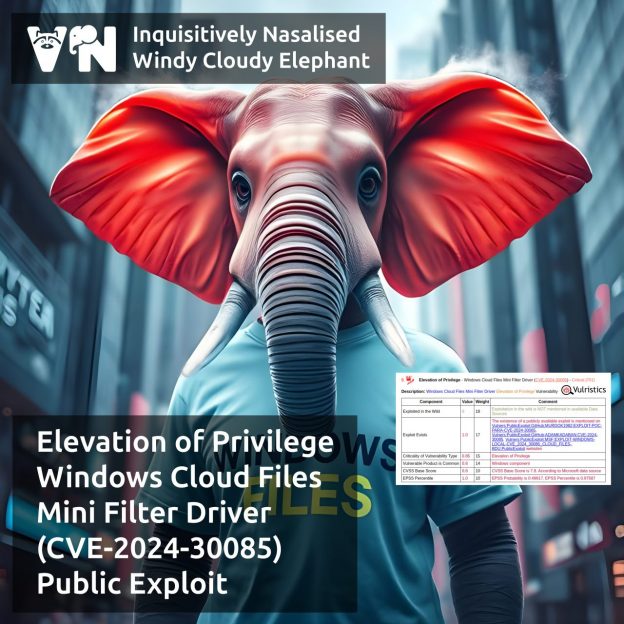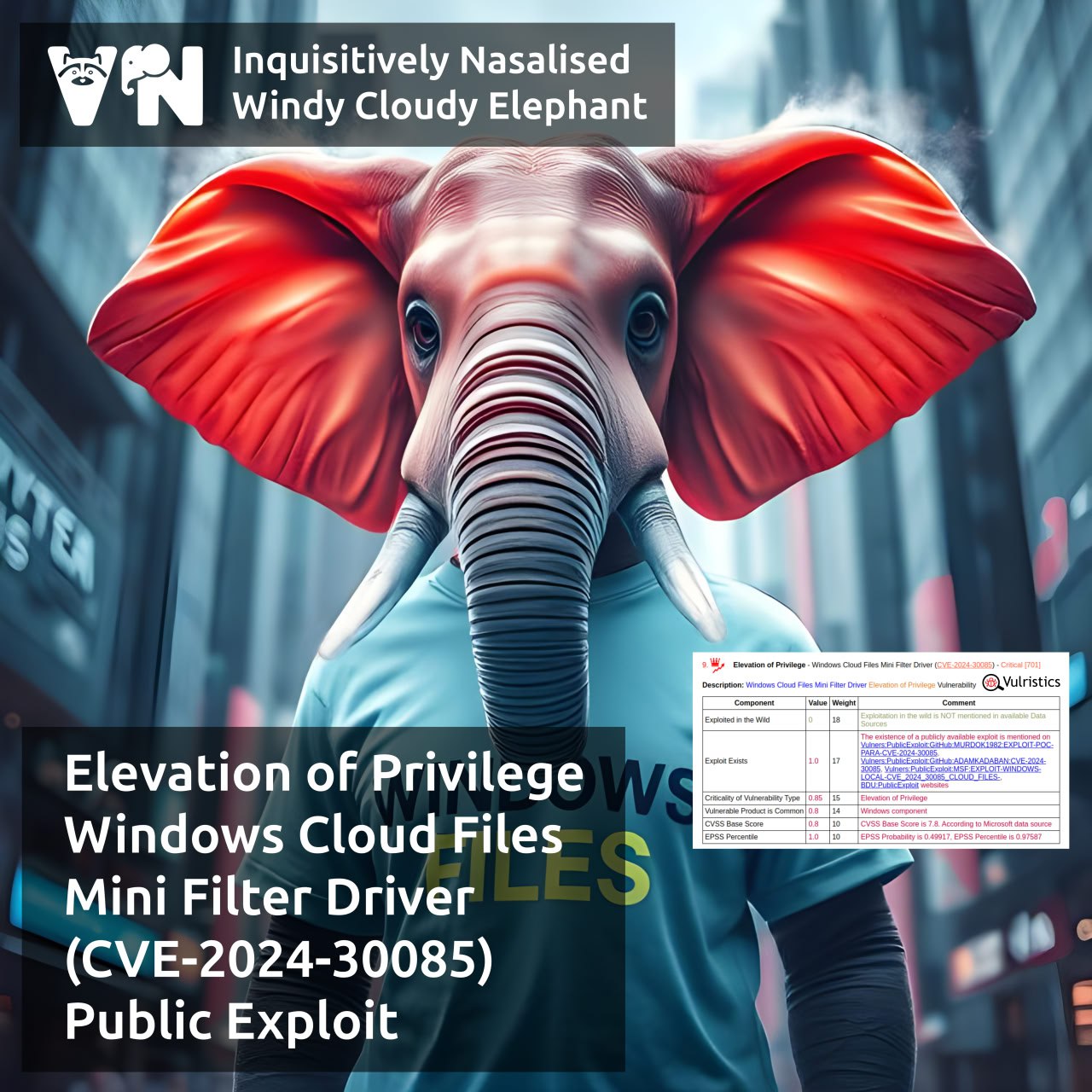
About Elevation of Privilege – Windows Cloud Files Mini Filter Driver (CVE-2024-30085) vulnerability. cldflt.sys is a Windows Cloud Files Mini Filter driver responsible for representing cloud-stored files and folders as if they were located on the local machine. The vulnerability in this driver, fixed as part of the June 2024 Microsoft Patch Tuesday, allows an attacker to gain SYSTEM privileges. The root cause of the vulnerability is a Heap-based Buffer Overflow (CWE-122).
🔻 A private exploit was presented at the TyphoonPWN 2024 competition on May 30, 2024. It was used as part of an exploit chain to achieve a VMware Workstation Guest-to-Host escape.
🔻 On December 19, 2024, a technical write-up and exploit code were published on the SSD Secure Disclosure website.
🔻 On March 3, a blog post by Positive Technologies was published that examines the roots of the vulnerability and exploitation techniques.