CyberCentral Summit 2018 in Prague. Almost whole last week I spent in Prague at CyberCentral conference. It was a pretty unique experience for me. I was for the first time at the International conference as a speaker. And not only I presented my report there, but lead the round table on Vulnerability Management and participated in a panel session.

From my point of view, everything was pretty good. I successfully closed my gestalt on public speaking in English. I definitely can do it. 🙂
The event was hold in Lucerna passage right in a center of Prague. Beautiful building in Art Nouveau style with famous ironic “Statue of King Wenceslas Riding an Upside-Down Dead Horse”. 🙂
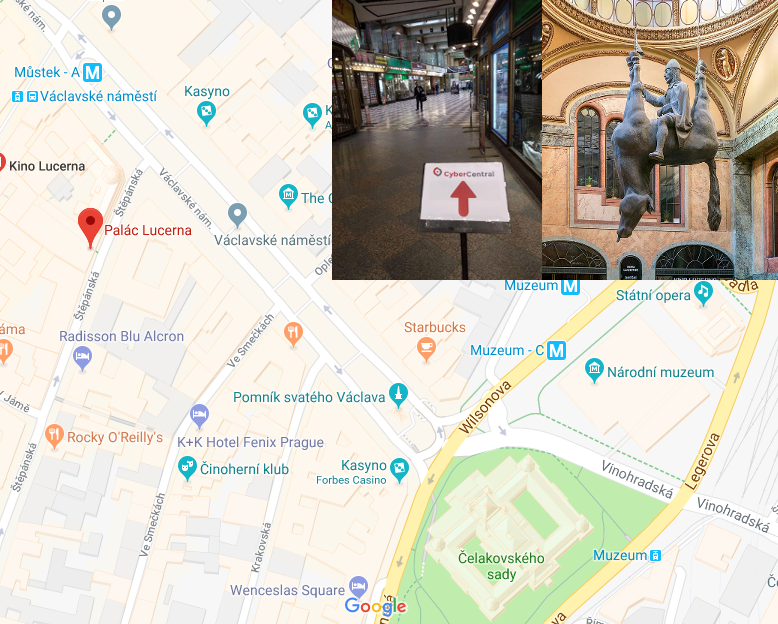
Even to speak in this building was a great honor. In my opinion the place was chosen ideally. It is beautiful and really good located. Lots of good hotels, restaurants and all main tourist attractions were in nearby. It was easy to go for a walk in a spare time.
Day 0
First pre-conference day I spent at the Application Security training by Milan Pikula, Security Analyst Lead at SK-CERT. He demonstrated how to exploit some basic web application vulnerabilities and use methods of binary analysis. It was possible to give it a try: all vulnerable applications were available for the audience.

I need to say that the Small Lucerna cinema Hall is very comfortable for such trainings. In every chair there was a built-in small table for the laptop and a power socket.
At the evening we had a great dinner for the speakers at the Výtopna Restaurant. Great feature of this restaurant is the functional railroad that goes right on the tables and the small trains serve drinks to the customers. 🙂 Food was also pretty good.

CyberCentral is not a very big conference, comparing to the main Russian events for security practitioners: PHDays and ZeroNights. At the same time it is an advantage. It’s much better for networking. Everyone in sight, everyone is available for a talk.
The important reason to visit European information security events is that you can meet there people who do not attend Russian international conferences. Moscow is a little bit far away for them and it’s necessary to get visa. It’s much easier to meet in one of the European countries. By the way, despite the fact that the conference was held in the Czech Republic, most of the attendees were from neighboring Slovakia. There were also many people from Germany, Great Britain and the Balkan countries. And practically from all other corners of Europe.
Day 1
At the first day of the conference I can mention great presentation of Marco Ermini,
Senior Security Architect Hosts & Networks at Telefonica O2. He was talking how security risks and threats are connected with merger and acquisition activities. I especially liked the second part of his presentation. It was OSINT tools. I had some experience in Competitive Analysis and used similar techniques for getting information about different organisations from the publicly available data.
At the same day I lead the round table on Vulnerability Management. Networking was pretty fun. 5 people participated. We discussed Tenable and other VM vendors, who drag everything into their clouds. ^_^ We also talked about compliance scanning, GDPR and about life in our countries.
Day 2
The second day was THE day for me. First of all, I presented my report “Enterprise Vulnerability Management: fancy marketing brochures and the real-life troubles”.


