New episode “In the Trend of VM” (#12): 8 February CVEs & Why the Darknet Matters for VM Specialists. Now with a new design and new video editing. 😉
📹 Video on YouTube and LinkedIn
🗞 Post on Habr (rus)
🗒 Digest on the PT website
Content:
🔻 00:00 Greetings
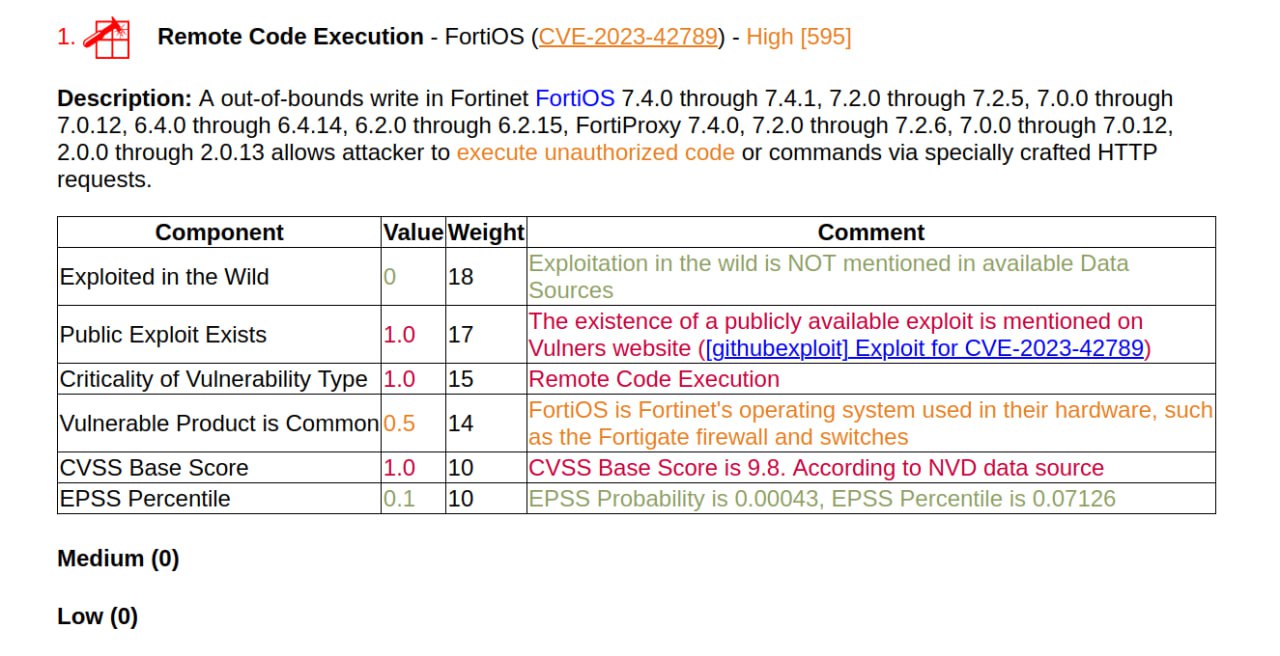
🔻 00:23 Remote Code Execution – Windows Lightweight Directory Access Protocol (LDAP) (CVE-2024-49112)
🔻 01:35 Remote Code Execution – Microsoft Configuration Manager (CVE-2024-43468)
🔻 02:38 Remote Code Execution – Windows OLE (CVE-2025-21298)
🔻 03:55 Elevation of Privilege – Windows Hyper-V NT Kernel Integration VSP (CVE-2025-21333, CVE-2025-21334, CVE-2025-21335)
🔻 05:02 Authentication Bypass – FortiOS/FortiProxy (CVE-2024-55591)
🔻 06:16 Remote Code Execution – 7-Zip (CVE-2025-0411)
🔻 07:27 Should a VM specialist be aware of what is happening in the Darknet?
🔻 08:48 About the digest of trending vulnerabilities