Qualys Option Profiles for Vulnerability Scanning. When I wrote about vulnerability scanning in Nessus, I described there in detail how Nessus scan profile looks like. And when I wrote about VM scanning in Qualys, I did not mentioned scan profiles at all. But it’s also an interesting topic. In Qualys scan profile you can’t specify which vulnerability check will run during the scan, as in Nessus (Upd. Actually yes you can, but in some different manner; I added how to do it in “Scan” section). However, you can also see some options that can affect the way you do the vulnerability scanning with Qualys.
The main option for me – the lists of scanning ports. By default Qualys does not check all the ports and that could negatively affect host detection during unauthenticated scanning.
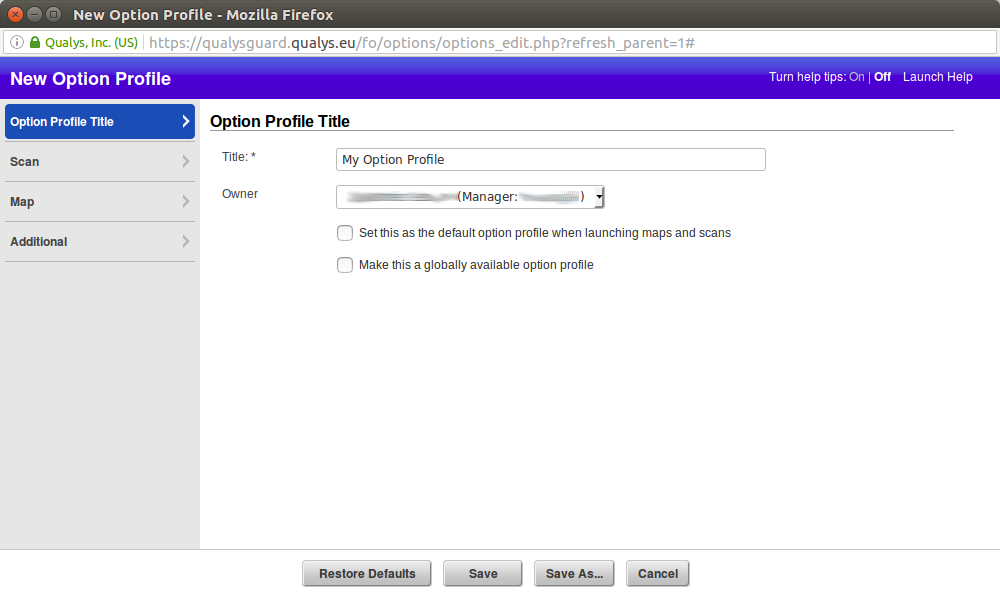
Creating new scan profile: Vulnerability Management -> Option Profiles -> New
Title
Setting title and owner of the profile. We can use this profile as a default for launching maps and scans or share it with other Qualys users in our organization ( “Make this a globally available option profile”).