Automated posting on Vkontakte public pages using VK API and Python. Vk.com (Vkontakte) is the most popular social network Russia and Ex-USSR with 430+ million users. Traditional advantages of vk.com – huge amount of free music and video. The service allows users to upload and share files and for a long time was quite tolerant to piracy. In 2016 Mail.Ru Group, Vkontakte parent company, has solved all problems with major music labels and now works closely with the rights holders.
VKontakte has very efficient features for creating communities: public pages (blogs) and groups (open and closed web-forums). In VK communities you can easily share news, photo, audio, video, text files in different formats, create discussions topics and wiki-pages. When I was studying at the University in 2003-2009, to share information in a study group we needed to create our own website and phpBB-based forum. Now practically all students simply use VKontakte groups for this. VKontakte shows all content in groups as is, without hiding and filtering.
With reach automation capabilities, you can do various interesting things based on VK. For a start, I decided to post all annotations from my https://avleonov.com blog to https://vk.com/avleonovcom Vkontakte page. I created this page in web GUI and filled it with content automatically using my own python scripts.
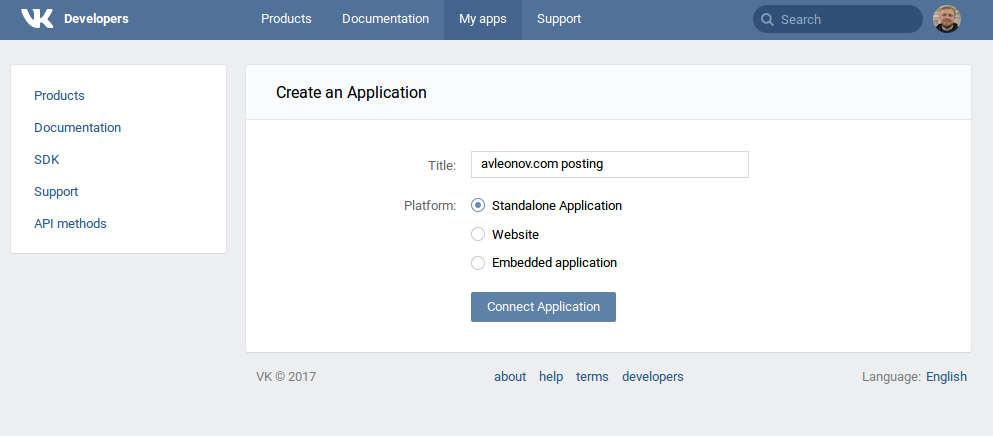
Creating a new application
I want to work with Vkontakte from my Python scripts. So, I will need to create a new Standalone Application for this. You can do it here: https://vk.com/editapp?act=create
Upd. March 2018 Integration with Vkontakte suddenly broke, because they added mandatory version parameter to all calls.