High-Tech Bridge service and API for SSL/TLS server testing. Another great free SSL security testing service — High-Tech Bridge SSL Server Test (and Free API). I have already reviewed something quite familiar – Qualys SSL Labs client. So naturally there will be an element of comparison.
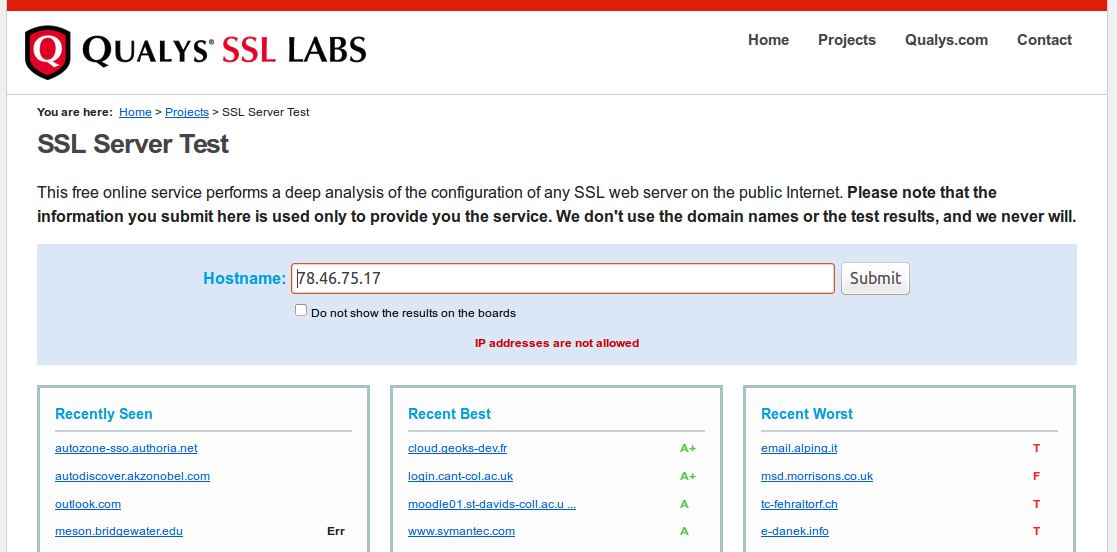
Why have I tried something else after Qualys SSL Labs? The thing is Qualys doesn’t support IP addresses as a target. Maybe they don’t want it to be used for assessing full IP-ranges. I don’t know. But the fact is “IP addresses are not allowed”.
With High-Tech Bridge you can set an IP address or domain name as a target.
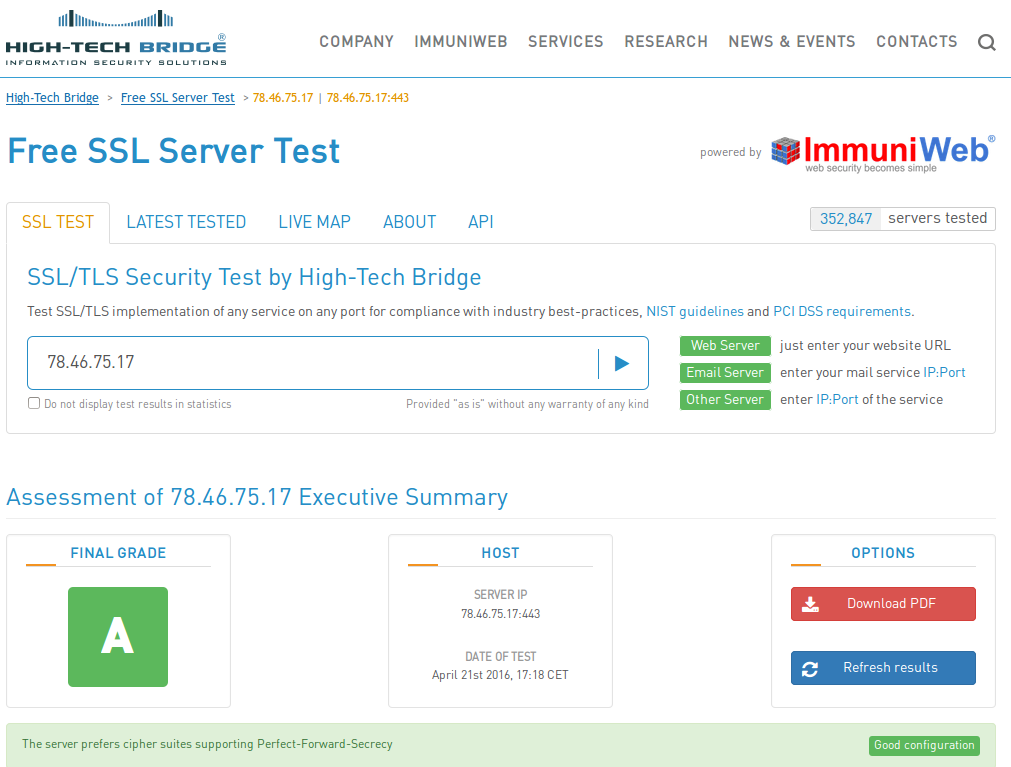
With High-Tech Bridge you can scan only 20 requests in 3 minutes and 250 requests in total per 24 hours, from one IP address. Qualys client does not have such restrictions.
