New Nessus 7 Professional and the end of cost-effective Vulnerability Management (as we knew it). It’s an epic and really sad news. 🙁

When people asked me about the cost-effective solution for Vulnerability Management I usually answered: “Nessus Professional with some additional automation through Nessus API”.
With just a couple of Nessus Professional scanning nodes it was possible to scan all the infrastructure and network perimeter (see “Vulnerability Management for Network Perimeter“). Price for each node was fixed and reasonable. And you could make your any reports from the raw scan data, as you like it.
Nessus Pro was still were best choice even when Tenable:
- Cut off master/slave functionality in Nessus and created “Nessus Manager”.
- Changed API completely during the update from 5 to 6 version.
- Gradually increased the price from $1,5k to $2,7k per scanning node per year.
But unfortunately it’s not anymore. End of an era.
And what is even more sad is that Tenable does not mention disabling the API and multi-user function in the main Nessus 7 marketing, as it never was, as if it’s not very important. Just look at “Announcing Nessus Professional v7” – not a word about “API” or users. Only in additional link:
Only there, in the text (not a video) there is an information about removed features.
The nice little things like “Easily transferable license” and “Emailed scan reports and custom report name / logo” do not make it any better.
So, what next?
I don’t know. We have some time to think until the December 31, 2018 or until the end of the license. Just do not update to the 7th version. Ignore this:
![]()
I don’t see much sense in updating to the 7th version. Obviously, solution with one shared admin user can’t be used in a big organization. And the lack of API kills all the work spent on VM process automation with Nessus.
What options I see:
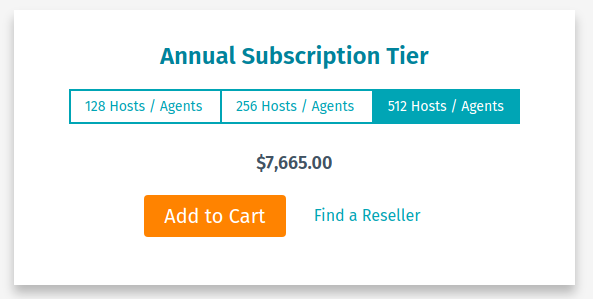
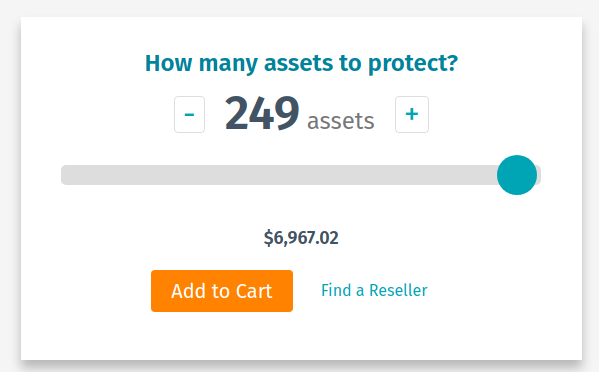
- Switch to the enterprise scanning solution licensed by IP-addresses. And to save existing automation efforts this might be Nessus Manager or, if you are able to use cloud solutions, Tenable.io. I think Tenable expect this step from the current Nessus Professional users. For a big infrastructure total price will be 10 and even more times higher. For example,
Nessus Manager:
Tenable.io VM:
- Switch to Tenable SecurityCenter with the minimal amount of IP addresses in order to use Nessus for SecurityCenter, which can save API capabilities. Now Tenable says that only API in Nessus Professional will be deprecated, but they can change their mind any time. So, it’s more like a hack.
- Keep Nessus Professional and start using the API for WebGui. It is not documented, it can be changed at any time, but technically it is possible and it’s relatively easy (See “Burp Suite Free Edition and NTLM authentication in ASP.net applications“). Will this violate the license? It’s not clear. But anyone who wants to automate will do it anyway with Selenium or even SikuliX. 🙂
- Find a comparable solution without licensing by IP addresses, with powerful API, with good scanning quality and reasonable fixed per year price. At the moment I do not know of any solution comparable to Nessus in functionality. But I believe it is possible to do something similar based on OpenVAS. Interested in this kind of solution? Please let me know.
