Rapid7 Nexpose in 2017. Last year I tested Rapid7 Nexpose and wrote two posts about installation and use of Nexpose Community Edition and Nexpose API. I didn’t follow news of this vendor for a about year. Today I watched live demo of Nexpose latest version. It has some new interesting features, improvements and ideas, that I would like to mention.
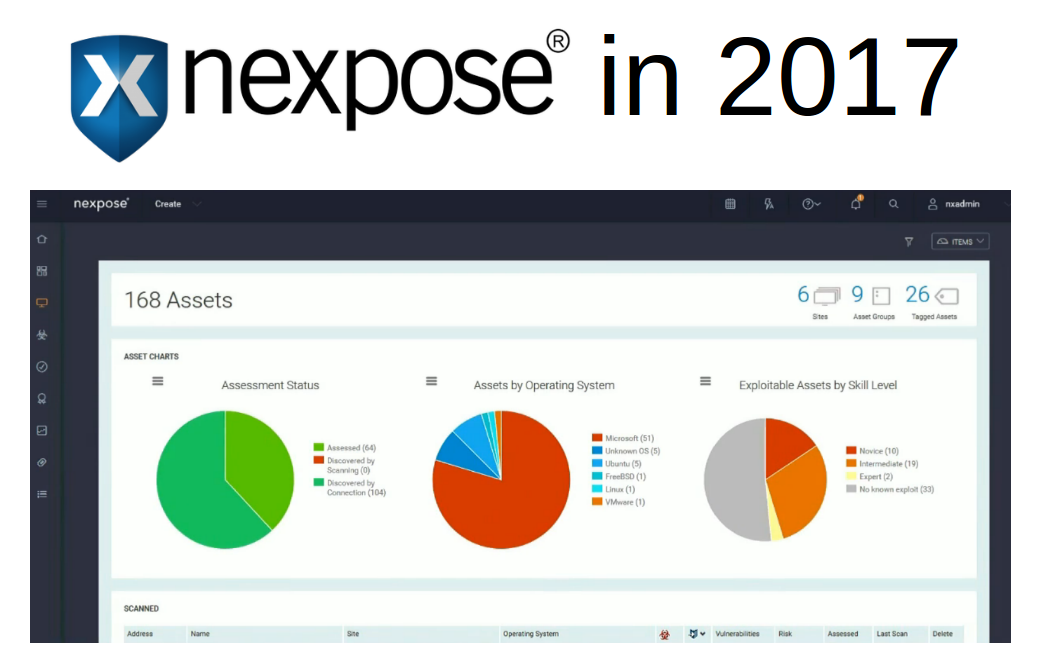
And of course, things that sales people say to you should be always taken with some skepticism. Only concrete implementation tested in your environment matters. But they usually mention some useful ideas that can be perceived independently from the products they promote.
Host detection
Scanning IP-ranges to find active hosts in your environment is classical way, but it is definitely not the most effective solution. And when (if? :-)) we all finally move to ipv6 it will be simply impossible.
What are the alternatives?
Integration
Well, historically Tenable suggests to use traffic analysis for host detection, i.e. Passive Vulnerability Scanner (PVS). Rapid7 historically hadn’t such kind of solution, but the have experience in getting this data from 3d party systems:
- VMware vSphere
- Amazon Web Services
- Exchange
- DHCP
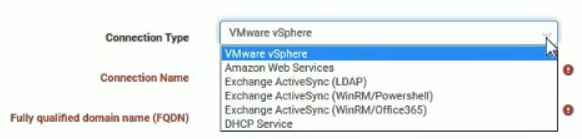
You can have different attitudes to this particular scanning solution, but in any case it’s very cool to take active host data from virtualization, monitoring and other IT systems. And not only information on the host’s activity, but also data about installed software and running processes, if it is possible.
Agents
Another alternative is to use local Agents. I already wrote about Nessus agents and Qualys agents. Rapid7 presented their agents last summer. I have not tried them yet, but they are similar in description to Qualys agents. They do not make checks on the host, but only collect some inventory information. I know that they are available now for for Windows, Linux and Mac.
