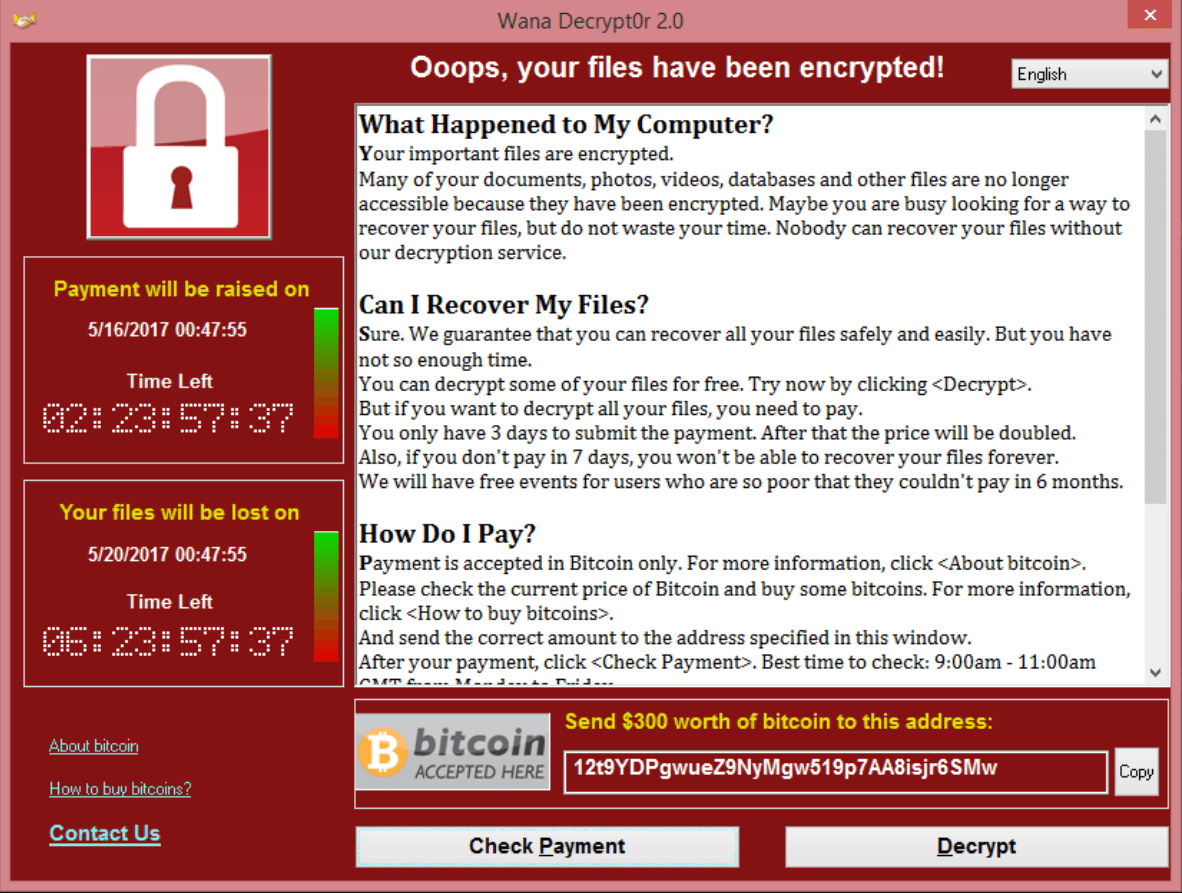
Is it possible to detect Zero Day vulnerabilities with Vulnerability Management solutions? Hello everyone! In my English-language telegram chat avleonovchat, the question was asked: “How to find zero day vulnerabilities with Qualys?” Apparently this question can be expanded. Not just with Qualys, but with any VM solution in general. And is it even possible? There was an interesting discussion.
Alternative video link (for Russia): https://vk.com/video-149273431_456239109
Image generated by Stable Diffusion 2.1: “calendar on the wall cyber security vulnerability zero day”
The question is not so straightforward. To answer it, we need to define what a Zero Day vulnerability is. If we look at wikipedia, then historically “0” is the number of days a vendor has to fix a vulnerability.
“Eventually the term was applied to the vulnerabilities that allowed this hacking, and to the number of days that the vendor has had to fix them.”