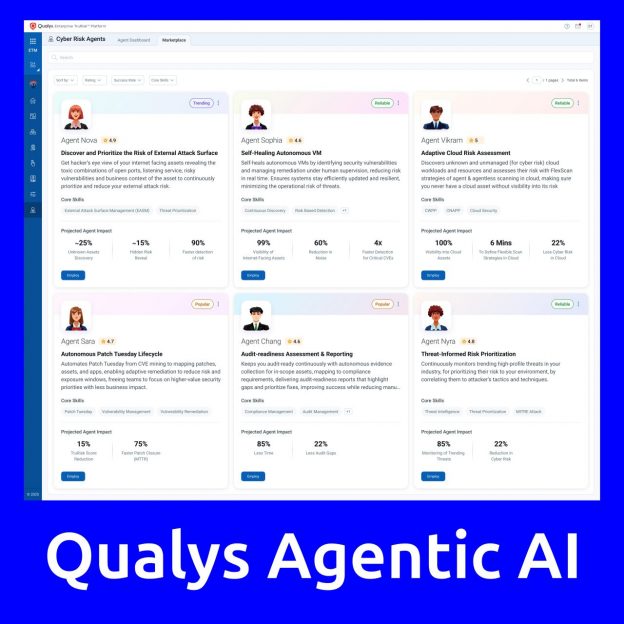
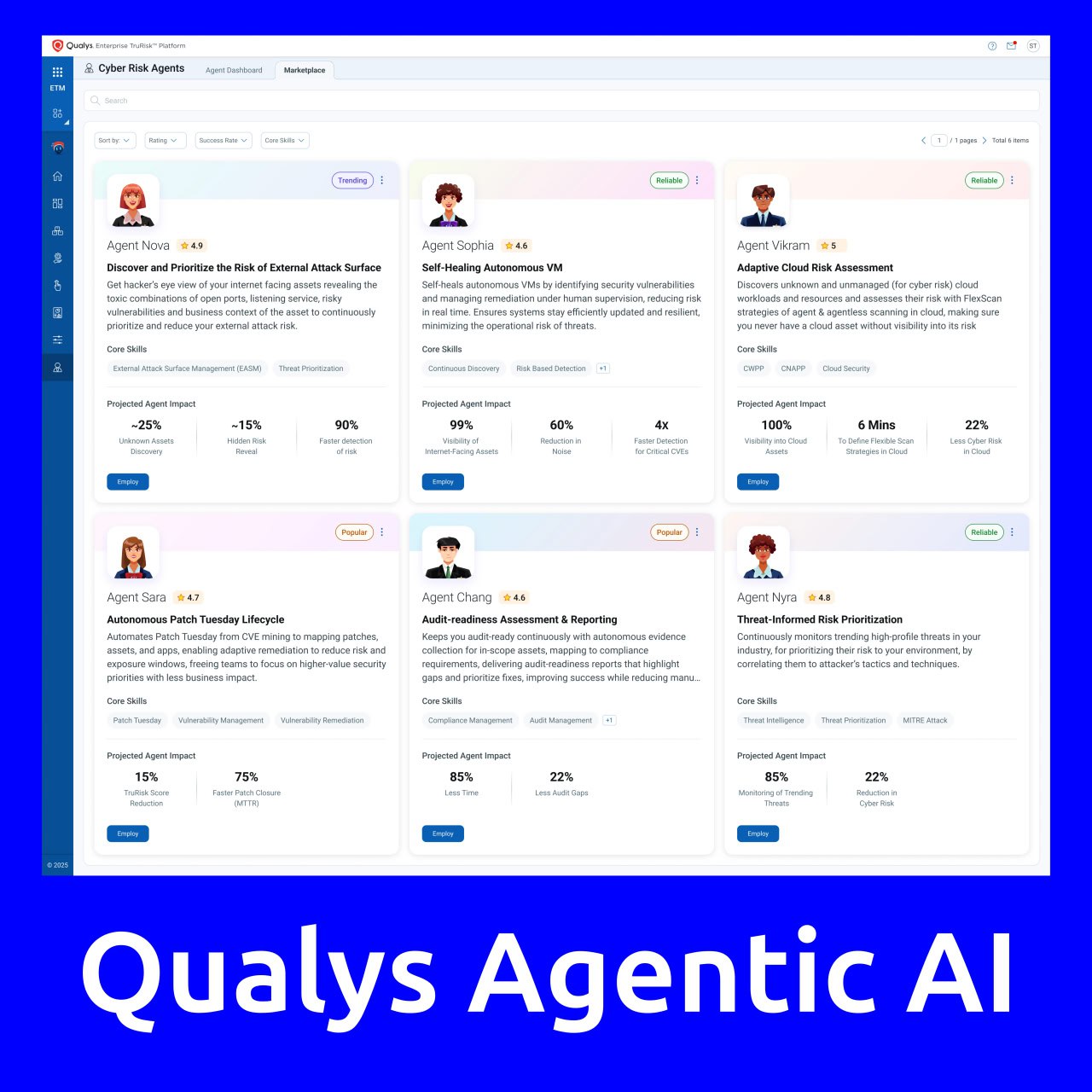
August “In the Trend of VM” (#18): vulnerabilities in Microsoft Windows and SharePoint. A traditional monthly roundup – this time, it’s extremely short.
