August 2023: GitHub PoCs, Vulristics, Qualys First-Party, Tenable ExposureAI, SC Awards and Rapid7, Anglo-Saxon list, MS Patch Tuesday, WinRAR, Juniper. Hello everyone! This month I decided NOT to make an episode completely dedicated to Microsoft Patch Tuesday. Instead, this episode will be an answer to the question of how my Vulnerability Management month went. A retrospection of some kind.
Alternative video link (for Russia): https://vk.com/video-149273431_456239134
GitHub exploits and Vulristics
This month I made some improvements to my Vulristics vulnerability prioritization tool. These changes relate to the use of exploit data on Github. We all know that exploits are often posted on GitHub. But how adequate is this source in order to evaluate the exploitability?
PoC in Github
For example, there is an interesting PoC in GitHub repository on github. It contains the results of an automated search for exploits of CVE vulnerabilities on GitHub. There are currently PoCs for 4484 CVE IDs.
Distribution by years:
CVE-1999-: 4 CVE-2000-: 4
CVE-2001-: 10 CVE-2002-: 14
CVE-2003-: 6 CVE-2004-: 9
CVE-2005-: 7 CVE-2006-: 13
CVE-2007-: 18 CVE-2008-: 21
CVE-2009-: 22 CVE-2010-: 25
CVE-2011-: 27 CVE-2012-: 39
CVE-2013-: 64 CVE-2014-: 128
CVE-2015-: 144 CVE-2016-: 185
CVE-2017-: 323 CVE-2018-: 407
CVE-2019-: 504 CVE-2020-: 684
CVE-2021-: 747 CVE-2022-: 739
CVE-2023-*: 340The total number of CVEs is growing, and so is the number of exploitable CVEs. ⤴️ But no one guarantees that PoC is functional and that there are no rickrolls or malware. Be careful.
For example, it contains Office RCE vulnerability (CVE-2023-36884) from the July Patch Tuesday. But if you look closely, everything is not so rosy. 😐 Let’s see.
- ❌ Maxwitat/CVE-2023-36884-Scripts-for-Intune-Remediation-SCCM-Compliance-Baseline – script for remediation
- ❌ deepinstinct/Storm0978-RomCom-Campaign – IOCs
- ❌ zerosorai/CVE-2023-36884 – remediation utility
- ❌ tarraschk/CVE-2023-36884-Checker – vulnerability detection script
- ❌ or2me/CVE-2023-36884_patcher – remediation utility
- ❌ ToddMaxey/CVE-2023-36884 – script for remediation
- ❌ ridsoliveira/Fix-CVE-2023-36884 – script for remediation
- ❌ raresteak/CVE-2023-36884 – information for remediation
There is no POC yet. 🤷♂️
So “PoC in GitHub” would be more appropriate to call “CVE mentions in GitHub”. It will highlight mentions of CVEs, but, of course, it will not show the context. Then only manual analysis or some automated classification will help you.
Vulristics vulners-use-github-exploits-flag
The ambiguity of exploitation data on GitHub is also bad for my Vulristics reports. For high-profile vulnerabilities, such as Zerologon (CVE-2020-1472), there are too many references to GitHub in the report, most of which are not related to exploits.