In the other hand, when you work with Qualys API, you need to get an API key or work with official client (as I did) and have some legal restriction. You can use API for non-commercial purposes only and can’t use it in services and products that will somehow compete with SSL Labs. What about High-Tech Bridge? “License notice: The API is provided for free both for private and commercial purposes. If you use the API for publicly available service (commercial or not) a link to High-Tech Bridge’s Free SSL Server Test is mandatory.” Just a link. And API key is not required. Anyway, both services is quite good and free, so decide for yourself, what is most suitable for you, or use them simultaneously for more complete and accurate results.
Another fun difference in processing domains that are resolved into several IPs. You should send first request with domain name. Get some reply. Than you should send several requests for every IP using token you from the reply. “In order to prevent abuse, a protection mechanism has been set up to remove the ability to test IPs that are not related to tested domain name.” What the sense if I actually can set any IP as a target? Anyway, Qualys makes makes one report for all domain IPs with one request.
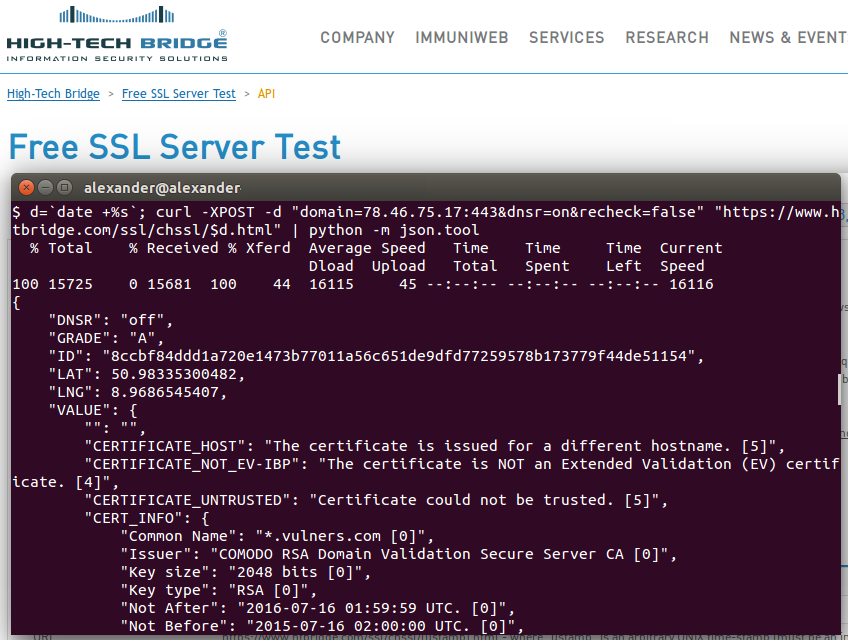
Let’s scan the host by IP with High-Tech Bridge SSL Server API:
d=`date +%s`; curl -XPOST -d "domain=78.46.75.17:443&dnsr=on&recheck=false" "https://www.htbridge.com/ssl/chssl/$d.html" | python -m json.tool
As you see, you should send POST request to the strange URL with unix timestamp https://www.htbridge.com/ssl/chssl/[ustamp].html. “Such construction is done to prevent caching on client side.” Hmm… Ok.
