Retrieving scan results through Nessus API. In this first article about Nessus API I want to describe process of getting scan results from Nessus.
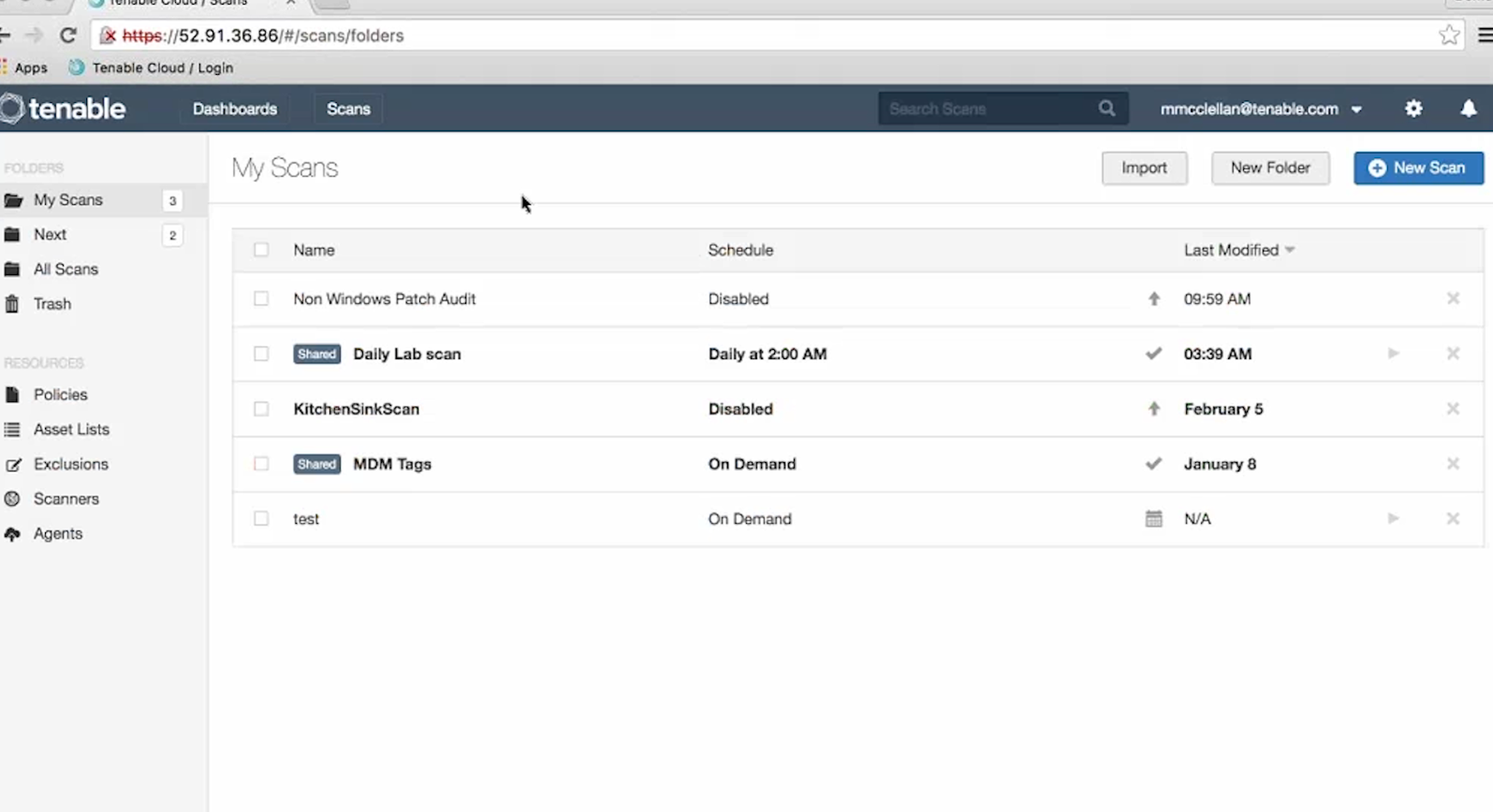
Of course, it’s also great to create and run scans or even create policies via API. But to be honest, in practice, you may need this functionality rarely. And it’s easier to do it manually in GUI. On the other hand, sometimes it very efficient to create automatically some specific scan task for specific group of hosts using existing (inventory) scan results. But we will talk about this topic next time (Upd. I wrote post about scan creation “Nessus API for hosts scanning“).