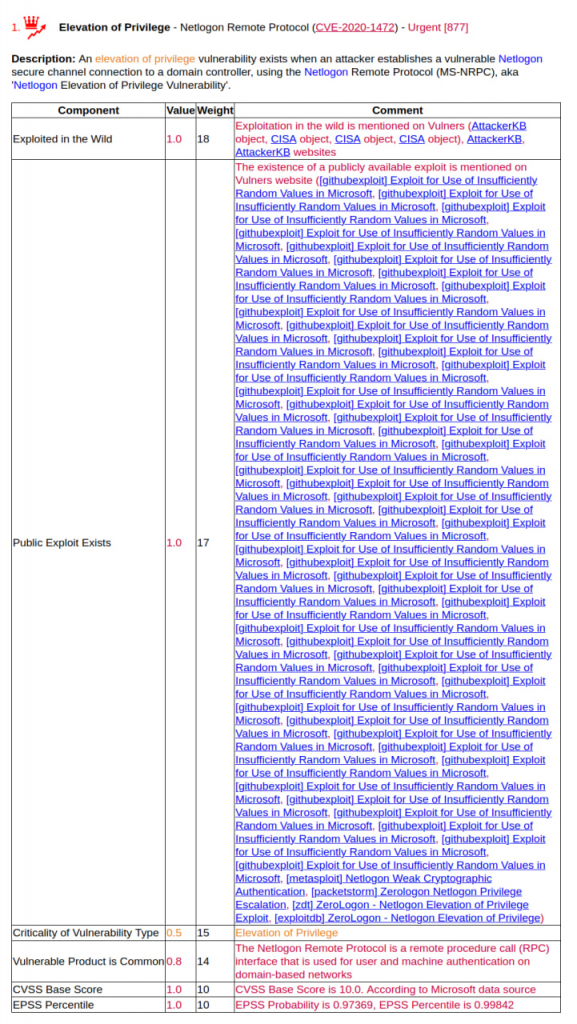
And it is very difficult to automatically understand which repositories contain exploits and which contain irrelevant content. And, as a rule, it is not really necessary. Fully functional exploit will most likely end up in specialized exploit packs, although it may happen with some delay.
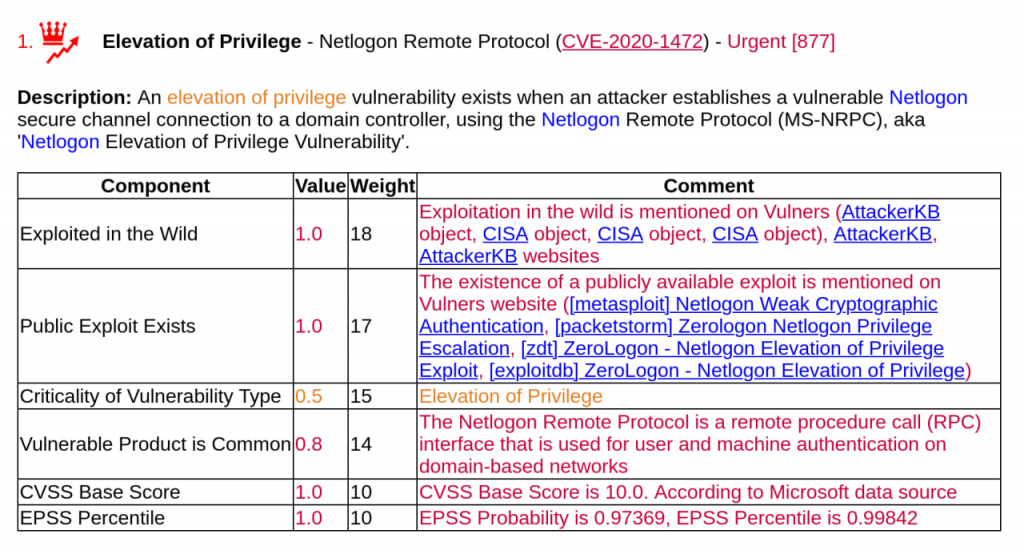
Therefore, I think Vulristics users should be able to generate both reports containing as much information about exploits as possible (although it will be littered) and reports that take into account only known exploit packs.
I have added the option --vulners-use-github-exploits-flag, which can be either True or False. The default value is True.
I also added [source] links.
Exceptions
An exploit from GitHub, as a rule, ends up in a specialized exploit pack over time, BUT NOT ALWAYS! For example, Command Injection – SAP NetWeaver (CVE-2022-22536).