Anyway, API is very well described at https://www.htbridge.com/ssl/#api.
domain:port must be a valid domain name, or IP address, followed by a port number. If port is not supplied, 443 is used by default.
dnsr “on” means that test results will be displayed in statistics, “off” means that test results will be hidden. …
recheck “false” will use results from cache if the server has been tested within the past 24 hours, “true” will perform a new test without looking at the cache.
In reply you will get JSON structure.
I pay attention to:
- GRADE
- INSECURE_SITE_NOHTTPS
- CERTIFICATE_EXPIRED
- CERTIFICATE_UNTRUSTED
- “Not After” in CERT_INFO
- ALL with “CVE-” — vulnerabilities: OpenSSL CCS flaw, POODLE, Heartbleed, etc.
Full results:
{
"DNSR": "off",
"GRADE": "A",
"ID": "8ccbf84ddd1a720e1473b77011a56c651de9dfd77259578b173779f44de51154",
"LAT": 50.98335300482,
"LNG": 8.9686545407,
"VALUE": {
"": "",
"CERTIFICATE_HOST": "The certificate is issued for a different hostname. [5]",
"CERTIFICATE_NOT_EV-IBP": "The certificate is NOT an Extended Validation (EV) certificate. [4]",
"CERTIFICATE_UNTRUSTED": "Certificate could not be trusted. [5]",
"CERT_INFO": {
"Common Name": "*.vulners.com [0]",
"Issuer": "COMODO RSA Domain Validation Secure Server CA [0]",
"Key size": "2048 bits [0]",
"Key type": "RSA [0]",
"Not After": "2016-07-16 01:59:59 UTC. [0]",
"Not Before": "2015-07-16 02:00:00 UTC. [0]",
"Organization Unit": "EssentialSSL Wildcard [0]",
"The Certificate Signature Algorithm": "sha256WithRSAEncryption [0]",
"authorityInfoAccess": "CA Issuers - URI:http://crt.comodoca.com/COMODORSADomainValidationSecureServerCA.crt OCSP - URI:http://ocsp.comodoca.com [0]",
"authorityKeyIdentifier": "keyid:90:AF:6A:3A:94:5A:0B:D8:90:EA:12:56:73:DF:43:B4:3A:28:DA:E7 [0]",
"basicConstraints": "CA:FALSE [0]",
"certificatePolicies": "Policy: 1.3.6.1.4.1.6449.1.2.2.7 CPS: https://secure.comodo.com/CPS Policy: 2.23.140.1.2.1 [0]",
"crlDistributionPoints": "Full Name: URI:http://crl.comodoca.com/COMODORSADomainValidationSecureServerCA.crl [0]",
"extendedKeyUsage": "TLS Web Server Authentication, TLS Web Client Authentication [0]",
"keyUsage": "Digital Signature, Key Encipherment [0]",
"subjectAltName": "DNS:*.vulners.com, DNS:vulners.com [0]",
"subjectKeyIdentifier": "69:98:40:E2:DB:D6:29:09:A1:C0:92:A8:FD:FC:3B:C1:3B:C4:0C:44 [0]"
},
"CLIENT_INITIATED_INSECURE_RENEGOTIATION_NOT_SUPPORTED-PCIDSS": "The server does not support client-initiated insecure renegotiation. [1]",
"CLIENT_INITIATED_SECURE_RENEGOTIATION_NOT_SUPPORTED-IBP": "The server does not support client-initiated secure renegotiation. [1]",
"CVE-2014-0224-PCIDSS": "The server is not vulnerable to CVE-2014-0224 (OpenSSL CCS flaw). [4]",
"DESCRIPTIONS": "CERTIFICATE_HOST~Usually, certificates are issued for one or several hostnames. In this particular case, the domain name of your server is not the same as the one indicated in the certificate.|SERVER_PREFERS_PFS_SUITES~Perfect-Forward-Secrecy (PFS), based on Diffie-Hellman Ephemeral key exchange, improves global security of TLS. With RSA, an attacker can intercept encrypted communications and record them in order to decrypt them later if he manages to obtain one private key. However, with PFS, it is not possible to use the private key to decrypt messages intercepted in the past.|INSECURE_SITE_NO_REDIRECT~Redirect the users from the HTTP to the HTTPS version is a good practice to enforce secure browsing.|INSECURE_CONTENT~When the HTTPS version of a website contains insecure elements, it cannot be totally trusted. Attackers can still intercept these elements which can contain personnal data, or include malicious content in them.