Why Asset Management is so important for Vulnerability Management and Infrastructure Security? When people ask me how should they start building Vulnerability Management process in their organization (well, sometimes it happens), I advice them to create an effective Asset Management process first. Because it’s the foundation of the whole Infrastructure Security.
The term “Asset Management” has different meanings and if you start to google it, you will get some results related mainly to finance sphere. I use this term as Qualys and Tenable. For me Asset Management is the process of dealing with network hosts.
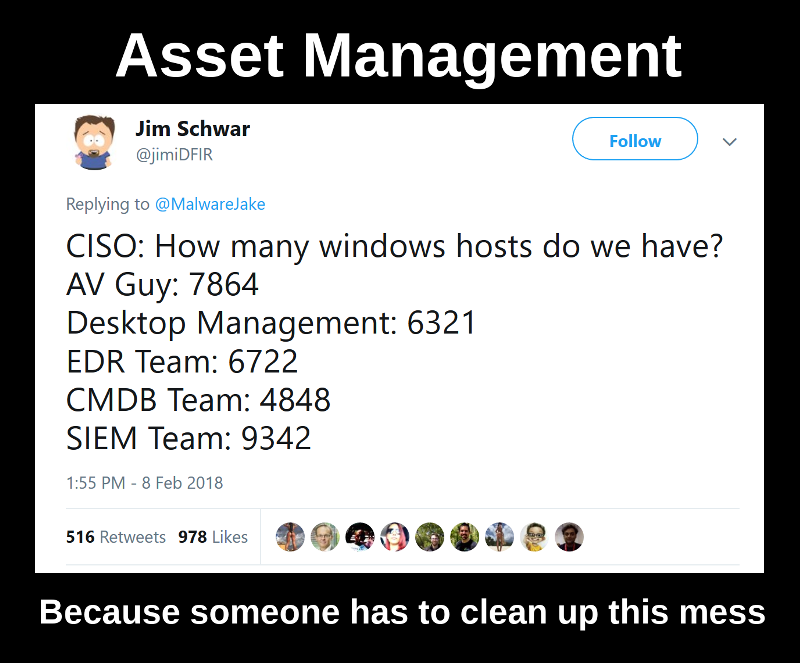
So, what should you do in situation described in the tweet above, when you don’t know exactly how many Windows hosts you have in your corporate IT environment? And, more importantly, why do you need to know?
The role of Asset Management in Infrastructure Security
Well, starting with the second question, without knowing your hosts it’s very hard to implement Security Measures for protecting your IT infrastructure. Even the most basic of them:
- install agents for Endpoint Security, Antivirus and DLP
- configure log collection for SIEM
- make security hardening
- perform regular Vulnerability Assessment
For each of these measures you will need to know:
- all the hosts that need to be affected by Security Measure
- all the hosts where Security Measure is already implemented
- all the hosts where Security Measure is NOT implemented
- the current coverage for Security Measure in the organization
- the current state of Security Measure in the organization
- the dynamics and plans for Security Measure implementation
Simply put, you need to see what is already done and what needs to be done. Without this, there will be many blind spots in the IT infrastructure, which can be an easy target for attackers. Moreover, it will be a pretty hard to show your managers that you are actually doing your job well, if you can’t provide any measurable results. 😉
So, how many Windows hosts do we have?
Of course, the picture above is a joke. However, this situation is typical. In real life it makes sense to:
- Intercept the host sets from the different datasources (AV Management Servers, Desktop Management system, Endpoint Detection systems, CMDB, SIEM, LDAP, IT Monitoring systems, etc; the actual set of inputs depends on what is in use in the particular organization).
- Go nuts by seeing all kinds of differences. 😉
- Stimulate the teams to add new hosts to their systems and try to automate these actions.
If you have such differences, this probably means that the logs are not collected from every host, agents are not installed on every host, some domains, some offices or some datacenters were forgotten. Ideally, everything should be the same everywhere. And not only for Windows hosts.
Practically speaking, in a similar situation I send all the data to Splunk using custom HTTP Event collectors for further analysis and demonstrate statistics about the hosts on dashboards. If there are any anomalies (host should exist in some data source, but in fact it doesn’t), I send the alerts to the owner of the datasource for investigation. I also use this system to manage Vulnerability Assessment process.
Of course, the ideal is unattainable, but when we start to measure the current situation, the mess decreases and the real security level increases drastically.
Why should we analyze various datasourses if we already have a Network Scanner?
Some might say that port scanning is enough for host discovery and we don’t need to analyse various datasources, including those that are maintained by IT teams. But, IMHO, the active unauthenticated scanning is the dumbest way for Asset Discovery.
- It takes too much time to run on a huge networks (discovering all open TCP and most used UDP ports).
- It creates unnecessary load on network devices and target hosts and can break the servers (see my previous post “Can a Vulnerability Scan break servers and services?“).
- It’s unreliable, because you never know if the host is inactive or you have problems with network access, or the host answers you very-very slowly and has some rare service on some rare port.
I also criticized it in my post “Asset Inventory for Internal Network: problems with Active Scanning and advantages of Splunk” and it’s not just me, read this page about Netbox “Why Doesn’t NetBox Scan for IPs?“.
Active unauthenticated scanning is a good way to detect shadow IT infrastructure, that couldn’t be spotted other ways. It’s good to have such scans as one of the sources for Asset Management. But I don’t think that it should the main and only Asset Discovery method as most of the Vulnerability Management vendors do. Especially if you have ipv6 networks, where you technically can’t make the detection scans.
What information you need about the Assets?
It’s not enough to see the active host. You must get minimal information about the host to understand what Security Policies and Security Measures should be implemented for it:
- Hostname
- IP address
- OS (Operating System)
- OS Vendor
- Project where it is used
- Owner
- Scope(s)
The most important is the Owner, who should approve the implementation of the Security Measure or implement it by himself and provide additional data that we need.
Who should make such Asset Management system?
As I already wrote in the post with the requirements to Asset Inventory systems, the best scenario if a robust Asset Management is provided by IT department. Or at least if they have a will to make the system that knows about all the hosts in the organization. It’s much better to be just a consumer of this data and some times report system anomalies than to build Asset Management system on your own.
But, as practice shows, in most cases IT security team will be the most interested in keeping asset data up to date. If IT team doesn’t want to provide such system for some reason, it will be necessary to collect and analyze all the information by Vulnerability Management team.
An overwhelming task?
Some might say that Asset Management is too complicated to do it organization wide. And it can be true. That’s why you may need start with the most Critical Assets. But how to get the list of such assets and constantly update them? It’s a topic for another post. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Great post Alexander, I’ve been doing a little research on this topic myself recently for a client I work with and your view on differnt ways to collect the data has helped stir some additional thought. I certainly agree that the asset/application owner is key for change, problem and any incident management.
Pingback: Vulnerability Management vendors and Vulnerability Remediation problems | Alexander V. Leonov
Pingback: Code IB 2019: Vulnerability Management Masterclass | Alexander V. Leonov
Pingback: PHDays 9: new methods of Vulnerability Prioritization in Vulnerability Management products | Alexander V. Leonov
Pingback: Big Microsoft day: EOL for Win7, Win2008 and crypt32.dll | Alexander V. Leonov