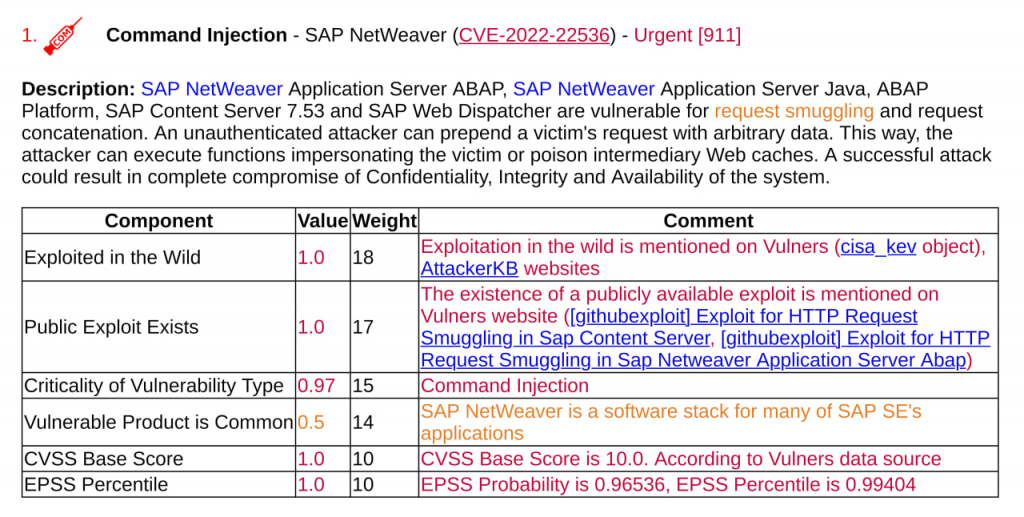
We see that exploits for this vulnerability are available only on the GitHub. And, judging by the description, they are valid.
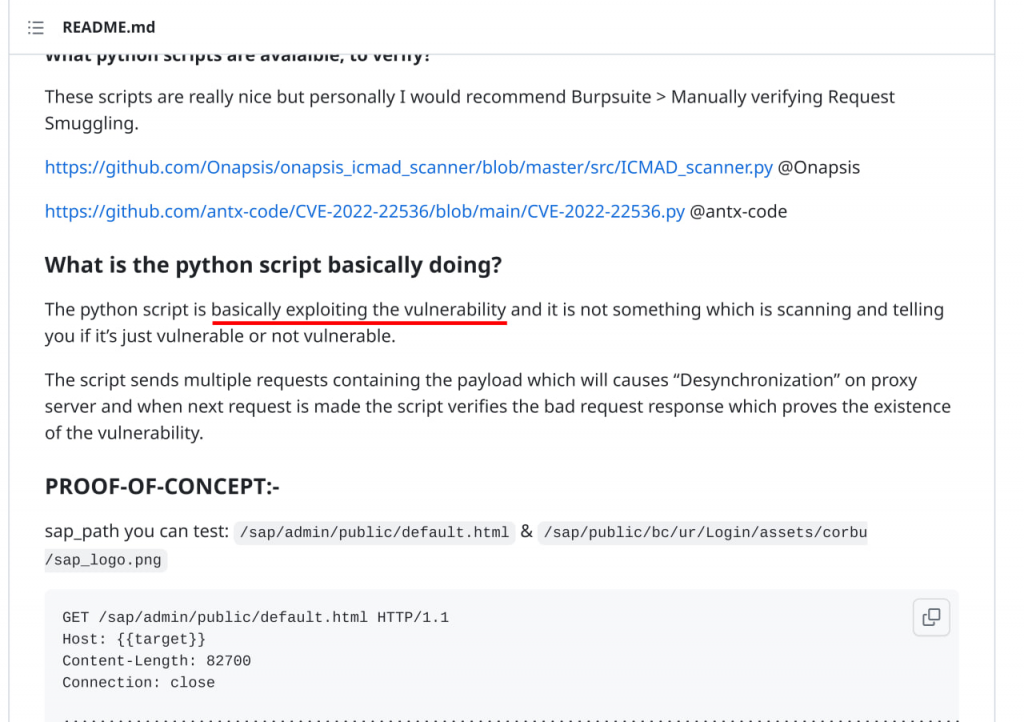
And if we generate a Vulristics report with --vulners-use-github-exploits-flag "False", then we will lose this valuable information.
