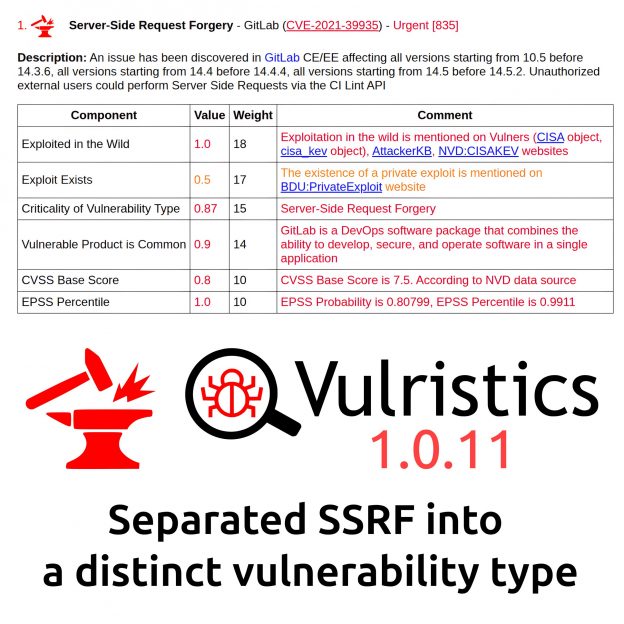
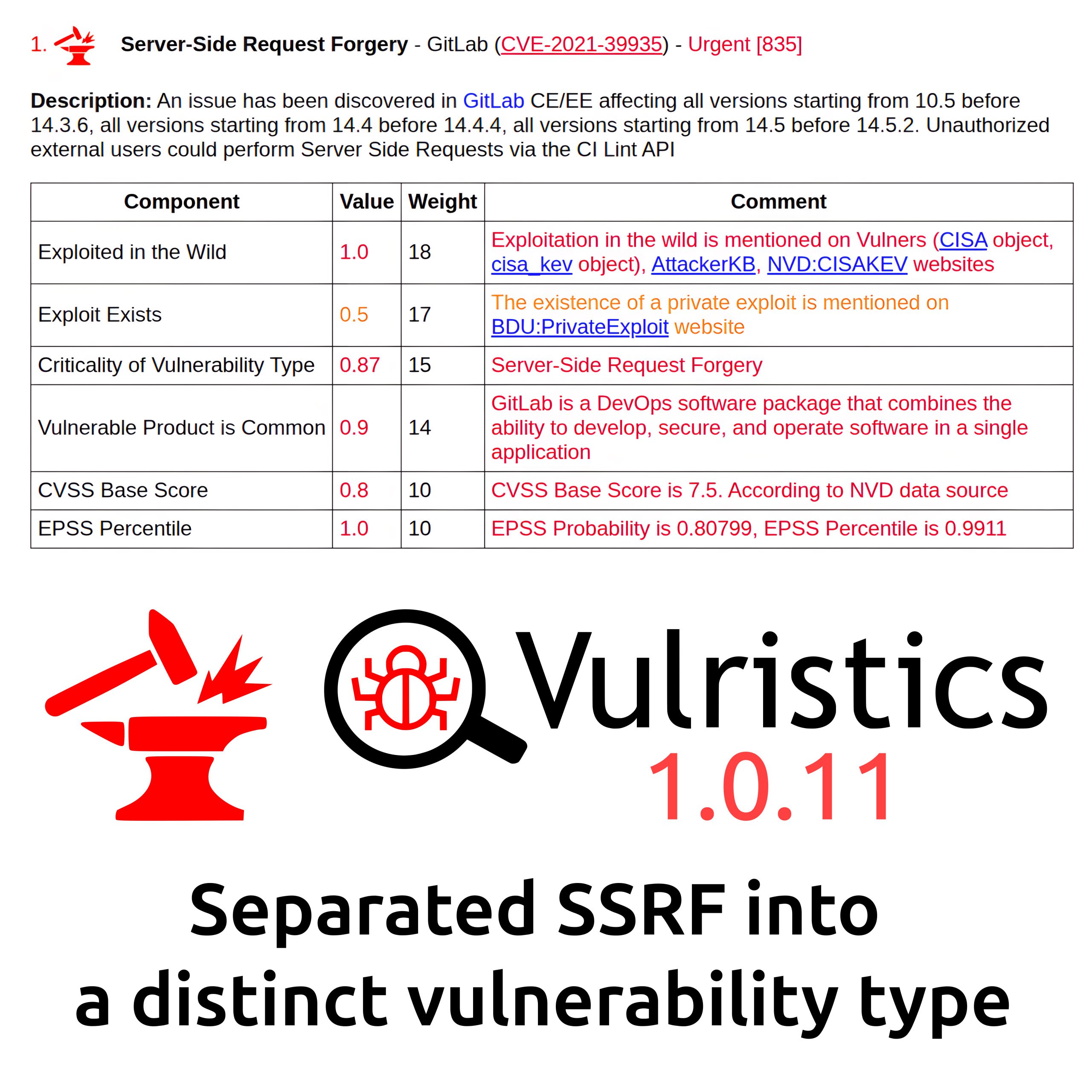
About Remote Code Execution – Microsoft Word (CVE-2026-21514) vulnerability. This vulnerability is from February Microsoft Patch Tuesday. Reliance on Untrusted Inputs in a Security Decision (CWE-807) in Microsoft Office Word allows an unauthenticated attacker to bypass OLE security features when opening a malicious file. The vulnerability is NOT exploitable via the Preview Pane.
👾 Microsoft reports that the vulnerability is being exploited in the wild. It has been listed in CISA KEV since February 10.
💬 Microsoft has classified the vulnerability as a Security Feature Bypass, but given that exploiting such vulnerabilities can lead to arbitrary code execution, it seems reasonable to classify it as Remote Code Execution, similar to the actively exploited CVE-2026-21509.
🛠 No public exploits are available yet.