- Make your own Vulnerability Scanner. For example, I decided to start working on Vulchain. Of course, creating a complete analogue of Nessus is an impossible task for one person and even for a small team. But creating a Vulnerability Management solution that will assess some concrete host types in some concrete scan modes seems pretty doable.
I’m very interested to know your opinion, especially if you are an active user of Nessus. What do you think about this situation?

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

I think Nessus have shot themselves in the foot.
We are a Qualys house at the moment and I persuaded the management to order three NP scanners to fill a niche. From there, Tenable stood a chance of getting a bigger slice – and maybe all of the work from Qualys. There is zero chance of that happening now – I have just cancelled the three NP orders as they had not been delivered by the API cut-off point.
Tenable seem to think NP and the API is taking money away from their bigger products. My experience here (until cancelled) and at previous employer where using NP lead to a contract upgrade to NM is they are wrong. As often as not it is a stepping stone, a starting point to the sale of their bigger products.
Well, they seem to have removed the first stepping stone, the first rung on the ladder – and now they will get nothing from this company.
Personally, I have 12 months to sort out replacement – I feel very upset at having put my personal reputation on the line with clients recommending Nessus to them.
It all reminds me of Solaris x86 – where Sun tried to pull it to help their Linux sales. It ended up helping other Linux sales, particularly RedHat, and not their own. By the time Sun realised their mistake and reintroduced the product it was too late. Linux had the market. Now Sun is but a small cog in the big Oracle.
Alexander, what can I say?
Julian is right, shot in the selves foot. Or as we speak Russian, it is difficult to translate, but you will understand :). about the saw and the tree branch :).
It’s sad, it’s sad that in April I will have a big headache. I do not believe that Tenablay will change his mind.
Sad day indeed for Nessus API users. Hopefully Tenable will rethink this decision. I have tested OpenVAS several times as an alternative to Nessus, most recently about a month ago and have found it to be unstable and extremely slow as compared to Nessus. A scan of a single subnet in my infrastructure takes 5 hours with OpenVAS compared to 1 with Nessus with less complete results. It doesn’t seem like a viable alternative in a consulting situation where you are onsite at a customer office and billing them by the hour.
Can’t say much about the unstable of OpenVAS of as it runs quite stable here. Just a note about the scan speed:
If you would like to compare the scan speed between Nessus and OpenVAS you need to enable “Thorough tests” and set the “Report paranoia” to Paranoid.
Concerning the less complete results Alex is always mentioning that each scanner has its strengths and weakness. Additionally the OpenVAS Community Feed doesn’t contain enterprise grade NVTs since a few months so this might play another role here as well as the infrastructure itself.
It is interesting that you mention feed costs – I have not obtained a quote yet for our OpenVAS, but in general terms I think most people have paid for a Nessus Professional licence and get the feed for free – so paying for a feed to add to a free product is likely to be cost neutral.
Thanks for the hints on scan speed and information on stability.
Meanwhile Tenable Community still appears to be down – perhaps they are scared that the platform will be hijacked to discuss the downgrades in Nessus 7.
Tenable do have a narrow window to redeem themselves – assuming they have not completely trashed to code – to release a version of Nessus Professional with the removed features reinstated – maybe called Nessus Professional Plus.
But as I say above with Solaris x86 – it is a narrow window. Once users have moved to another product I c annot see many being prepared to move back.
Hey,
> Thanks for the hints on scan speed
no problem. Just to have some numbers of my own infrastructure:
Network: local /24
Hosts: 21 up hosts (mixed services like HTTP, SSH, Database etc.)
Nessus 7 with default scan config + CGI scanning enabled: 27 minutes
Nessus 7 with “Thorough tests” and “Report paranoia” like explained above: 2 hours, 3 minutes
OpenVAS 9 with “full and fast” scan config: 1 hour, 1 minutes
with nearly the same results (there are always differences between both).
The OpenVAS “full and fast” is basically a Nessus scan config which has enabled CGI scanning as well as “Thorough tests” and “Report paranoia” set like explained above.