|SERVER_PROVIDES_HSTS_WITH_LONG_DURATION~HTTP-Strict-Transport-Security basically allows a server to make users browsers remember to browse it using HTTPS for a specified duration.|SERVER_DOES_NOT_PROVIDE_HPKP~HTTP-Public-Key-Pinning basically allows a server to make users browsers remember of a list of signatures of certificates to trust for a specified duration. These certificates can either be server certificate or CA certificate.|POODLE~When using CBC cipher suites, TLS imposes padding to be filled with its own length, as the opposite of SSLv3 for which padding could be anything allowing POODLE attack. POODLE over TLS is a vulnerability that appears when a server does not check padding value when using CBC cipher suites.|CLIENT_INITIATED_SECURE_RENEGOTIATION_NOT_SUPPORTED~Client-initiated secure renegotiation (CVE-2011-1473, CVSSv2: 5.0/10) is a vulnerability that may allow Denial of Service (DoS) attacks on servers supporting it.|CLIENT_INITIATED_INSECURE_RENEGOTIATION_NOT_SUPPORTED~Client-initiated insecure renegotiation (CVE-2009-3555, CVSSv2: 5.8/10) is a vulnerability that may allow attacker to successfully perform Man-in-The-Middle attacks.|SSL_HEARTBLEED~Heartbleed (CVE-2014-0160, CVSSv2: 5.0/10) is an OpenSSL vulnerability allowing attackers to access random portions of data stored in servers memory. It could include user or admin passwords, private keys and other sensitive data.|CVE-2014-0224~OpenSSL Change-Cipher-Specs flaw (CVE-2014-0224, CVSSv2: 5.8/10) is a vulnerability affecting OpenSSL and allowing attacker performing a Man-in-The-Middle attacks to downgrade cipher suite used between client and server.",
"DH_PARAM_SIZE-INFO": "4096 bits [0]",
"DH_PARAM_SIZE-NIST": "4096 bits [1]",
"DH_PARAM_SIZE-PCIDSS": "4096 bits [1]",
"EC_BITS-INFO": "256 bits [0]",
"EC_BITS-NIST": "256 bits [1]",
"EC_BITS-PCIDSS": "256 bits [1]",
"EC_NAME-INFO": "P-256 [0]",
"EC_NAME-PCIDSS": "P-256 [1]",
"FINAL_GRADE": "A",
"HIGHLIGHT": "The server prefers cipher suites supporting Perfect-Forward-Secrecy [1]|The server provides HTTP Strict Transport Security [1]|Your certificate is untrusted [5]",
"HOSTNAME": "78.46.75.17",
"HTTP_RESPONSE": "200 OK",
"INSECURE_CONTENT-IBP": "The website includes HTTP content in HTTPS. [3]",
"INSECURE_SITE_NO_REDIRECT-IBP": "The HTTP version of the website does not redirect to the HTTPS version. We advise to enable redirection. [3]",
"NOT_NIST_COMPLIANT": "The server is not NIST compliant. That does not mean its configuration is not good, but it may have security or compatibility issues. [2]",
"NOT_PCI_COMPLIANT": "The server is not compliant with PCI DSS. That does not mean its configuration is not good, but it may have security or compatibility issues. [5]",
"OCSP_STAPLING_SUPPORTED-NIST": "The server supports OCSP stapling, which allows better verification of the certificate validation status. [1]",
"POODLE-PCIDSS": "The server is not vulnerable to POODLE over TLS. [4]",
"PREFERED_CIPHER_FOR_TLSv1.1": "PFS|TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA [1]",
"PREFERED_CIPHER_FOR_TLSv1.2": "PFS|TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [1]",
"REVERSE_DNS": "static.17.75.46.78.clients.your-server.de",
"SECURE_RENEGOCIATION_SUPPORTED-IBP": "The server supports secure server-initiated renegotiation. [1]",
"SERVER_DOES_NOT_PROVIDE_HPKP-IBP": "The server does not send HTTP-Public-Key-Pinning header. We advise to enable HPKP in order to avoid Man-In-The-Middle attacks. [4]",
"SERVER_IP": "78.46.75.17:443",
"SERVER_PORT": "443",
"SERVER_PREFERS_PFS_SUITES-IBP": "For TLS family of protocols, the server prefers cipher suite(s) providing Perfect Forward Secrecy (PFS). [1]",
