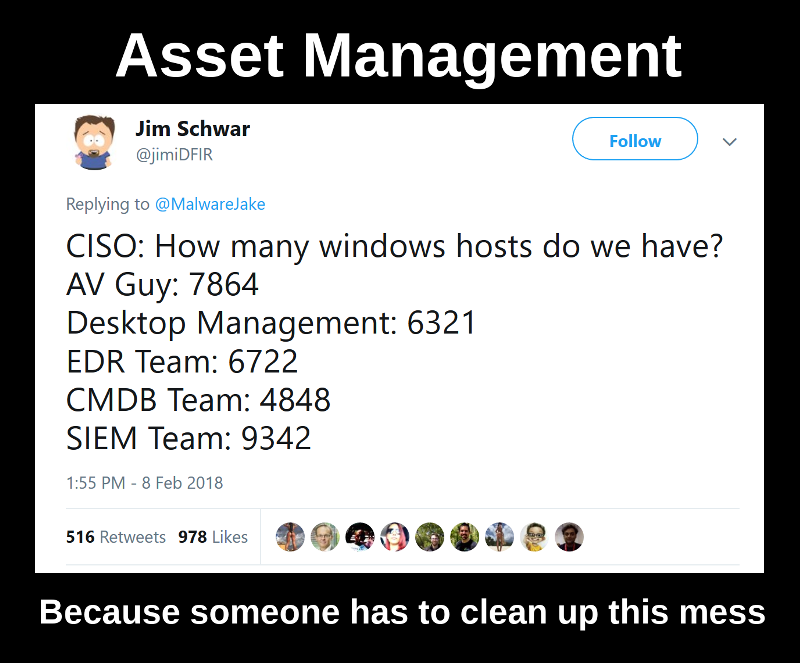
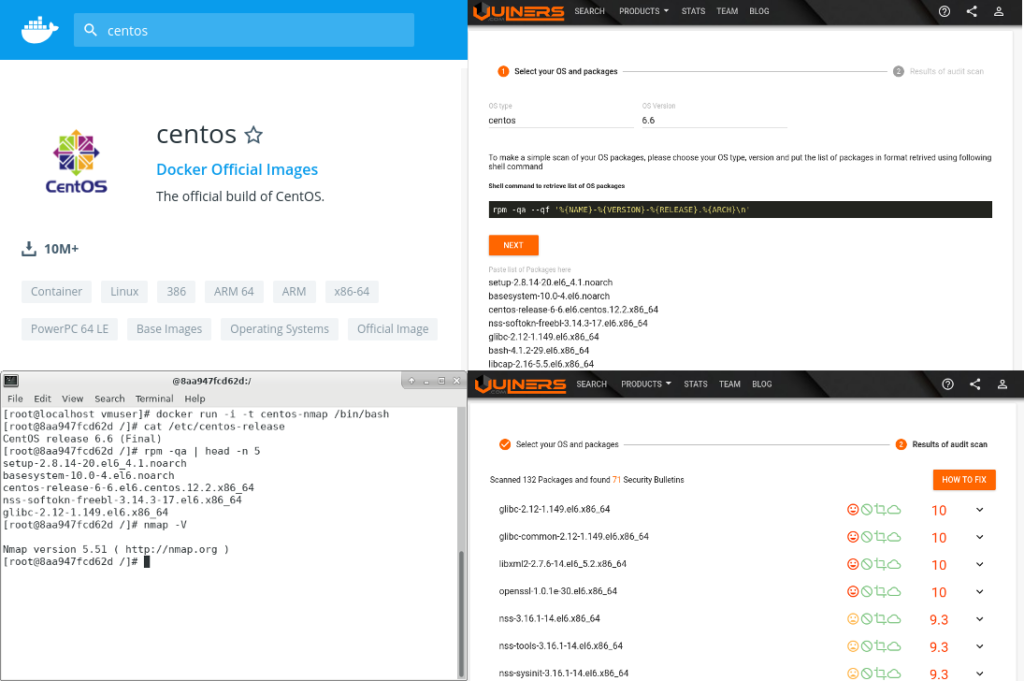
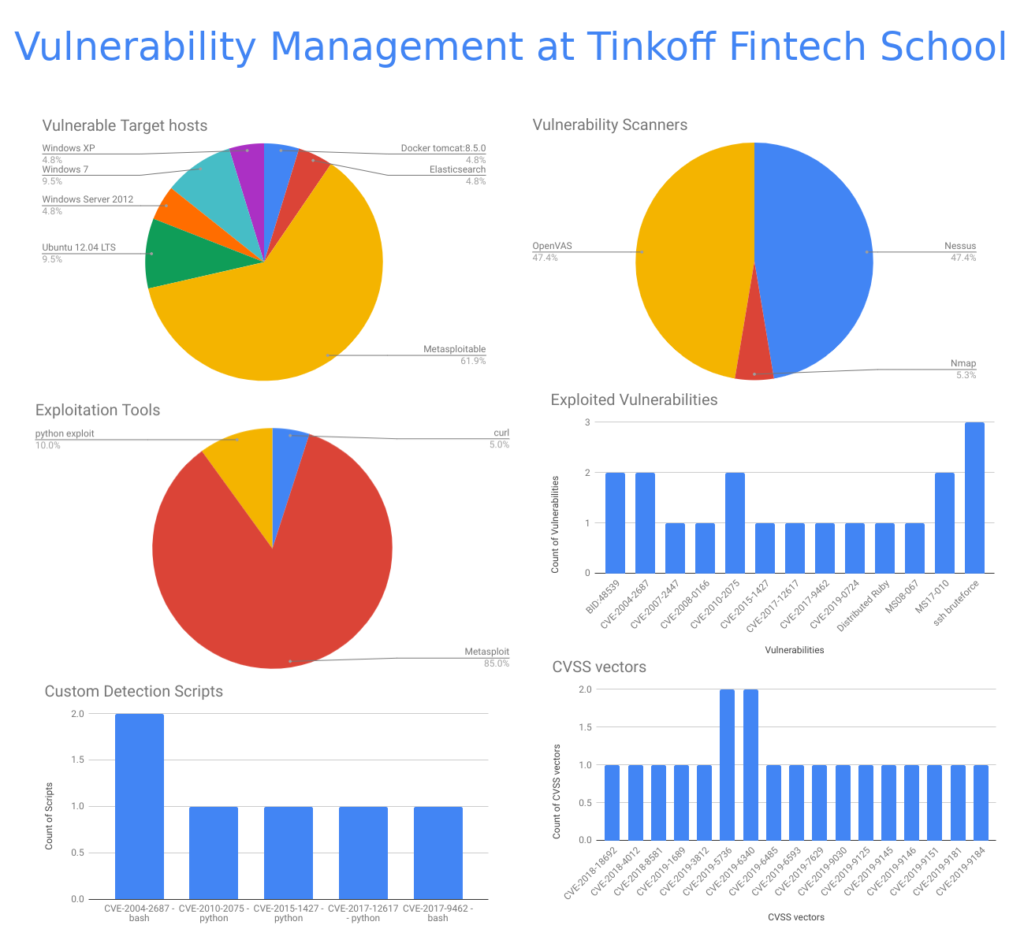
Code IB 2019: Vulnerability Management Masterclass. On March 29, I held one hour master class “HOW to avoid excessive formalism in Vulnerability Management process” at Code IB Profi 2019. Everything went quite well and I’ve got 88% positive ratings. Not bad result ^_^.

The main feature of the conference was a very special audience. The only way to visit this event was to buy a real ticket (there were no promotional codes, invites, free tickets from sponsors, etc.). So, the people who came were really interested in the content. Target audience: CISO, their deputies, leading experts from all industries. The whole event was up to 200 people, it lasted for 2 days with 4 threads of masterclasses.
This year organizers decided that titles of all masterclasses should start with “How to” (to keep them practical) and there should be checklists for each masterclass as a handout. I am going to translate my checklist Into English and publish it in this blog soon.
In fact, there were 2 masterclasses on Vulnerability Management at the conference! The second was held by Lev Paley. However, our content did not intersect: I spoke mostly about technical stuff (and I criticized VM vendors as usual), and he spoke mainly about the organizational part and high-level processes.