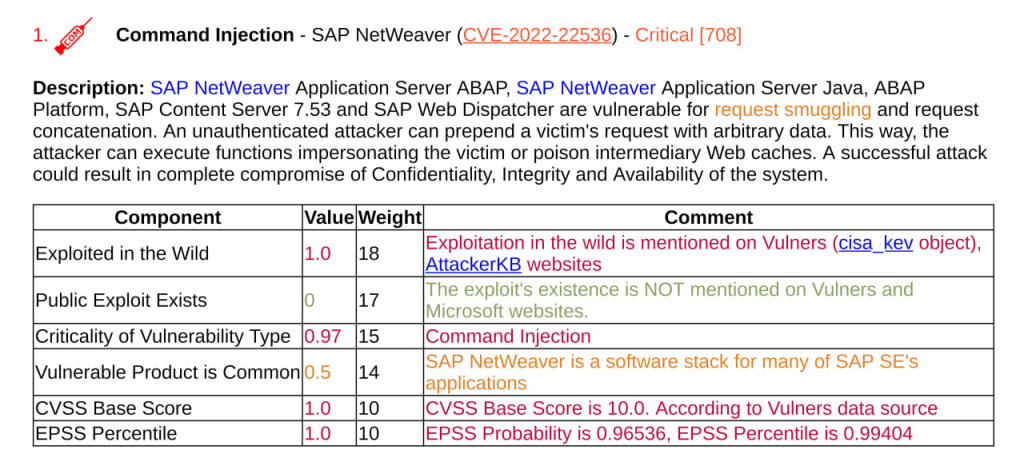
So be aware and use the option with caution. 😉
VM vendors updates
Qualys First-Party Application Risk Detection and Remediation
In early August, Qualys introduced new capabilities for analyzing the vulnerabilities of self-written (First-Party) and open source applications.
- Custom Assessment and Remediation (CAR) is a mechanism for adding your own detection scripts, including PowerShell and Python scripts. You can write your own detection script (for example, using the versions that the application security guys told you), add it to Qualys and get a list of vulnerable hosts. Such vulnerabilities will have a QID and can be treated as vulnerabilities detected by Qualys itself.
- Runtime Software Composition Analysis (SCA). During a vulnerability scan, not only the software itself is checked, but also the libraries used by this software. In fact, Qualys Agent runs through the file system and searches / analyzes library files (including Log4j). This is not a super new feature. I have seen such detections in Microsoft Defender for Endpoint for a long time. But apparently it becomes a mandatory feature.
Tenable ExposureAI
Tenable announced Vulnerability (Exposure) Management with generative AI similar to ChatGPT. The product (or rather technology) will be called ExposureAI and will be available as part of Tenable One.
Main features:
- It will be possible to make requests in a natural language.
- It will be possible to generate human-readable descriptions of Attack Path scenarios (this saves time when preparing reports).
- It will be possible to see insights “what needs to be done first”.
As with Cyclops Security, which announced similar functionality a little earlier, it all depends on how smart the system turns out to be and how bad mistakes it makes.
SC Awards and Rapid7
SC Awards continues to be fun. This year Rapid7 InsightVM received “Best Vulnerability Management Solution”. In the nomination there was Tenable – it’s ok. Do you know what other 3 giants and innovators of the VM market were there?
🔸 Palo Alto Networks Prisma Cloud – cloud-native application protection platform 😀
🔸 Lacework – cloud security platform 😄
🔸 Coalfire Ransomware Simulation-as-a-Service (RSaaS) 😆
Have the contest organizers heard of Qualys VM? 😏
Apparently, so that Tenable would not be offended, they were given “Best Risk / Policy Management Solution” (Qualys was also in this nomination) and “Best Security Company”. The company is the best, but apparently their VM is so-so, Rapid7’s solution is better. 🙃 The only pity is that Rapid7 seems to have problems with sales of this best VM solution. “Rapid7 will lay off about 18 per cent of its workforce, around 470 employees, with significant cuts to sales and engineering – as well as permanently close some office locations”.
Now let’s talk about vulnerabilities.
Anglo-Saxon vulnerability lists
Anglo-Saxon state security agencies from 5 countries issued a joint advisory “2022’s Top Routinely Exploited Vulnerabilities“. I took this report, wrote out the CVE references and released 2 Vulristics reports:
In the Top 12 Vulnerabilities, all CVEs have links to exploits and signs of exploitation in the wild. All of them are Urgent, except for one, because it is EoP in the not-so-common Workspace One. The most critical are RCEs in Apache Log4j2, Microsoft Exchange, and Confluence.