🗞 Post on Habr (rus)
🗒 Digest on the PT website (rus)
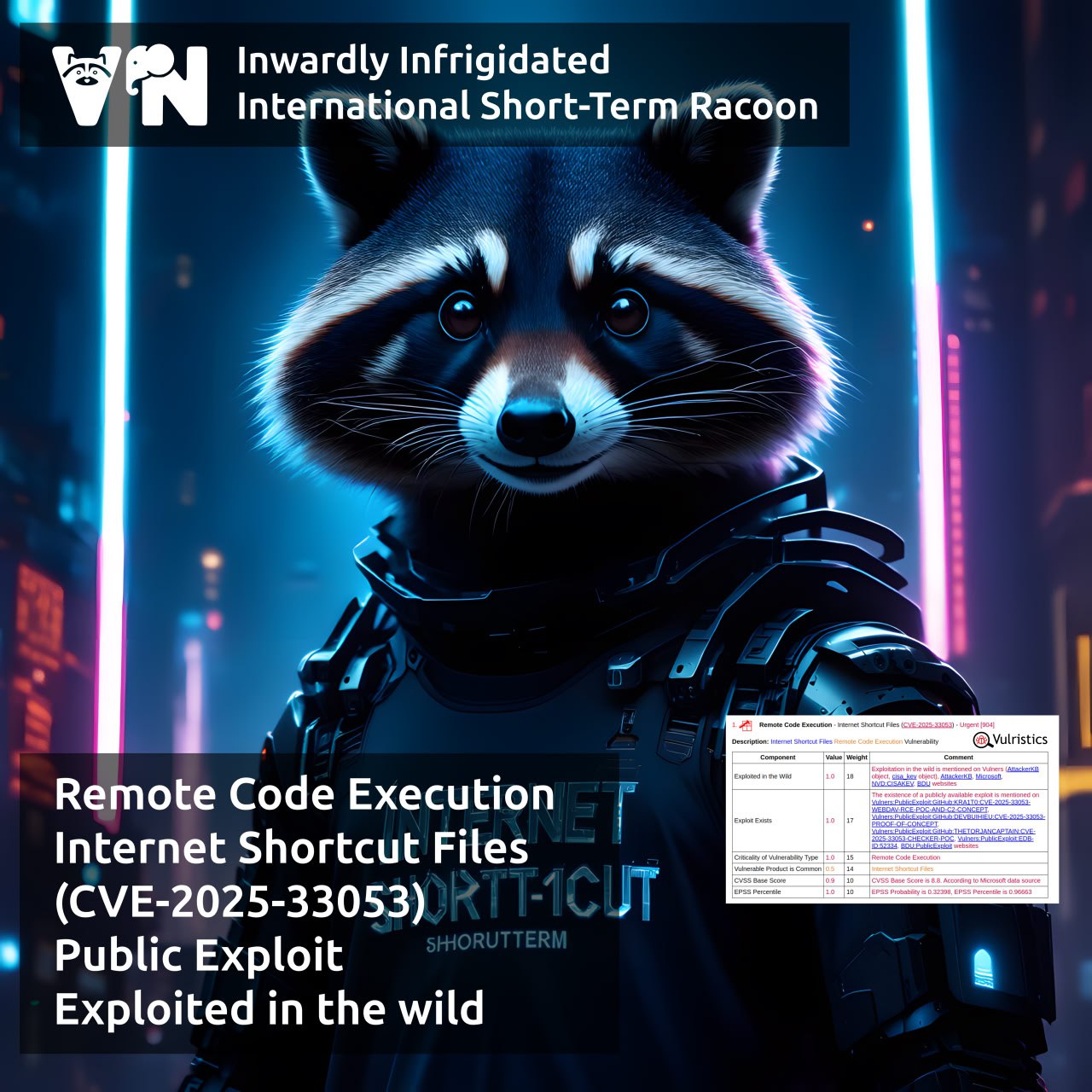
Only two trending vulnerabilities:
🔻 Remote Code Execution – Microsoft SharePoint Server “ToolShell” (CVE-2025-53770). The vulnerability is being widely exploited; attackers may even have gained access to U.S. nuclear secrets. The vulnerability is also relevant for Russia.
🔻 Elevation of Privilege – Windows Update Service (CVE-2025-48799). The vulnerability affects Windows 10/11 installations with at least two hard drives.