Vulnerability scanners: a view from the vendor and end user side. Original article was published in Information Security Magazine #2, 2016 (in Russian)
Vulnerability scanner is a computer program or hardware appliance designed to detect security problems on hosts in computer network. What kind of problems? Well, problems that may occur if some critical security updates were not installed on time or the system was not configured securely. In practice, this situation often occurs and it makes hacking the systems easy even for inexperienced attacker.
If it is all about checking, maybe it’s possible to do it manually? Yes, sure, but it requires a lot of specific expertise, accuracy and time. That’s why vulnerability scanners, which can automate network audit, have become standard tools in the arsenal of information security experts.
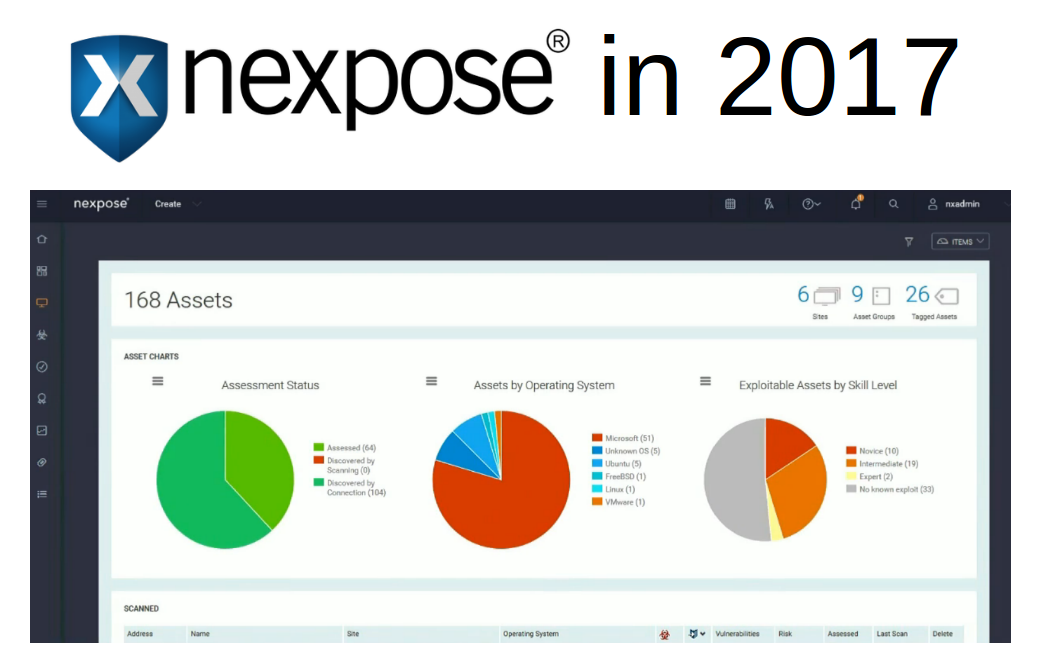
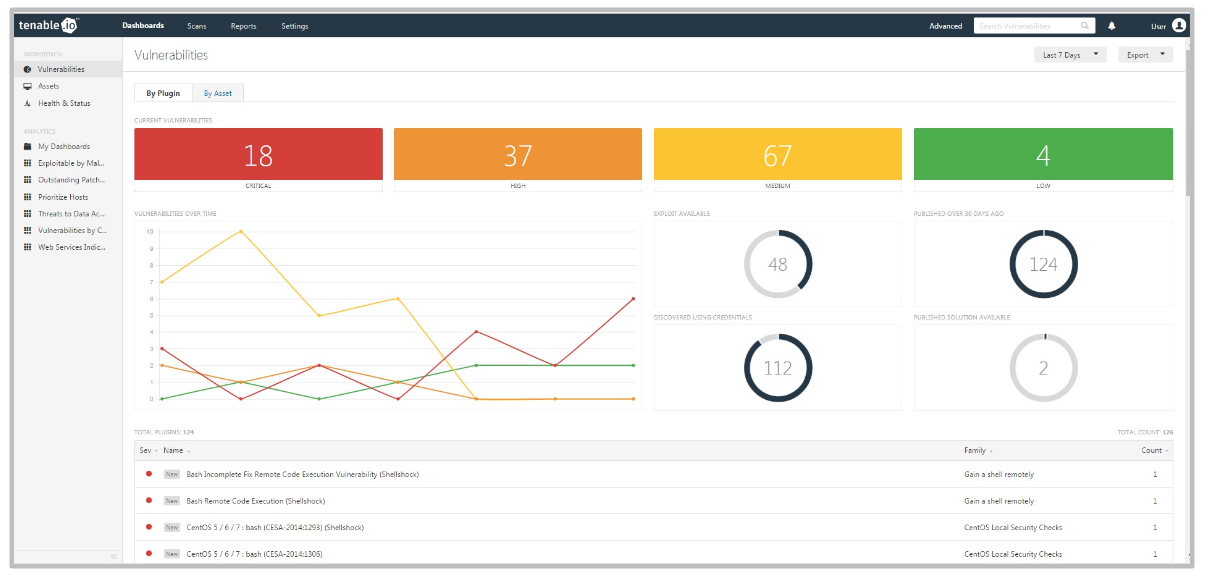
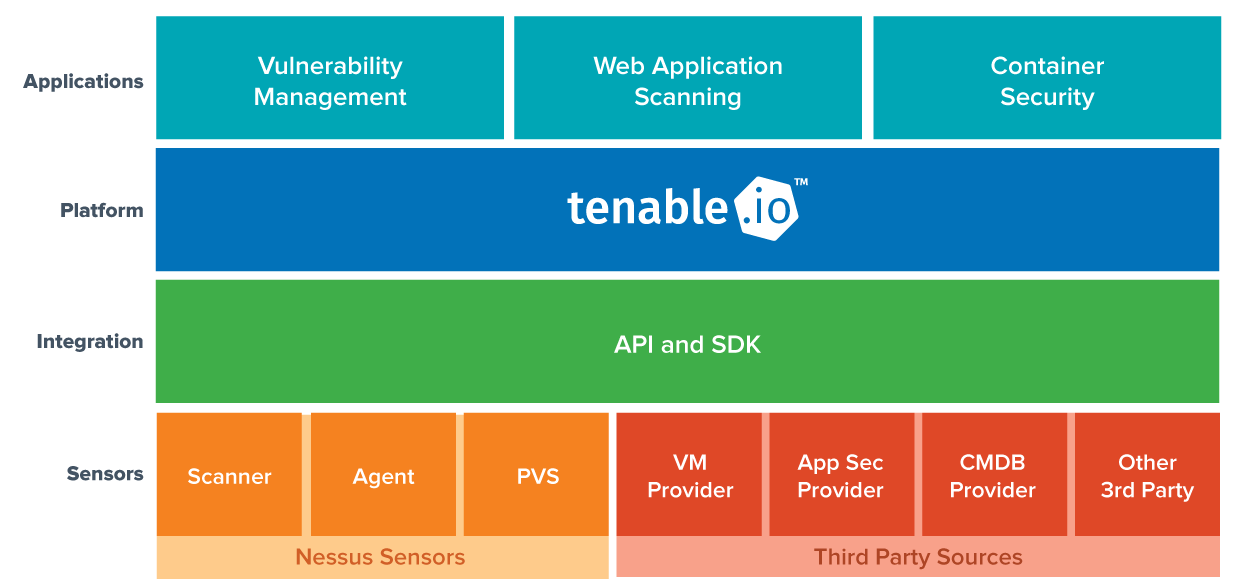
I worked for a long time in the development department of well-known vulnerability scanning vendor and was making a lot of competitive analysis as well. At current time, I use vulnerability scanners as an end user. So, in this article I will try to look at the main problems of this class of products from the vendor and from the end user side.
How vulnerability scanner detects vulnerabilities?
Detection methods are usually well known and uncomplicated: vulnerability scanner somehow detects software version installed on a host. If version is less then secure version of this software (known from the public bulletin) – vulnerability exists and the software should be updated. If not – everything is ok. As a rule, vulnerability scanners try to guess installed versions by opened ports and service banners, or scanner may just have a full remote access to the host and able to perform all necessary commands (it is the most accurate and effective way).
Continue reading →