Crypto AG scandal. The article in The Washington Post is really huge, but even a brief glance is enough to see how absolutely amazing this Crypto scandal is. A great example of chutzpah. ?
“Crypto AG was a Swiss company specialising in communications and information security. It was jointly owned by the American CIA and West German intelligence agency BND from 1970 until about 2008. … The company was a long-established manufacturer of [backdoored] encryption machines and a wide variety of cipher devices.”
“You think you do good work and you make something secure,” said Juerg Spoerndli, an electrical engineer who spent 16 years at Crypto. “And then you realize that you cheated these clients.”
¯\_(ツ)_/¯
Now the causes of hysteria around Kaspersky and Huawei become more clear. It is natural to suspect others in the things you practiced yourself.
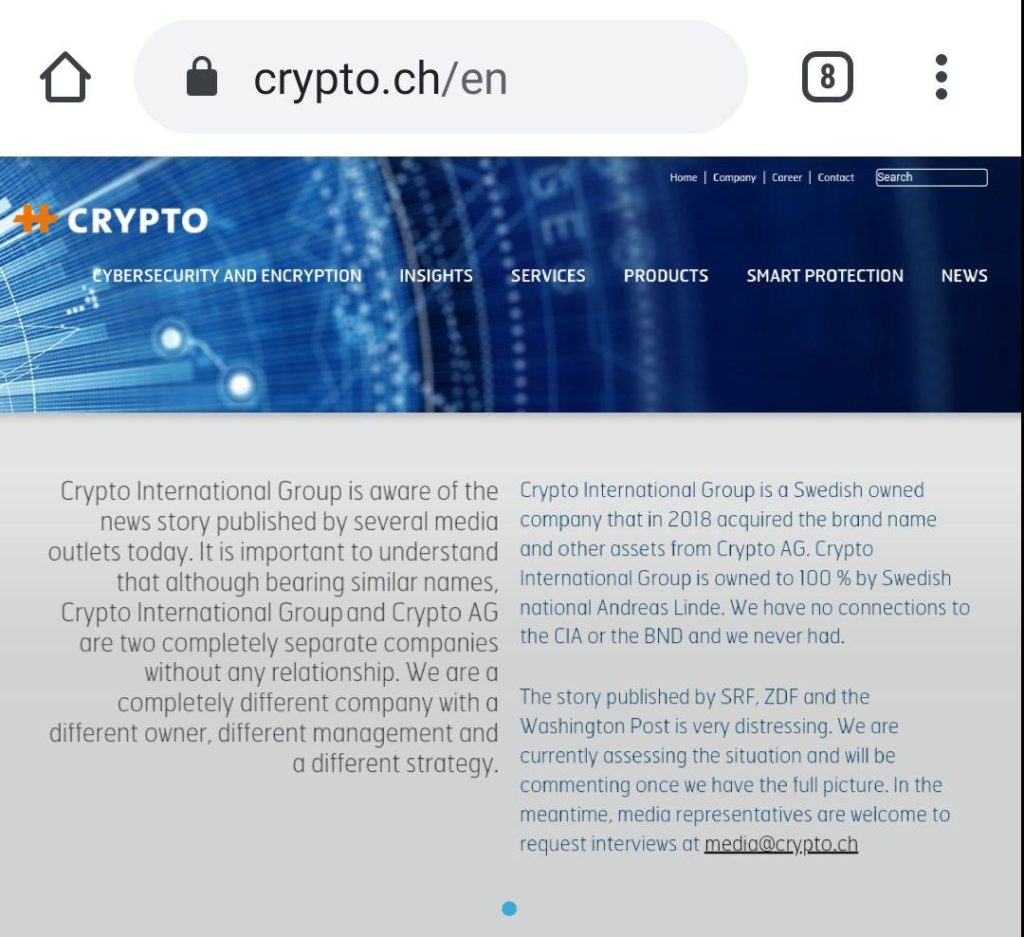
And note the disclaimer on the Crypto’s website. A completely different company, with a different strategy. ☝️? Okaaay…