"SERVER_PROVIDES_HSTS_WITH_LONG_DURATION-IBP": "Duration (in seconds): 63072000 [1]",
"SERVER_SIGNATURE": "nginx-wallarm",
"SSL_CIPHER-INFO": "TLS_DHE_RSA_WITH_AES_256_CBC_SHA [0], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA [0], TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 [0], TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 [0], TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 [0], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 [0], TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 [0], TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [0]",
"SSL_CIPHER-NIST": "TLS_DHE_RSA_WITH_AES_256_CBC_SHA [1], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA [1], TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 [1], TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 [1], TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 [1], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 [1], TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 [1], TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [1]",
"SSL_CIPHER-PCIDSS": "TLS_DHE_RSA_WITH_AES_256_CBC_SHA [1], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA [1], TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 [1], TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 [1], TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 [1], TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 [1], TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 [1], TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 [1]",
"SSL_COMPRESSION-IBP": "TLS compression is not supported by the server. [1]",
"SSL_HEARTBLEED-PCIDSS": "The server version of OpenSSL is not vulnerable to Heartbleed attack. [4]",
"SSL_NEED_CIPHERS-NIST": "TLS_RSA_WITH_3DES_EDE_CBC_SHA [2], TLS_RSA_WITH_AES_128_CBC_SHA [2], TLS_RSA_WITH_AES_128_GCM_SHA256 [2]",
"SSL_PROTOCOL-INFO": "TLSv1.1 [0], TLSv1.2 [0]",
"SSL_PROTOCOL-NIST": "TLSv1.1 [1], TLSv1.2 [1]",
"SSL_PROTOCOL-PCIDSS": "TLSv1.1 [1], TLSv1.2 [1]",
"THIRD_PARTY_CONTENT": "https://blog.vulners.com/wp-content/themes/catch-kathmandu/style.cssver=4.4.2|https://blog.vulners.com/wp-content/themes/catch-kathmandu/css/genericons/genericons.cssver=3.4.1|https://blog.vulners.com/wp-content/themes/catch-kathmandu/css/dark.css|https://blog.vulners.com/wp-content/themes/catch-kathmandu/css/responsive.cssver=4.4.2|https://blog.vulners.com/wp-includes/js/jquery/jquery.jsver=1.11.3|https://blog.vulners.com/wp-includes/js/jquery/jquery-migrate.min.jsver=1.2.1|https://blog.vulners.com/wp-content/plugins/better-analytics/js/loader.phpver=1.1.3.js|https://blog.vulners.com/wp-content/themes/catch-kathmandu/js/catchkathmandu-allmenu.min.jsver=20140317|https://blog.vulners.com/wp-content/themes/catch-kathmandu/js/catchkathmandu.fitvids.min.jsver=20140317|https://blog.vulners.com/wp-content/themes/catch-kathmandu/js/catchkathmandu-scrollup.min.jsver=20072014|https://blog.vulners.com/wp-includes/js/wp-embed.min.jsver=4.4.2|https://avleonov.com/wp-content/uploads/2016/03/cve.png|https://blog.vulners.com/wp-content/uploads/2016/03/back-e1457556882458.png|https://blog.vulners.com/wp-content/uploads/2016/03/cropped-logo_small-e1457554507539-1.png|https://blog.vulners.com/wp-content/uploads/2016/04/zdt.png|https://blog.vulners.com/wp-content/uploads/2016/04/zdt_full_script.png|https://blog.vulners.com/wp-content/uploads/2016/04/zdt_private.png|https://blog.vulners.com/wp-content/uploads/2016/04/stat.png|https://blog.vulners.com/wp-content/uploads/2016/04/sles_bulletin.png|https://blog.vulners.com/wp-content/uploads/2016/04/badlock.png|https://blog.vulners.com/wp-content/uploads/2016/04/Screenshot-from-2016-04-04-140454.png|