New Vulners.com services for Linux Security Audit and Vulnerability Alerting. Upd. This post is out of date! Check out “Vulners Linux Audit API for Host Vulnerability Detection: Manual Auditing, Python Scripting and Licensing” from 2021.
A few weeks ago I was describing how to perform Linux Vulnerability Assessment without a Vulnerability Scanner. I also wrote in “Vulnerability scanners: a view from the vendor and end user side” that vulnerability scanning is not rocket science and it is easy to make your own scanner for vulnerabilities for a particular OS. Especially it is a popular Linux Distribution.
But. It’s one thing to write that you can do it, and another thing to develop a script for home use, and quite another thing to make a publicly available and efficient service…
Vulners Team guys have actually created such free Linux Vulnerability Audit service!
Linux Vulnerability Audit Service
First of all, they made a GUI where you can specify OS version (usually it is in the /etc/os-release file), list of packages installed on the host and get the list of vulnerabilities.
For example, here are the vulnerabilities for my Ubuntu Laptop, which I update frequently:
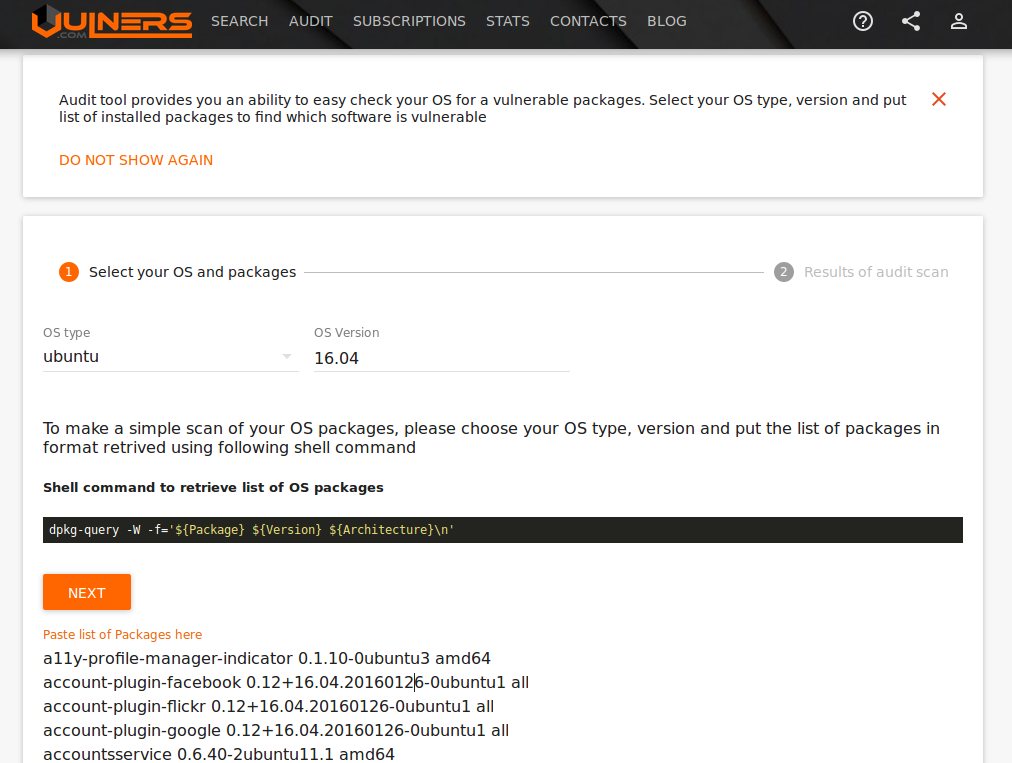
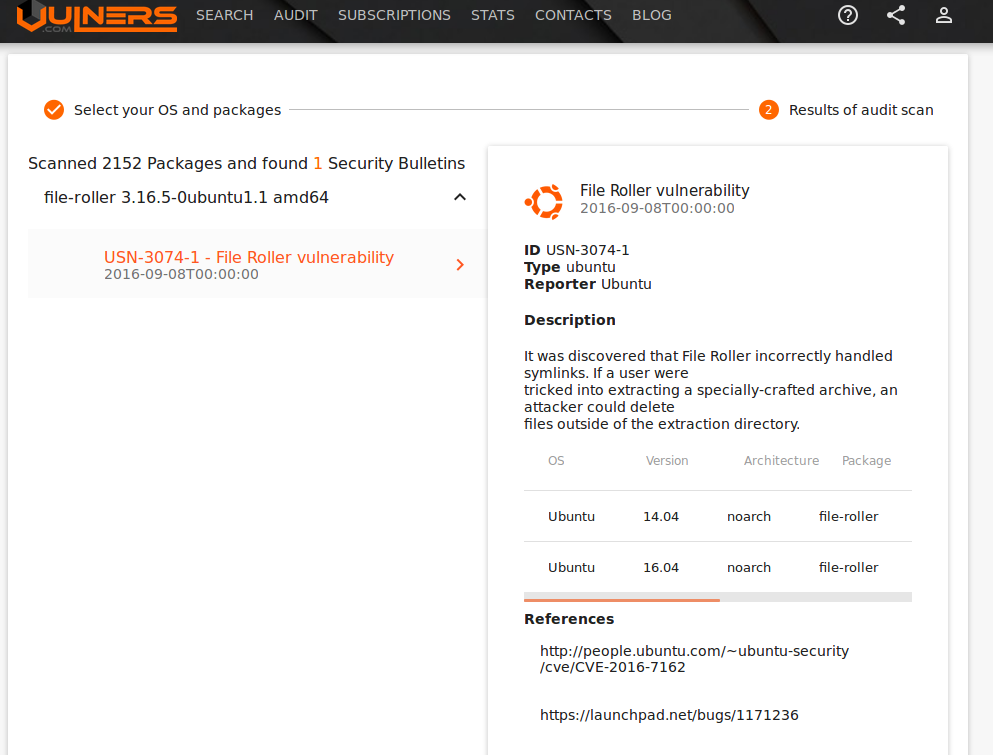
One vulnerability was found:
But GUI is good for demonstration. In real life, you can use Vulners Audit API. It will return list of vulnerabilities in JSON.
Example for CentOS:
curl -H "Accept: application/json" -H "Content-Type: application/json" -X POST -d '{"os":"centos","package":["pcre-8.32-15.el7.x86_64", "samba-common-4.2.3-11.el7_2.noarch", "gnu-free-fonts-common-20120503-8.el7.noarch", "libreport-centos-2.1.11-32.el7.centos.x86_64", "libacl-2.2.51-12.el7.x86_64", "sos-3.2-35.el7.centos.noarch" ],"version":"7"}' https://vulners.com/api/v3/audit/audit/
{
"result": "OK",
"data": {
"reasons": [
{
"providedPackage": "sos-3.2-35.el7.centos.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0188",
"providedVersion": "0:3.2-35.el7.centos",
"bulletinPackage": "sos-3.2-35.el7.centos.3.noarch.rpm",
"bulletinVersion": "3.2-35.el7.centos.3",
"package": "sos-3.2-35.el7.centos.noarch"
},
{
"providedPackage": "pcre-8.32-15.el7.x86_64",
"operator": "lt",
"bulletinID": "CESA-2016:1025",
"providedVersion": "0:8.32-15.el7",
"bulletinPackage": "pcre-8.32-15.el7_2.1.x86_64.rpm",
"bulletinVersion": "8.32-15.el7_2.1",
"package": "pcre-8.32-15.el7.x86_64"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:1486",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-7.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-7.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0612",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-6.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-6.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0448",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.3-12.el7_2.noarch.rpm",
