Vulners.com search API. Upd. Vulners released updated Vulners API. What is written below is still working. But now it’s all this can be done much easier.
The greatest thing is “references=true”. It makes possible to get all the referenced objects (exploits, detection plugins, etc.) and bulletin description in ONE search request.
So, for example bellow this query will be enough: https://vulners.com/api/v3/search/lucene/?query=cvss.score:10%20type:centos%20order:published&references=true
Life is getting better! 😉
In a previous post I made a brief review of Vulners.com security content database and search engine. Today let’s see how to automate searching of vulnerabilities, exploits, patches, bugbounty results, etc, with vulners.com search API.

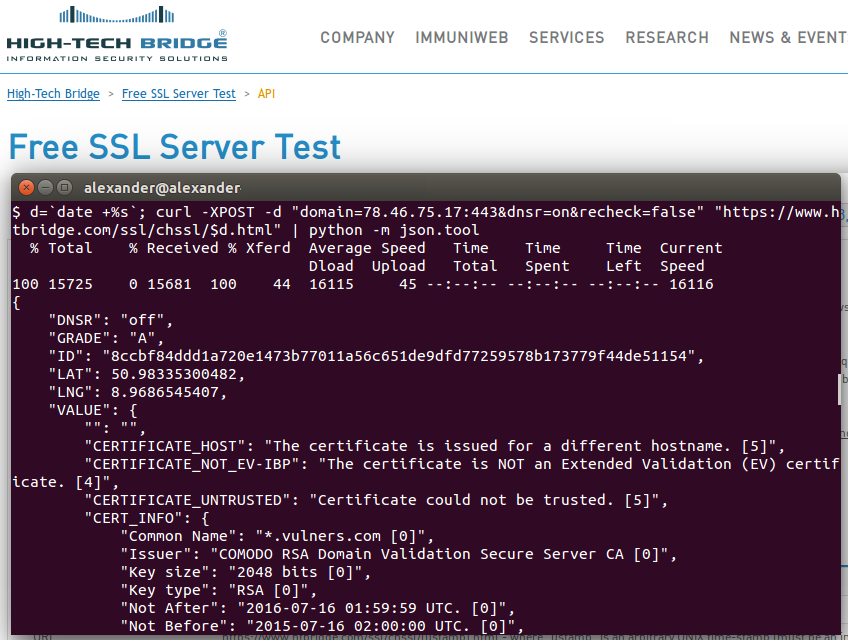
It is really easy. We just need to send POST-request to https://vulners.com/api/v1/luceneSearch/ with JSON structure containing search query, size of results you want to get (10000 is maximum), and number of search result entities you would like to skip (optional). Huge size parameter limit makes possible, for example, getting all 2267 CentOS security bulletins with only one request. At the moment, no authorization is required to make requests and no limits for API use exist. Of course, the service is in active development phase and this functionality may be changed soon.
So, let’s get latest CentOS bulletin with most critical vulnerability:
curl -H "Content-Type: application/json" -X POST -d '{"query":"cvss.score:10 type:centos order:published", "size":1}' https://vulners.com/api/v1/luceneSearch/ | python -m json.tool
Continue reading →