Great OpenVAS news: delay in plugin feed will be dropped, new GVM-Tools for remote management released. Jan Oliver Wagner, CEO of Greenbone and OpenVAS Community leader sent recently several messages to community email list with the great news.
First of all, Greenbone decided to drop two weeks delay in a free plugin feed, that was implemented in June 2017 and made some OpenVAS users pretty nervous.
I wrote about it in “GSM Community Edition and lagging OpenVAS Plugin Feed“. The good thing is that, it has increased interest in NASL scripting among OpenVAS users. I also made some steps in this way in “Adding third party nasl plugins to OpenVAS“. I don’t now why Greenbone finally decided to drop this delay, but I am very glad for this decision. Wise move!
The feed will stay delayed until September 4th, 2017. To demonstrate the current state I used some data from Vulners.com collections. Let’s see the nasl vulnerability detection plugins for CentOS in Nessus and OpenVAS. I know that Windows would be much more clear, but Microsoft released latest MS17-023 bulletin in March, so now there is no much difference there.
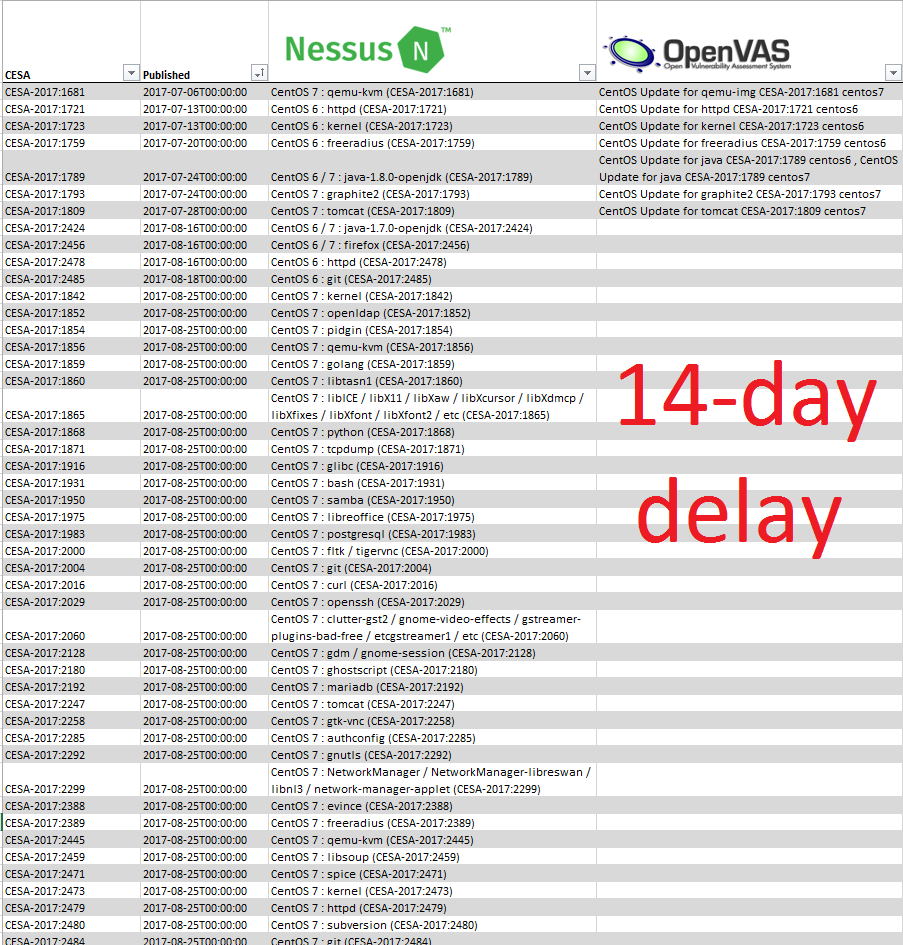
As you can see, no OpenVAS plugins since 2017-08-16, literally two weeks. And I hope this will change very soon.
