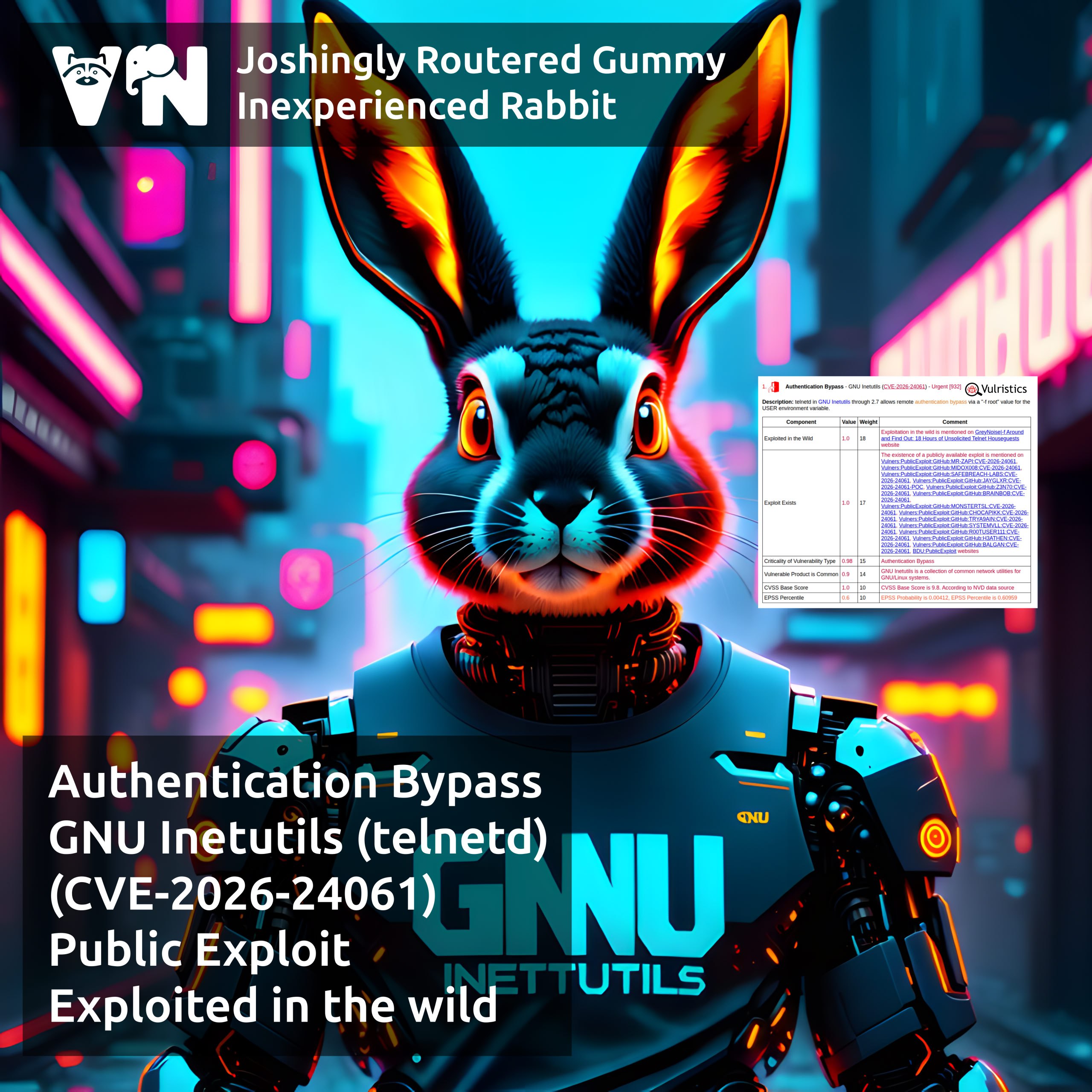
About Authentication Bypass – GNU Inetutils (CVE-2026-24061) vulnerability. GNU Inetutils is a collection of common network programs, including, among other things, a Telnet server (telnetd). A vulnerability in GNU Inetutils telnetd allows a remote attacker to obtain a root shell on the host without any credentials by sending a crafted USER environment variable containing the value “-f root”.
⚙️ A patch fixing the vulnerability was released on January 20. Versions 1.9.3–2.7 are vulnerable; the issue went undisclosed for 10+ years. 🤷♂️
🛠 A detailed write-up and exploit were published by SafeBreach on January 22.
👾 Exploitation in the wild has been observed by GreyNoise since January 21.
🌐 Shodan estimates ~212,396 Telnet servers online in total. How many of them use GNU Inetutils and are vulnerable is still unclear. CyberOK discovered around 500 potentially vulnerable Telnet servers in the Russian Internet segment.