Personally I have been managing VM for about 10 years now and during that time always found QUALYS to be the best solution. They always offer free trials of anything I want to test and as many IPs as I would like to scan.
And the biggest cost is typically in man hours to fix the vulnerabilities you find, and so this is where the accuracy of Qualys really shines, saving you time and effort chasing down false positives.
I hear they have automated patching available now too! Which should save even more time/effort!
You really have to think about the whole cost of purchasing, maintaining, updating and using/remediation.
Qualys is undoubtedly a good product – we use it here – but it is cloud based and IP count licensed – like the Tenable.io product – see pricing above.
The Nessus professional with its API and unlimited capabilities was an entirely different beast – and Qualys have nothing similar. Sadly neither do Tenable now.
We used to automate things with cmdline client _many_ years ago. They deprecated it. Binary was there for years. They broke the functionallity occasionally, nevertheless, and every time we contacted support the answer was: “yeah it’s broken… but no support, use api”. Functionallity was broken for months until something was done.
But with the API you didn’t have template export. Which by accident was available in another product of Tenable. Well, we reprogrammed the whole thing using the API… And now… this. Randomly taking important feature to force you to buy other expensive products you don’t need. A shame. Srsly, time to look for other products.
We’re also affected by Tenable’s announcement as we just finished our API connection to offer automated vulnerability scans. Now we have to think about another solution which not only offers an API, but also can be licensed without any IP limit, because we got too much assets. I found the Retina Vulnerability Scanner from BeyondTrust. Licensing seems to be ok, does anyone know if it has an API?
It is a truly epic and sad news. We had a few Nessus licenses to renew for 12/20/2017 and several more to buy and after we saw these news we didn’t renew the old licenses and we will go after other solution. Unfortunately, it looks that OpenVAS is Open Source partially. You can see that they have a GSA on GitHub with code, functionalities and libraries (https://github.com/greenbone/gsa/blob/master/gsad/src/gsad.c) that the Open Source version doesn’t have (GSA 7.0.2). Maybe they intended to make that repository private and they leave it public by mistake but it tells, and I hope to be wrong, that the spirit of Greenbone is to close the source to OpenVAS step-by-step, just like Tenable did with Nessus. Even tho Greenbone dropped the delay in the plugin feed, that reveals that their are thinking about reducing the support for the Open Source Version. On top of that, both Nessus and OpenVAS support less than 97k CVE’s falling short both, Nessus and Greenbone Commercial Feed, to find all the CVE’s.
In this case the github part is a complete misinterpretation on your side. Currently modules are step by step migrated to github and i see no intention to make OpenVAS closed source. Rather it looks like quite the opposite. And if you check the github tags correctly you will also find the apparently disappeared GSA 7.0.2.
Furthermore a short note on the CVE topic:
CVE is not the only measurement for vulnerabilities. And if you e.g. check Android CVEs you will see for example 1.5k CVEs which are just outside of the coverage of a security scanner like Nessus or OpenVAS. Not talking about tons of exotic software where a CVE was assigned but which will never arrive in the database of a security scanner.
Don’t know where do you get these news from but nevertheless this is completely wrong. OpenVAS is still and will be free software. Why should we switch from an insufficient and unknown development platform at wald.intevation.de to make it private at the biggest, well-known and contributor friendly platform github? I really don’t get that. Please subscribe to our mailing lists to get informed about ongoing processes in OpenVAS and don’t make such statements in public. Greenbone isn’t going to make OpenVAS private in any way. Greenbone has been founded as a free software company and will stay as a free software company. And if you are unsure about the differences between OpenVAS and the Greenbone products please take a look at https://www.greenbone.net/en/community-edition/
As already stated you are also comparing different branches of GSA. GSA master will become the next version and completely differs from the latest release 7.0.2. We have rewritten the GSA web interface in master to be a single page application. Comparing master with an old branch doesn’t make sense anymore.
> Find a comparable solution without licensing by IP addresses, with powerful API, with good scanning
> quality and reasonable fixed per year price. At the moment I do not know of any solution comparable to
> Nessus in functionality. But I believe it is possible to do something similar based on OpenVAS. Interested
> in this kind of solution? Please let me know.