In the extended report, all CVEs have the sign of exploitation in the wild, but there are 6 vulnerabilities without links to exploits and therefore with Critical/High criticality. The most critical are RCEs in Apache HTTP Server, Apache Log4j2, Windows RDP and Microsoft Exchange.
It is worth noting that the extended list contains such Oldies But Goodies vulnerabilities as:
- Zerologon (CVE-2020-1472). A vulnerability in the cryptography of Microsoft’s Netlogon process that allows an attack against Microsoft Active Directory domain controllers

- Microsoft Office RCE (CVE-2017-11882). The PoC for this vulnerability appeared a week after the publication in 2017 and since then, for more than 5 years, it has been actively exploited. 🙈

Compared to last year advisory, GitLab and exotics like Hikvision and Buffalo are gone. The set of CVEs looks better.
Commands for those who want to build a report themselves in Vulristics using comments for CVEs from AA23-215A.
$ cat AA23-215A_comments.txt | grep -v "30 Additional" | egrep -o "CVE-[0-9]-[0-9]" | sort | uniq > AA23-215A_cves_top12.txt
$ cat AA23-215A_comments.txt | egrep -o "CVE-[0-9]-[0-9]" | sort | uniq > AA23-215A_cves.txt
$ python3 vulristics.py --report-type "cve_list" --cve-project-name "AA23-215A" --cve-list-path "AA23-215A_cves.txt" --cve-comments-path "AA23-215A_comments.txt" --cve-data-sources "ms,nvd,epss,vulners,attackerkb" --rewrite-flag "True"
$ python3 vulristics.py --report-type "cve_list" --cve-project-name "AA23-215A_top12" --cve-list-path "AA23-215A_cves_top12.txt" --cve-comments-path "AA23-215A_comments.txt" --cve-data-sources "ms,nvd,epss,vulners,attackerkb" --rewrite-flag "False"Funny detail: 8 agencies from 5 countries released this, but there was no one who carefully read and noticed that in several places the identifier for Log4Shell is written as “CVE-2021- 44228” with a space. Both in pdf, and in the web-version. 😏
August Microsoft Patch Tuesday
My impressions of the August Microsoft Patch Tuesday – nothing special. 🫠