You can see slides at Slideshare:
I was preparing this presentation since October 2017 and partly shown it at ISACA Moscow meetup. Of course, for CyberCenter I updated it a lot: added research on CWE, Nessus exploits, IDC and Forrester marketing reports, the latest problems with Nessus and OpenVAS. I also spoke a little bit about my vulnerability scanner Vulchain and added wonderful examples of patching problems related to the latest Specter and Meltdown vulnerabilities.
Finally, I’ve got this presentation plan:
- Typical VM Solution
- Inconvenient Questions
- What actually should we scan?
- Perimeter
- Office
- Business critical / Production
- VM Analyst’s Heaven and Hell
- Vulnerability Management Market
- Outrageously expensive solutions
- Limited license = Limited IT Visibility
- The end of cost-effective VM (Nessus 7)
- OpenVAS “Attic Cleanup”
- What about your own scanner?
- All Vulnerability Scanners are the same?
- Reports: problem of prioritization
- Dynamic reports
- Why *they* don’t patch vulnerabilities
- It’s great when you can update OS automatically, but…
- Something can break after update
- Update can make situation even worse (Spectre and Meltdown)
- The Neverending story of 3d party software patching
- Fifty Shades of Legacy
- Some systems are just difficult to update
And made the following conclusions:
- There is no magic in Vulnerability Management
- Vulnerability scanners are awesome. Trust them, but not too much.
- Homegrown automation is still necessary:
- Update scan targets (Wiki, DNS, WAF/AntiDDoS, AD, Monitorings…) and manage regular scan tasks
- Get critical exploitable vulnerabilities from scan results
- Inform responsible person / make tasks
- Get statistics and visualize VM process
In the Q&A section, we talked very nicely about problems of detecting vulnerabilities in self-assembled software packages and about backported patches. Also there were interesting questions about Vulchain and the detection methods that it currently uses. ^ _ ^
In the same technical stream I liked 2 presentations:
- First one, “Regulations vs. actual security. The bottom line.” by Viktor Larionov, Director Of Operations at Nordicore Operations Ltd. He was talking about regulators who always check the documents and not the servers. I am working on actual security and naturally I would like to see more server checks during such audits.
- The second one is “Building Great SOC & CSIRT from Open-source Components” by Milan Pikula, Security Analyst Lead at SK-CERT. It was especially interesting what they use for Vulnerability Management. For example, I learned about Taranis project. Here is a slide with the main SOC components:

Then I was participating in “International Panel on Worldwide Trends”. It was the last talk of the event.

The plenary session also went well:
- We talked about the trends. I said that nothing fundamentally new is happening. The waste majority of cases that we all have seen recently happened because people do not patch their systems on perimeter (Equifax and Apache Struts), in internal network (Windows, WannaCry, Petya, etc.) or do not make minimal hardening (Cisco Smart Install). And as long as people don’t pay much attention to Vulnerability and Patch Management there will be lots of such massive attacks.
- Then we talked about awareness. I said that training of the employees is wonderful, but we shouldn’t forget to make effective minimization of privileges as our first priority.
- The social problem of cybercrime also was discussed. Nothing new: whitehats and blackhats are grown from the same children. We should start working with them earlier: show how they can do what they really like to do while staying on the light side; how to earn money without risk of getting in jail.
It was very intense week. Lots of new connections and interesting talks. Big thanks to the organizers, especially to Alexander Nevski, Cyber Security Program Director at EBCG, and all participants! It was awesome. =)

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Vulchain scan workflow and search queries | Alexander V. Leonov
Hi Alexander,
Thanks for your post.
Just one small correction, this “majority o cases” probably needs to be this “majority of cases”.
Cheers,
John
Hi John,
Thank you very much! Fixed. 😉
With best regards,
Alexander
Pingback: CISO Forum and the problems of Vulnerability Databases | Alexander V. Leonov
Pingback: MIPT/PhysTech guest lecture: Vulnerabilities, Money and People | Alexander V. Leonov