This should be interesting indeed, and how this could be taken forward.
I am messing with gvm-tools and the python api for some fun.
But this could really be interesting with a flask frontend perhaps…
Well, I dunno, first day @work after new years. So I still have some happiness left in me 😀
Pingback: Tenable Security killed Nessus Manager and anounced Tenable.io On-Prem | Alexander V. Leonov
If you’re a PCI shop, then you need to find a solution that is a registered ASV solution, so you can get your PCI scans. For that, there are cloud based subscriptions that do a really good job (Trustwave for ~$500, HackerGuardian might be free if you buy certs from them). I’m sure there are others. Then it’s just a matter of finding a decent scanning product that can do network, host and cloud (i.e. AWS) scans. It seems as if Nessus is architecting the “upgrade” as a way to force users to pay more, and for me, that’s not cool and is reason for me to look for other solutions. On my list is Qualys and Rapid 7.
How about checking with F-Secure RADAR, It has all the ingredients with API and does Discovery, Internet discovery, system and web scan..I believe worth looking at.. also as mentioned by Jason, It is ASV too
Hi Arun!
I already reviewed it:
F-Secure Radar Vulnerability Management solution
F-Secure Radar basic reporting
F-Secure Radar ticketing
The only problem is licensing model.
Alexander,
And about Nessus Manager?
I subscribe, in 18′ January a lot of licences, and the API to extract results are the bigger winpoint to me. I received today a “alert” to update my Manager to v7, but, when I read the documentation, only founf about APIs on Nessus Professional. I’m afraid thinking if I wish or not update my Nessus Manager :/
Tenable is going to lose us as a customer without a doubt, as we use their API extensively.
We desperately need a good alternative.
You don’t have to upgrade to Nessus 7 till December 2018, which is when the Nessus 6 it will be end of life.
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov
Pingback: Potential RCE in Nessus 7 and attacks on Vulnerability Scanners | Alexander V. Leonov
I have been looking into alternatives ever since the announcement of the loss of API. We tested Rapid7 and wanted to test Tenable.io (We have a need to not store any VM data into the cloud). The main sticking point is price, either product exceeds 100K US for the scans. I am wondering if we can use Nessus Professional 7, export the data to XML and import the data into Kenna. https://github.com/tenable/nessrest and https://avleonov.com/2018/02/15/kenna-security-connectors-and-rest-api/#comments
Check nvanalyzer.com for a solution that allows scan analysis and comparison.
Im new into the field of consulting. Prior worked with Qualys VM/PC/WAS, etc and im very interested on Nessus Professional.
Digging on information about the new version of Nessus Pro, saw this post and have some doubts about the decision to buy it.
My purpose is to offer Vulnerability Assesments as a service to several clients. So, 1) nessus professional is the right choose? 2) Can I do external scans (facinng internet IPS) with Nessus pro? 3) Can I make o365 scans? 4) What are the things that all loose on the new version and why are so important?
Pingback: What’s new in Nessus 8 | Alexander V. Leonov
My shop has been using Ness* Pro API for years now, doing security consulting and automated vulnerability scanning both on Internet and internal networks. We have decided to ditch Ness* altogeather, regardless of what they may do. Their business tactics are untrustworthy and they are all about $$$ now.
We have been playing around with OpenVAS API python and gvm-tools with very promising results.
In comparison to Ness* I’d say OpenVas is “almost as good” NVT-wise, some NVTs need polishing.
API wise, OpenVAS is way better than Ness*, giving you complete control of most all aspects of the scanner and data. Ness* API gave less control in our experience. OpenVas installations can be fragile and must be done with extreme care. When you get past that, all is bright.
We are not worried about Greenbone closing the source on Greenbone/OpenVAS code as that is protected by GPLs, which has already been affirmed in a court of law. If they try, we or anyone, can and will sue them.
As a result of our experiment we have decided to join with Greenbone on Github in maintaining and developing the OpenVas code and NVTs. I urge all in here who can to do the same.
Pingback: Parsing Nessus v2 XML reports with python | Alexander V. Leonov