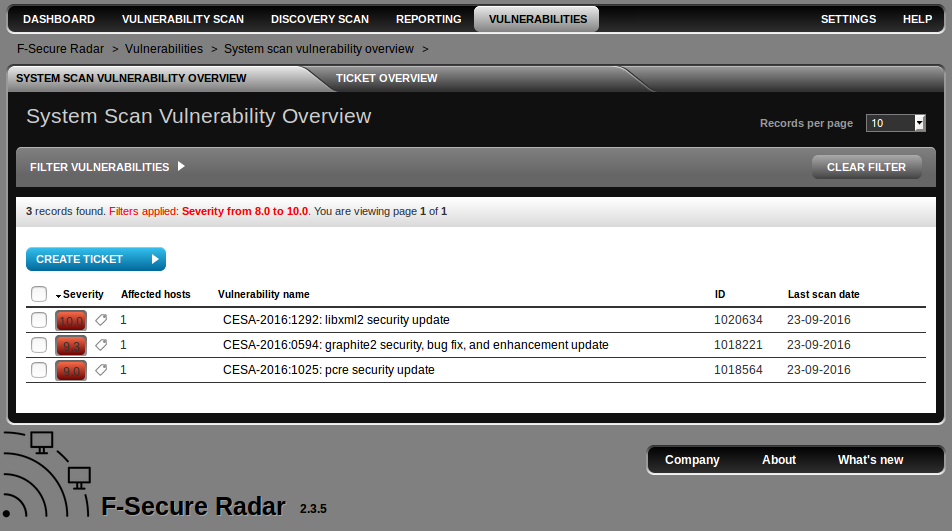
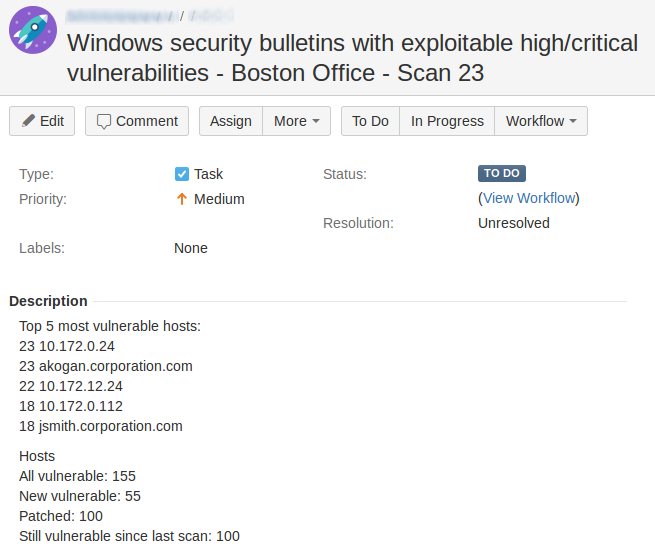
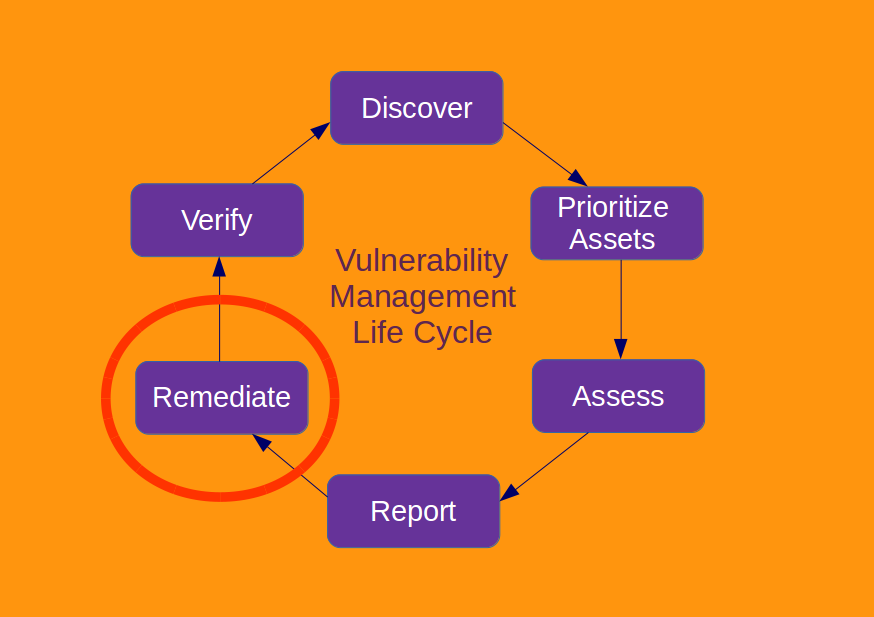
Vulnerability Management vendors and Vulnerability Remediation problems. It’s not a secret, that Vulnerability Management vendors don’t pay much attention to the actual process of fixing vulnerabilities, that they detect in the infrastructure (Vulnerability Remediation). Although it seems to be the main goal of VM products: to make vulnerabilities fixed and whole IT infrastructure more secure, right?
In fact, most of VM vendors see their job in finding a potential problem and providing a link to the Software Vendor’s website page with the remediation description. How exactly the remediation will be done is not their business.

The reason is clear. Remediation is a painful topic and it’s difficult to sell it as a ready-made solution. And even when Vulnerability Vendors try to sell it this way, it turns out pretty ugly and does not really work. Mainly because the Remediation feature is sold to the Security Team, and the IT Team will have to use it.