"bulletinVersion": "4.2.3-12.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"vulnerabilities": [
"CESA-2016:1486",
"CESA-2016:1025",
"CESA-2016:0448",
"CESA-2016:0612",
"CESA-2016:0188"
],
"cvelist": [
"CVE-2015-5370",
"CVE-2015-7560",
"CVE-2016-2119",
"CVE-2016-2118",
"CVE-2015-7529",
"CVE-2016-2112",
"CVE-2016-2113",
"CVE-2016-3191",
"CVE-2015-8386",
"CVE-2015-8388",
"CVE-2015-8385",
"CVE-2016-2110",
"CVE-2015-5073",
"CVE-2015-8391",
"CVE-2015-2328",
"CVE-2016-2115",
"CVE-2015-3217",
"CVE-2016-2114",
"CVE-2016-2111"
],
"cvss": {
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:PARTIAL/A:COMPLETE/",
"score": 9.0
},
"packages": {
"pcre-8.32-15.el7.x86_64": {
"CESA-2016:1025": [
{
"providedPackage": "pcre-8.32-15.el7.x86_64",
"operator": "lt",
"bulletinID": "CESA-2016:1025",
"providedVersion": "0:8.32-15.el7",
"bulletinPackage": "pcre-8.32-15.el7_2.1.x86_64.rpm",
"bulletinVersion": "8.32-15.el7_2.1",
"package": "pcre-8.32-15.el7.x86_64"
}
]
},
"sos-3.2-35.el7.centos.noarch": {
"CESA-2016:0188": [
{
"providedPackage": "sos-3.2-35.el7.centos.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0188",
"providedVersion": "0:3.2-35.el7.centos",
"bulletinPackage": "sos-3.2-35.el7.centos.3.noarch.rpm",
"bulletinVersion": "3.2-35.el7.centos.3",
"package": "sos-3.2-35.el7.centos.noarch"
}
]
},
"samba-common-4.2.3-11.el7_2.noarch": {
"CESA-2016:1486": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:1486",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-7.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-7.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"CESA-2016:0448": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0448",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.3-12.el7_2.noarch.rpm",
"bulletinVersion": "4.2.3-12.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"CESA-2016:0612": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0612",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-6.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-6.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
]
}
}
}
They also presented a PoC of local agent for their further Vulnerability Management cloud solution. At the moment, it’s just a python-script, but in the future there would packages for different the operating systems. The agent is fully functional. It not only collects data from the system, and sends it to the Vulners server for analysis, but also receives vulnerability lists from the server and displays vulnerabilities in console.