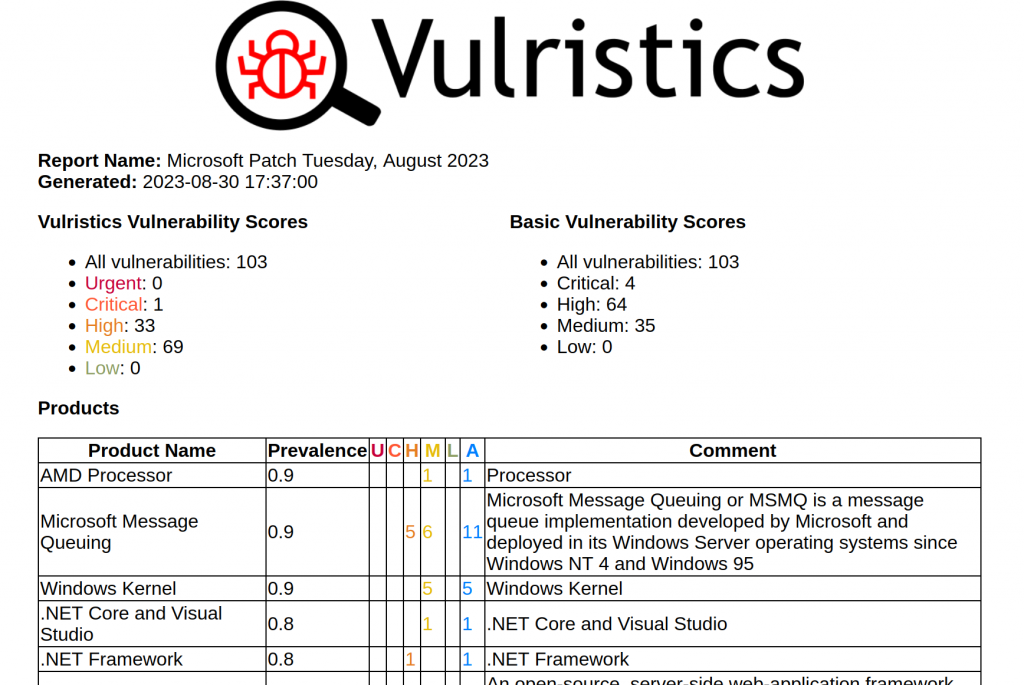
- All vulnerabilities: 103
- Urgent: 0
- Critical: 1
- High: 33
- Medium: 69
- Low: 0
Formally, the most critical vulnerability is Denial of Service – .NET and Visual Studio (CVE-2023-38180), because there are signs of exploitation. There are no details, but it is somehow doubtful. 🤡
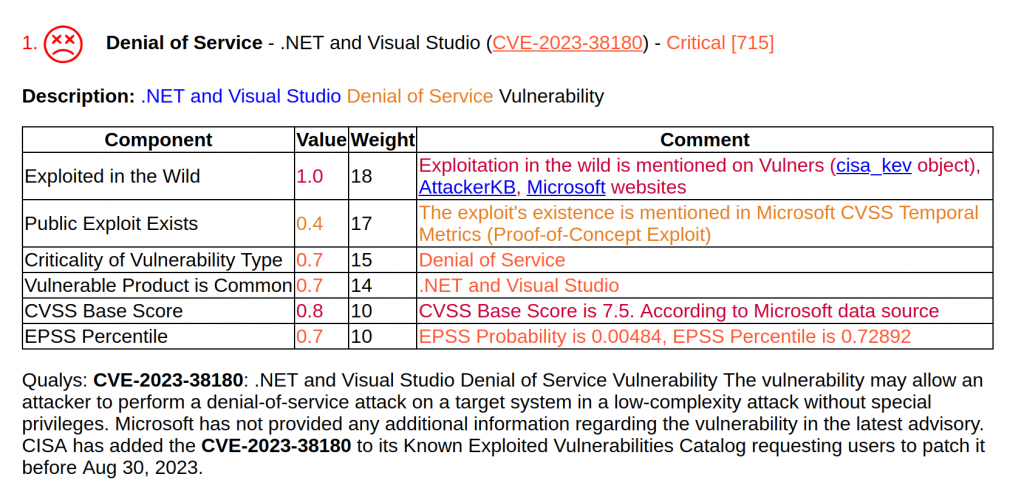
No more vulnerabilities with public exploits or signs of exploitation.
Several Remote Code Executions – Microsoft Exchange (CVE-2023-35368, CVE-2023-38185, CVE-2023-35388, CVE-2023-38182). 3 of them definitely require authentication, one is unclear. This authentication can potentially be obtained through Elevation of Privilege – Microsoft Exchange (CVE-2023-21709) – “This vulnerability allows a remote, unauthenticated attacker to log in as another user”. It’s better to patch!
Remote Code Execution – Microsoft Teams (CVE-2023-29328, CVE-2023-29330). Fortunately, in Russia it’s not popular anymore.
There is also a bunch of EoPs in the Windows kernel&components.
Full report: ms_patch_tuesday_august2023_report
Other important vulnerabilities
Among other vulnerabilities of this month, I would like to highlight:
- Actively exploited since April 2023 WinRAR Extension Spoofing (CVE-2023-38831), which also has a public exploit. I highly recommend installing the WinRAR 6.23 update, which also fixes the potentially dangerous RCE CVE-2023-40477.

- Numerous vulnerabilities in the J-Web component (web console) of the Juniper Networks Junos operating system on SRX and EX series devices. These are the vulnerabilities that lead to RCE and for them there is a detailed review and a PoC.


Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: September 2023: VM courses, Bahasa Indonesia, Russian Podcasts, Goodbye Tinkoff, MS Patch Tuesday, Qualys TOP 20, Linux, Forrester, GigaOm, R-Vision VM | Alexander V. Leonov
Pingback: Выпустил новую англоязычную видяшечку | Александр В. Леонов