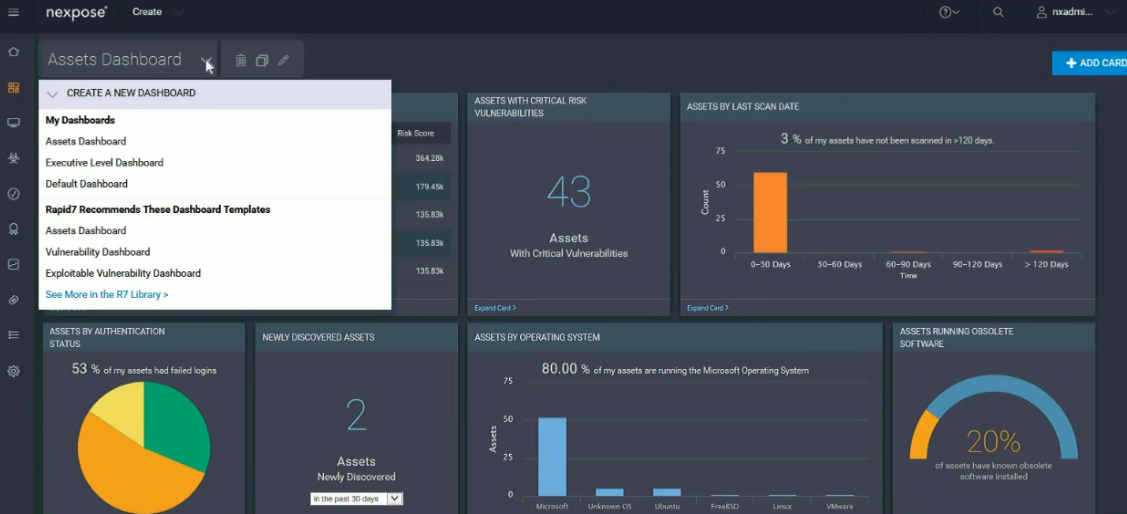
Asset Management
Like Tenable.IO, Rapid7 began to pay great attention to Asset Management. Now the uniqueness of the Asset is defined by combination of MAC address, hostname and UUID. The UUID, if I understand it correctly, is registered during the authorization scan, like Tenable.io and Qualys Cloud do. And like in Qualys, Rapid7 Nexpose supports unlimited discovery scans. You pay only for those hosts for which vulnerability assessment will be performed.
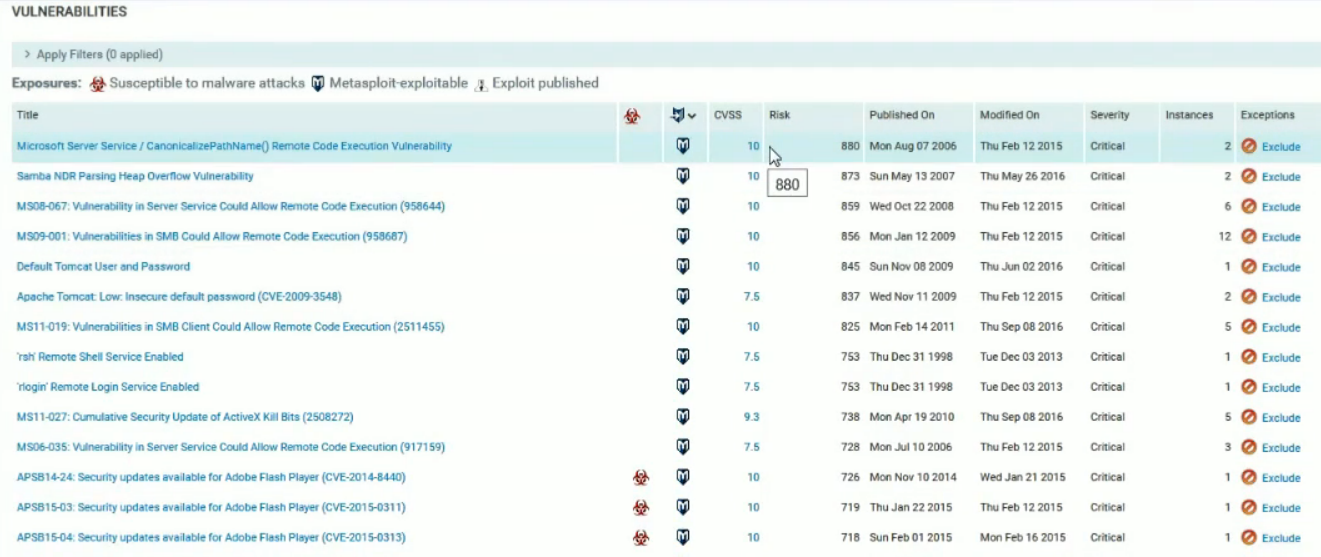
Vulnerability Prioritisation
During the presentation, Arian Massoudi criticized CVSS as a means to prioritize the vulnerability. And basically I agree with him.
Nexpose uses the integral assessment of “Real risk”. It takes into account:
- Malware attacks
- Metasploit exploit available
- Exploit published
- Age of vulnerability – older is more dangerous.