Don’t forget that NVT will be called now GCF (Greenbone Community Feed) and some advanced enterprise-level checks will be now released only in paid feed.
Another good news is the recent release of open source GVM-Tools for controlling OpenVAS remotelly. It will replace old console client openvas-cli (omp). Let’s try to download and install it on Debian host with installed OpenVAS (see “Installing OpenVAS 9 from the sources“).
ssh vmuser@192.168.56.120
su -
apt-get install python3-setuptools python3 python3-dev libffi-dev
wget https://bitbucket.org/greenbone/gvm-tools/get/1.2.0.tar.gz
tar -xzf 1.2.0.tar.gz
cd greenbone-gvm-tools-77352f8dfa2e/
python3 setup.py install
After it you will have utility gvm-cli, that you can use to controll OpenVAS by ssh, tls or unix socket. Well, I had some troubles with tls connection:
gvm-cli tls --hostname localhost --gmp-username admin --gmp-password 1 -X "<get_version/>"
[Errno 111] Connection refused
But I could run it via socket:
$ openvasmd -c test
gvm-cli socket --sockpath test --gmp-username admin --gmp-password 1 -X "<get_version/>"
<get_version_response status="200" status_text="OK"><version>7.0</version></get_version_response>
I can get information about scans tasks:
$ gvm-cli socket --sockpath test --gmp-username admin --gmp-password 1 -X "<commands><authenticate><credentials><username>admin</username><password>1</password></credentials></authenticate><get_tasks/></commands>"
<commands_response status="200" status_text="OK"><authenticate_response status="200" status_text="OK"><role>Admin</role><timezone>UTC</timezone><severity>nist</severity></authenticate_response><get_tasks_response status="200" status_text="OK"><apply_overrides>0</apply_overrides><task id="e356b6d1-43cf-4da8-b7a0-951c740116e9">...</task><filters id="">...</filters><sort><field>name<order>ascending</order></field></sort><tasks start="1" max="1000"/><task_count>1<filtered>1</filtered><page>1</page></task_count></get_tasks_response></commands_response>
Great thing is that this tool is written in python and there is a mechanism to run specially written scripts in tool called gvm-pyshell:
gvm-pyshell socket --sockpath test --gmp-username admin --gmp-password 1 script.gmp
Here is the list of sample scripts:
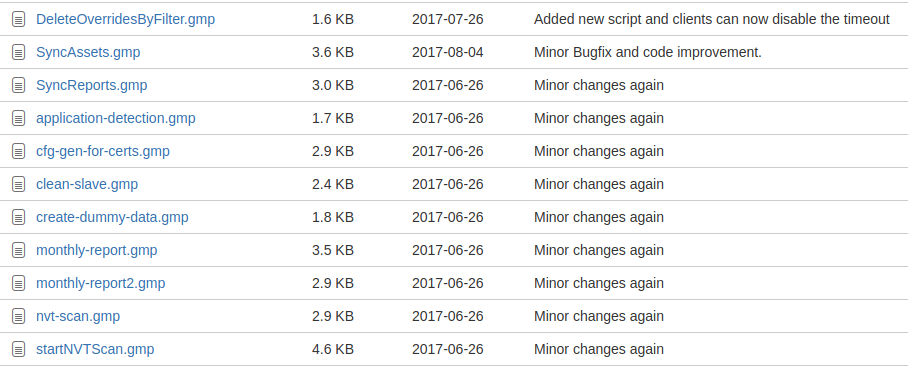
However, this idea of making special shell and special scripts looking a bit strange for me. Imho, just using gvm_connection.py classes in your own python will make the process of managing OpenVAS much more efficient.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Again, great post. Any news on the “socket only” connection? I’d really like to use it over SSH / TLS (some sort of remote). I could just wrap it up in a script, but seems unnecessary overhead when I it is possible to just connect directly with the gvm tool set