https://blog.vulners.com/wp-content/uploads/2016/04/Screenshot-from-2016-04-04-140704.png|https://blog.vulners.com/wp-content/uploads/2016/04/Screenshot-from-2016-04-04-135029.png|https://blog.vulners.com/wp-content/uploads/2016/03/mitre.png|https://blog.vulners.com/wp-content/uploads/2016/03/nvd.png|https://blog.vulners.com/wp-content/uploads/2016/03/Screenshot-from-2016-03-21-124046.png|https://blog.vulners.com/wp-content/themes/catch-kathmandu/images/dark-search.png|https://mc.yandex.ru/metrika/watch.js|https://www.google-analytics.com/analytics.js|https://mc.yandex.ru/metrika/advert.gif|https://mc.yandex.ru/watch/34503445wmode=5callback=_ymjsp956111828page-url=file3A2F2F2Ftmp2Fe7a1dba6c96391f51a82f8c4b541844f64cfce8e777192fc669261f432b47a44.htmlbrowser-info=s3A1024x768x323Ask3A13Afpr3A2166136261013Acn3A13Aw3A1920x12003Az3A1203Ai3A201604211717223Aet3A14612518423Aen3Autf-83Av3A6853Ac3A13Ala3Ac3Awh3A13Apv3A13Als3A9818222434313Arqn3A13Arn3A4149496303Ahid3A8683717913Awn3A216393Ahl3A13Arqnl3A13Ast3A14612518423Au3A1461251842781830643At3AVulners20Blog20E2809320Information20security20news2C20research2C20malware20analysis|https://mc.yandex.ru/watch/34503445/1wmode=5callback=_ymjsp956111828page-url=file3A2F2F2Ftmp2Fe7a1dba6c96391f51a82f8c4b541844f64cfce8e777192fc669261f432b47a44.htmlbrowser-info=s3A1024x768x323Ask3A13Afpr3A2166136261013Acn3A13Aw3A1920x12003Az3A1203Ai3A201604211717223Aet3A14612518423Aen3Autf-83Av3A6853Ac3A13Ala3Ac3Awh3A13Apv3A13Als3A9818222434313Arqn3A13Arn3A4149496303Ahid3A8683717913Awn3A216393Ahl3A13Arqnl3A13Ast3A14612518423Au3A1461251842781830643At3AVulners20Blog20E2809320Information20security20news2C20research2C20malware20analysis [0]",
"TLS_12_SUPPORTED-IBP": "The server supports TLSv1.2 which is the only SSL/TLS protocol that currently has no known flaws or exploitable weaknesses. [1]",
"TLS_FALLBACK_SCSV_SUPPORTED-IBP": "The server supports TLS_FALLBACK_SCSV extension for protocol downgrade attack prevention. [1]",
"TOTAL_POINTS": 95,
"TS": 1461251891,
"httpHeaders": {
"CITY": "Haina (Kloster)",
"COUNTRY": "Germany",
"DNSR": "off",
"GLOBAL_HIGHLIGHTS": [
"By default, if available, the secure version of the website is tested (using HTTPS). If you want to test the HTTP version, please enter the URL with http:// prefix. [4]"
],
"GRADE": "A-",
"HOSTNAME": "78.46.75.17",
"HTTP_HEADERS": {
"Content-Security-Policy": {
"description": "Content-Security-Policy (CSP) allows to define allowed sources for each type of content, helping to defend against XSS attacks for example. It also allows to define several browsers behaviors, like sandbox enforcement, or value to send in Referer HTTP header.",
"highlight": [
"The header was not sent by the server. [3]"
]
},
"Public-Key-Pins": {
"description": "HTTP-Public-Key-Pinning (HPKP) header prevents Man-In-The-Middle attacks against the website by whitelisting allowed certificates in trust chain.",
"highlight": [
"The header was not sent by the server. [3]"
]
},
"Server": {
"description": "Server header is usually sent by webservers to advertise their version.",
"highlight": [
"Webserver does not send detailed information about its version. [1]"
],
"raw": "Server: nginx-wallarm"
},
"Strict-Transport-Security": {
"colored-raw": [],
"description": "HTTP-Strict-Transport-Security (HSTS) header forces user agents to browse the website in HTTPS.",
"enforced": true,
"highlight": [
"The certificate is untrusted, users may not be able to access the website because HSTS forbids bypass of the error message. [3]",
"The header is properly set. [1]"
],
"includeSubdomains": {
"description": "Used to enforce the use of HTTPS on subdomains of your website. [1]"
},
"max-age": {
