Vulristics News: EPSS v3 Support, Integration into Cloud Advisor. Hello everyone! This episode will focus on the news from my open source Vulristics project for vulnerability analysis and prioritization.
Alternative video link (for Russia): https://vk.com/video-149273431_456239122
EPSS v3
The third iteration of the Exploit Prediction Scoring System (EPSS) was released in March. It is stated that EPSS has become 82% better. There is a pretty cool and detailed article about the changes. For example, EPSS Team began to analyze not 16 parameters of vulnerabilities, but 1164. I have a suspicion that most of these properties are vendor labels, as in the table.
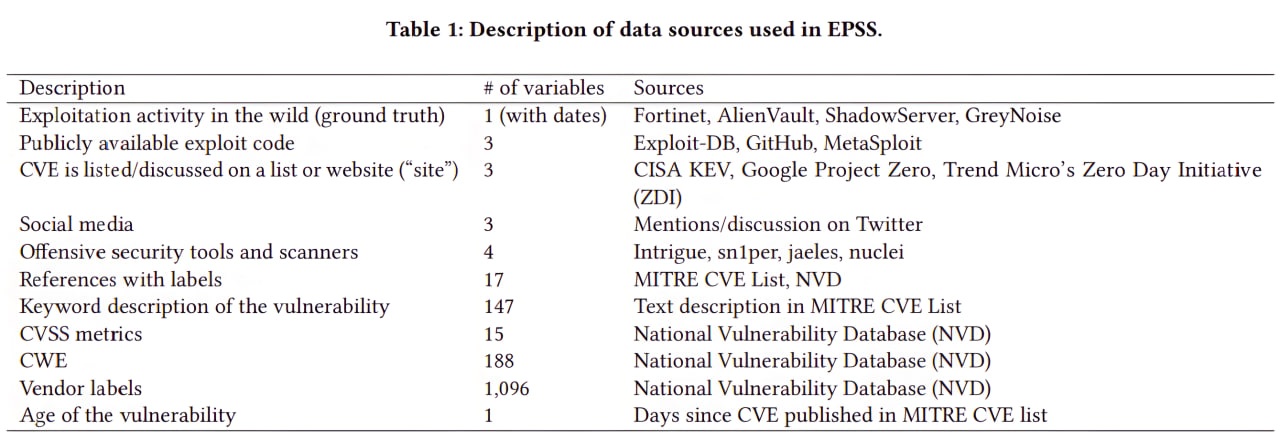
But trying to figure out how it actually works is not very promising. After all, this is the output of some neural network. So there is no algorithm there. In terms of complexity and incomprehensibility, this is already similar to Tenable VPR. But the fact that EPSS is available for free redeems everything. 😇 By the way, the article mentions Tenable VPR and other commercial scores and criticizes them for their proprietary nature, public inaccessibility, and the fact that these scores are partly based on expert opinion, and not just on data.
