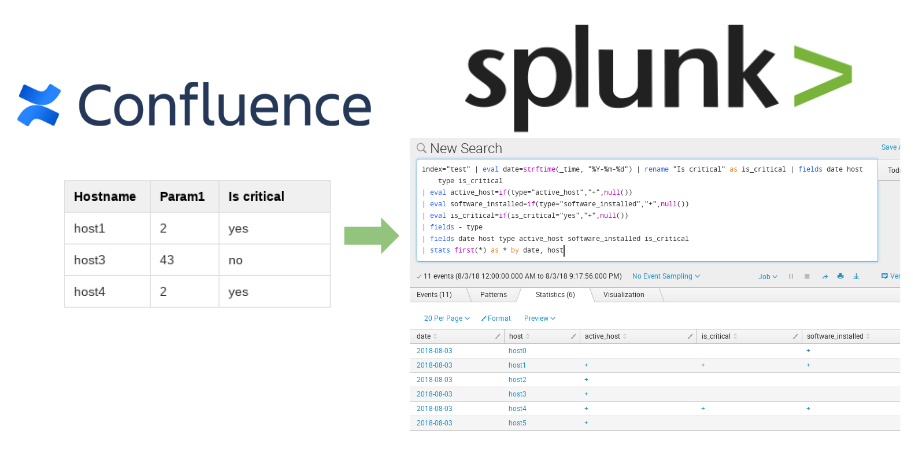
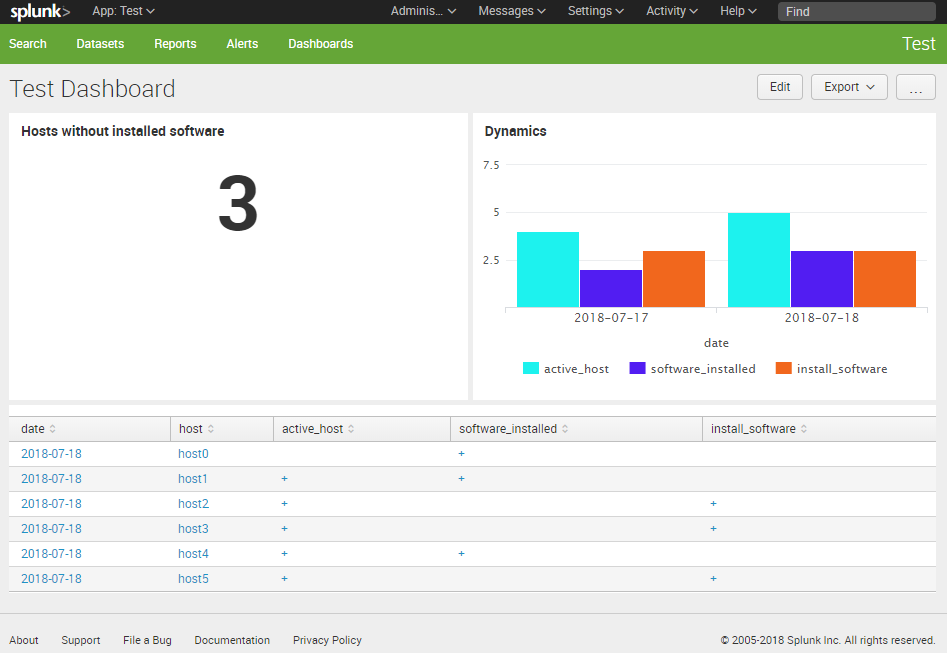
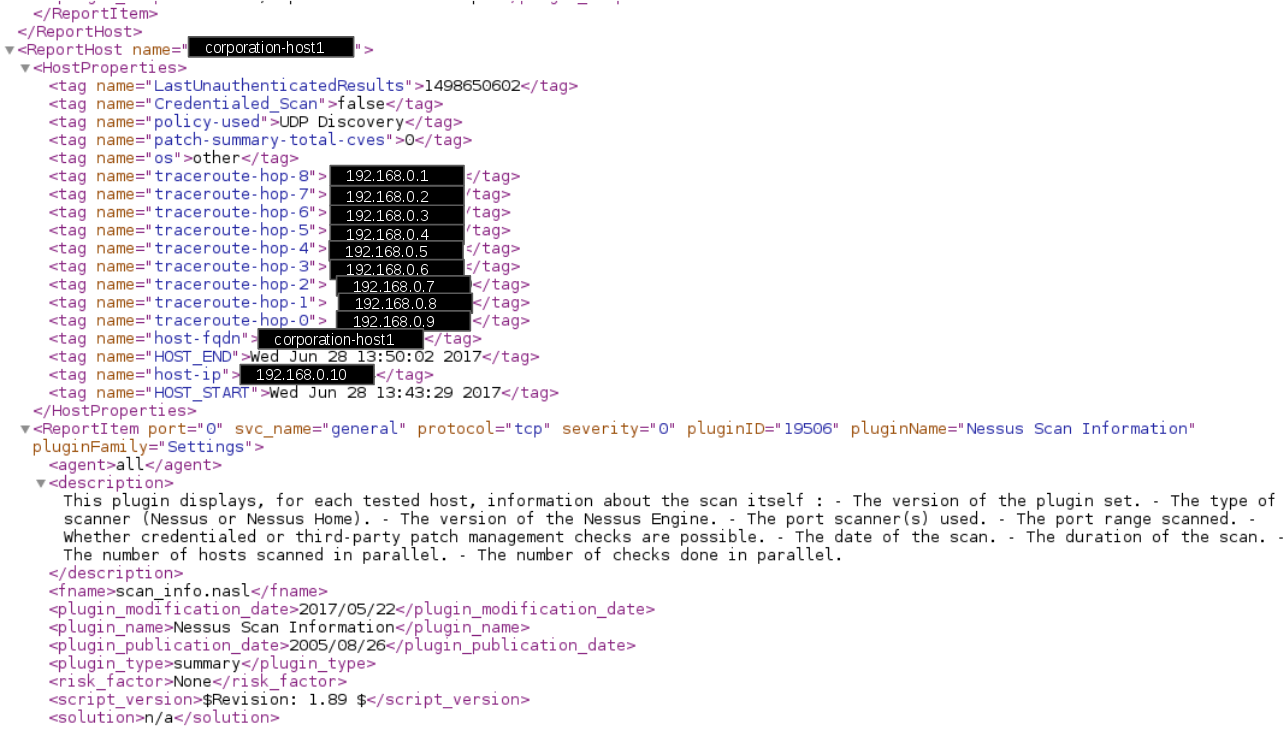
Kenna Security: Analyzing Vulnerability Scan data. I’ve been following Kenna Security (before 2015 Risk I/O) for a pretty long time. Mainly, because they do the things I do on a daily basis: analyse various vulnerability scan results and feeds, and prioritize detected vulnerabilities for further mitigation. The only difference is that my scripts and reports are highly specific for my employer’s infrastructure and needs. And guys from Kenna team make a standardized scalable cloud solution that should be suitable for everyone.
I think their niche is really great. They do not compete directly with Vulnerability Management vendors. They can be partners with any of them, bringing additional features to the customers. Perfect win-win combination. That’s why Kenna speakers regularly participate in joint webinars with VM vendors.
I couldn’t lose a great opportunity to see Kenna Security service in action. 😉
In this post I will try to make a very brief review of Kenna functionality and formulate pros and cons of the solution.
When you submit trial request at https://www.eu.kennasecurity.com/signup (or https://app.kennasecurity.com/signup if you are not in Europe) you will get a link to your company account:
https://corporation.eu.kennasecurity.com/
The login screen will look like this:

Continue reading →