"63072000": "",
"description": "Sets the time user agents must enforce the use of HTTPS to browse the website. [0]"
},
"preload": {
"description": "Used to allow user agents developers to hardcode to enforce the use of HTTPS only for this website. [1]"
},
"raw": "Strict-Transport-Security: max-age=63072000; includeSubdomains; preload"
},
"X-Content-Type-Options": {
"description": "X-Content-Type-Options allows to disable user agent ability to sniff content type and to only use the one declared. This allows to protect against XSS or Drive-by-Download attacks.",
"highlight": [
"The header is properly set. [1]"
],
"nosniff": "Disables browser ability to detect content type by analyzing it and allows to prevent XSS for example. [1]",
"raw": "X-Content-Type-Options: nosniff"
},
"X-Frame-Options": {
"DENY": "Disables the user agent ability to display this content in a frame. [1]",
"colored-raw": [],
"description": "X-Frame-Options header allows to define if the website should be framed or not, allowing to defend against clickjacking attacks for example.",
"highlight": [
"The header is properly set. [1]"
],
"raw": "X-Frame-Options: DENY"
},
"X-XSS-Protection": {
"1": "Specifies user agent to enable heuristic protection against reflected XSS attacks. [1]",
"colored-raw": [],
"description": "X-XSS-Protection allows to define how user agents should enforce cross-site scripting protection.",
"highlight": [
"The header is properly set. [1]"
],
"mode=block": "Specifies user agent to block server's response when heuristic protection detects an XSS. [1]",
"raw": "X-XSS-Protection: 1; mode=block"
}
},
"HTTP_RESPONSE": "200 OK",
"HTTP_VERBS": {
"GET": "GET method allows to get any information (header and body) relative to the URL specified. [1]",
"HEAD": "HEAD method is identical to GET excepted that only header should be responded by the server. Using it may allow to bypass poorly implemented security mechanisms. [4]",
"POST": "POST method is used to send data to a web server. [1]"
},
"ID": "bd9ed1c8b6f20d7b7a782e0cb0e8020bfd9bd208486440b14b52868f996cc485",
"LAT": "51.000000",
"LNG": "9.000000",
"REDIRECT_TO": "",
"REVERSE_DNS": "static.17.75.46.78.clients.your-server.de",
"SCORE": "80",
"SERVER_IP": "78.46.75.17",
"SERVER_LOCATION": "Haina (Kloster), Germany",
"SERVER_SIGNATURE": "nginx-wallarm",
"TESTED_URL": "https://78.46.75.17",
"TEST_EXECUTIVE_TIME": "7",
"TS": "1461251891"
}
}
}

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Qualys SSL Labs console client | Alexander V. Leonov
Pingback: High-Tech Bridge service and API for SSL/TLS server testing | Security World VietNam
Qualys also doesn’t support any protocols but HTTPS
Hi,
I am one of the developers working for High-Tech Bridge on that project.
Thank you for your awesome post about our service!
I also wanted to add 2 points. You seem wondering why is our anti-abuse token for.
Without this token, it was possible to submit a hostname to test with an arbitrary IP, meaning it was easy to have a result for let’s say htbridge.com that looked to have an F score. This token is here to ensure this behavior is not possible.
The other point is important to me as we spent lot of time to add this feature :). We also enable people to test any port number, meaning you can also test email servers for example. I don’t think SSL Labs allows that.
If you have any suggestion or feature you would like to be added, feel free to contact us, we are always pleased to improve our services.
Pingback: When a free scanning service detects vulnerabilities better | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Free High-Tech Bridge ImmuniWeb Application Discovery service | Alexander V. Leonov