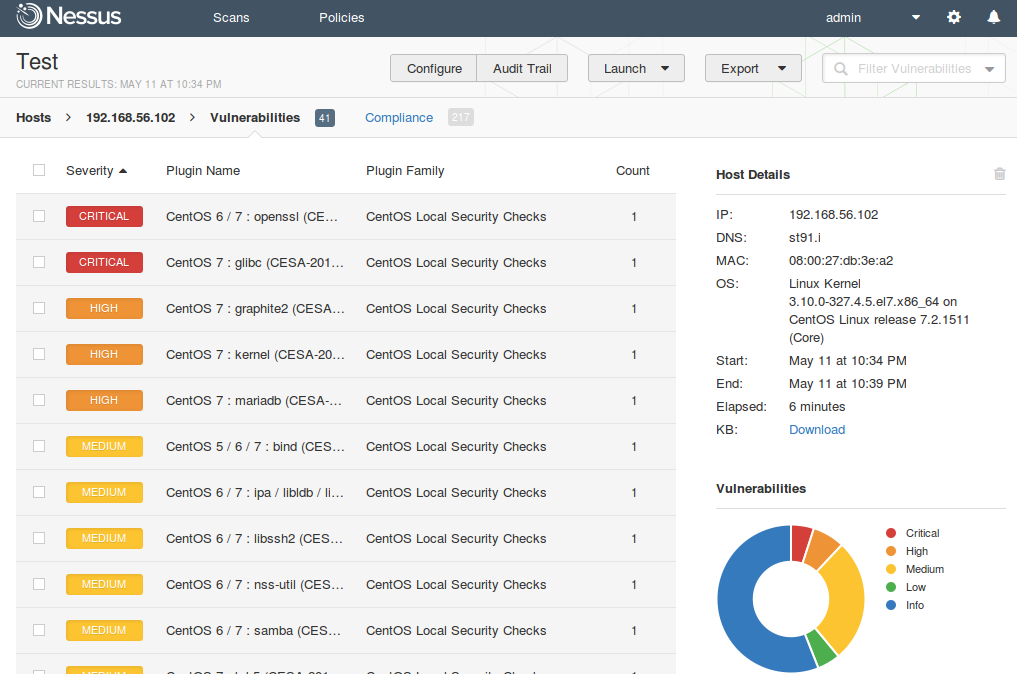
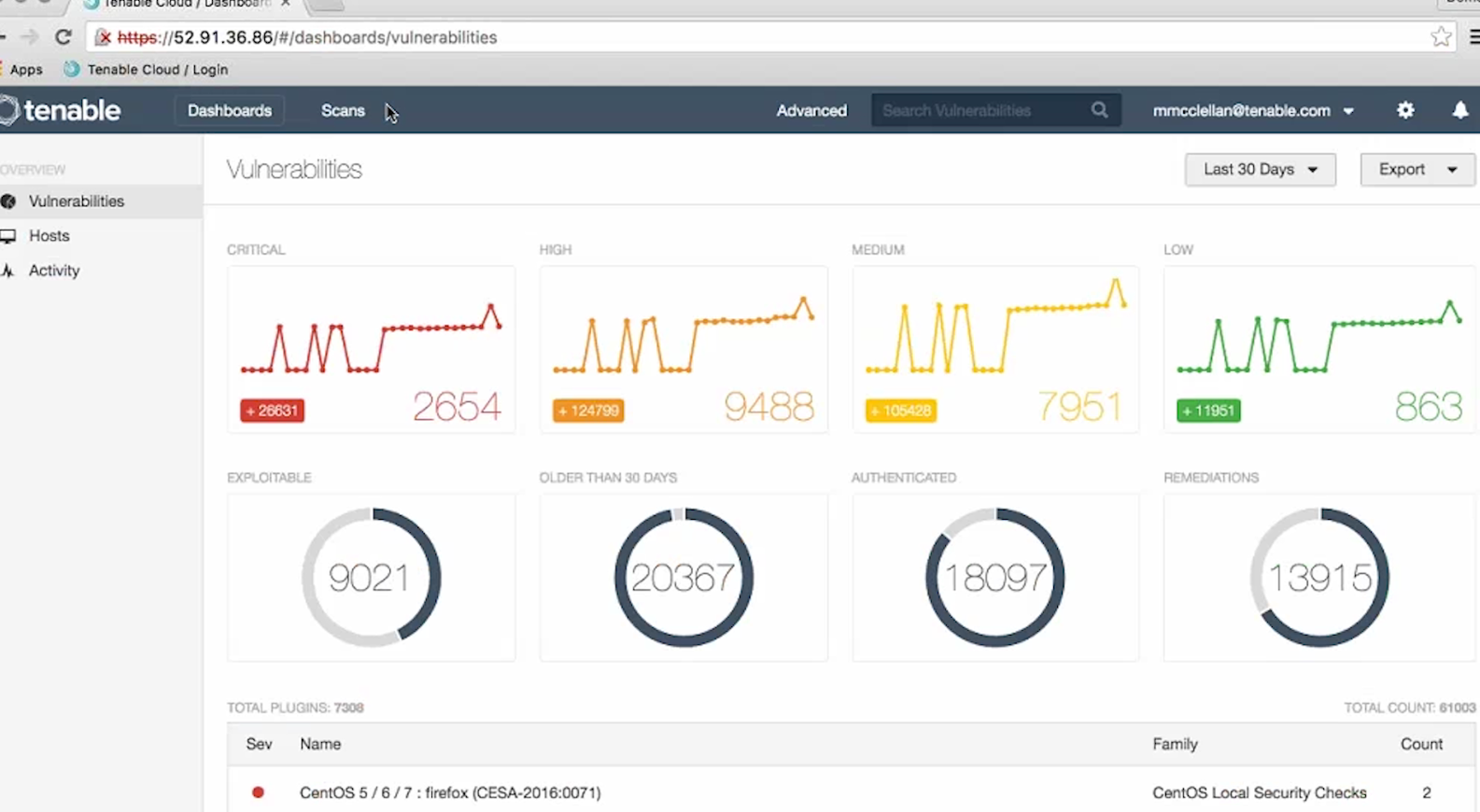
Now, imagine that we have configured regular Nessus scans. And we want to get this scan results on a regular basis to make some analysis and maybe create some tickets in Jira.
As usual, I will use curl for all examples, because it is easy to read and easy to test in any Linux terminal.
Starting from Nessus v.6 the API manual is built in GUI: https://<scanner_ip>:8834/api#
Continue reading