen very few people, who had all this qualities and where also interested in the technical stuff. And, unfortunately, I have seen lot’s of examples when the lack of communication skills among technical specialists lead to absolutely unnecessary conflicts.

In my opinion, it’s much more comfortable situation when technical specialists (practitioners) do their part of job – detect vulnerabilities and make the automation and specialists with great soft and management skills make principal negotiations and set the policies to implement.
Common Recommendations
Implementation of Vulnerability Remediation is a long a hard process (usually all the stages from Denial to Acceptance). It can stuck anywhere, and cause lots of stress for anyone who involved. It’s normal. And this what I always recommend to anyone, especially to myself:
- Don’t take it too personally and emotionally, it’s just a job.
- Stay extremely polite and respectful in any situation. It really helps to soft the corners.
- It’s better to discuss sensitive issues face to face. Everything that is written is much easier to misinterpret.
- However, it’s crucial to keep all mutual agreements in a written form. Chat logs are better than nothing, email messages are better than chat logs, tasks in the task tracker are better than emails.
- Even if you are 100% sure that colleagues treat you badly and constantly deceive you, there is still a chance it is some kind of misunderstanding and you can work it out. Maybe you don’t know something important that your colleagues know or you don’t have some specific experience that they have. Sometimes it’s about the cultural differences, communication style, sense of humor, etc. People are usually better than they seem.
- Of course, there also a chance that you work with some really bad, rude, ignorant and lazy people, who just don’t want to do their job. If it is really true, than Vulnerability Remediation is not the biggest problem of the organization (and yours as well).
So stay calm and try to do your best.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Great article. These are real facts when it comes to dealing with your IT.
Pingback: ISACA Moscow Vulnerability Management Meetup 2018 | Alexander V. Leonov
Pingback: PRYTEK meetup: Breach and Attack Simulation or Automated Pentest? | Alexander V. Leonov
Pingback: What’s wrong with patch-based Vulnerability Management checks? | Alexander V. Leonov
Pingback: MIPT/PhysTech guest lecture: Vulnerabilities, Money and People | Alexander V. Leonov
Pingback: No left boundary for Vulnerability Detection | Alexander V. Leonov
Pingback: AM Live Vulnerability Management Conference 2022: my impressions and position | Alexander V. Leonov
Pingback: Поделюсь свежими впечатлениями после мероприятия Код ИБ Безопасная Среда "Управление уязвимостями" | Александр В. Леонов