- Successful exploitations in Rapid7 environment
Reports
I’m not a big fan of dashboards and reports, and I am convinced that practically any organization needs external tools for reporting. But I liked this one. Top 25 Remediations by Risk with details. If you don’t know what to do, patch these:
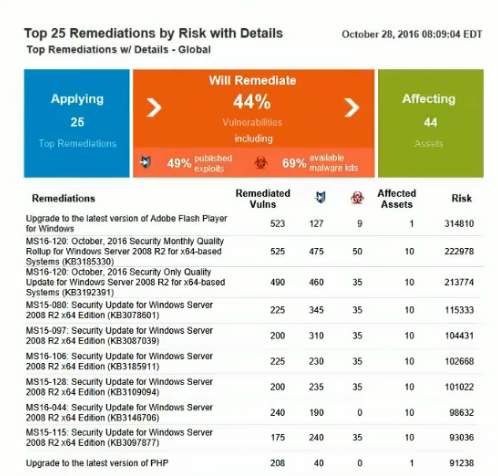
With detailed recommendations for patching:
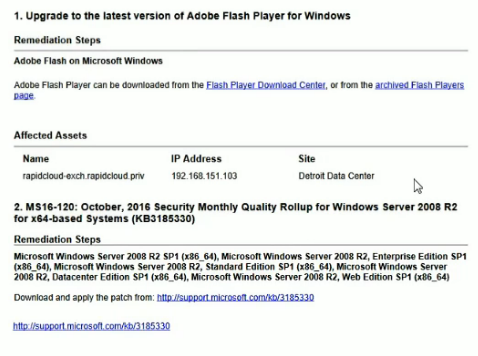
And this one makes possible to compare vulnerability state in different offices of your organization:
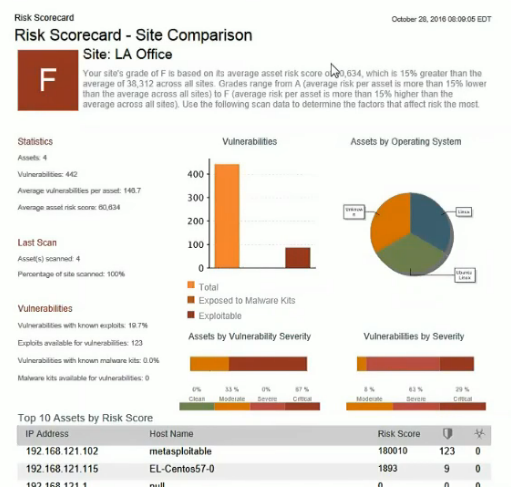
Nexpose Now
This is a cloud service that uses Nexpose data. Dashboards are really beautiful. For example, dashboards for controlling SSL certificates.
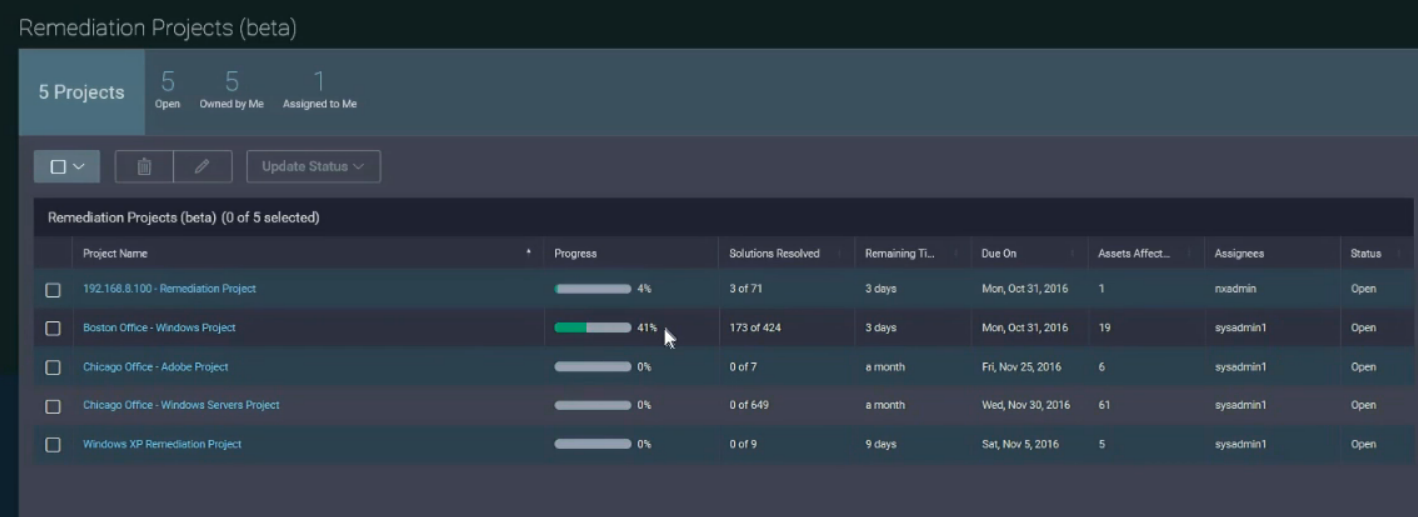
Quite an interesting interface for creating Remediation Projects:
Security specialist can specify what software needs to be updated and on which hosts, and set the SLA. System administrator will be able to log in, perform work, and run check scan. Looks useful. Although I am a fan of custom VM Remediation automation using jira.
What I really like about Rapid7 is that they are trying to understand how security professionals and system administrators do they job in practice and trying to automate the workflow naturally, including vulnerability prioritization. It is unlikely that this particular solution will suit everyone, but the approach is worthy.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

SecurityCenter can also be configured to allow administrators to perform remediation scans on their assets. Regarding JIRA integration, Tenable far far away from a real enterprise workflow.
Thanks for comment, Oleksandr! Totally agree with you about SecurityCenter. Imho, it’s still better to get raw vulnerability scanning data and produce tickets that most suitable for your IT department.
Pingback: Microsoft security solutions against ransomware and APT | Alexander V. Leonov