$ git clone https://github.com/videns/vulners-scanner
$ cd vulners-scanner
$ ./linuxScanner.py
_
__ ___ _| |_ __ ___ _ __ ___
\ \ / / | | | | '_ \ / _ \ '__/ __|
\ V /| |_| | | | | | __/ | \__ \
\_/ \__,_|_|_| |_|\___|_| |___/
==========================================
Host info - Host machine
OS Name - centos, OS Version - 7
Total found packages: 1026
Vulnerable packages:
krb5-libs-1.13.2-10.el7.x86_64
CESA-2016:0532 - 'Moderate krb5 Security Update', cvss.score - 6.8
openssh-server-6.6.1p1-23.el7_2.x86_64
CESA-2016:0465 - 'Moderate openssh Security Update', cvss.score - 7.7
libtdb-1.3.6-2.el7.x86_64
CESA-2016:0612 - 'Critical ipa Security Update', cvss.score - 0.0
kernel-tools-3.10.0-327.4.5.el7.x86_64
CESA-2016:1033 - 'Important kernel Security Update', cvss.score - 0.0
CESA-2016:1633 - 'Important kernel Security Update', cvss.score - 4.3
CESA-2016:0185 - 'Important kernel Security Update', cvss.score - 7.2
CESA-2016:1539 - 'Important kernel Security Update', cvss.score - 7.2
CESA-2016:1277 - 'Important kernel Security Update', cvss.score - 7.2
openssl-libs-1.0.1e-51.el7_2.2.x86_64
CESA-2016:0301 - 'Important openssl Security Update', cvss.score - 0.0
CESA-2016:0722 - 'Important openssl Security Update', cvss.score - 10.0
nss-softokn-3.16.2.3-13.el7_1.x86_64
CESA-2016:0685 - 'Moderate nss-softokn Security Update', cvss.score - 6.8
...
As you can see, it really works.
However, there will always be some questions related to to cloud and agent based Vulnerability Management solutions. I would like to share my opinion on them.
1. Is it safe to send information about the hosts (and vulnerabilities) to a remote cloud service?
This is a worldwide practice. TOP3 Vulnerability Management vendors have their own cloud solutions (Qualys Cloud Platform, Nessus Cloud, Rapid7 Nexpose Now). For Qualys cloud-based solution is the main product, and this vendor has the biggest VM market share according to Gartner. Using of VM cloud solutions is a matter of trust to a particular vendor.
The same trio provide hosted solutions (Qualys private cloud appliance, Tenable Nessus and Security Center, Rapid7 Nexpose). If some companies will want to use local Vulners servers in their network, I think it’s quite possible that Vulners Team will release such solution.
Some ideas for the cautious Vulners Audit users. As Agent and API is open, you can easily modify the data you send to the Vulners server:
- Mix real and non-existent software packages in input, and exclude vulnerabilities of non-existent packages from the results.
- Use a “proxy server”, and make all requests to Vulners from this host only, hiding real ip-addresses and host names.
2. Is it safe to use local agents for vulnerability detection?
The use of agents for vulnerability detection is a recent global trend in VM. Agent-based solutions fast and reliable results. All you need is to install agents. You do not need to create scanning accounts, manage network access for the scanners and determine right time when the scan will not interfere with normal operations in the network and so on.
Tenable and Qualys presented their agent-based solutions not so long ago. They are very different. Tenable Agents are the Nessus installations without GUI and limited to scan only localhost. Nessus has been historically available for many platforms. Therefore, it was easier to do. Qualys created very minimalistic agents. They weigh just a few megabytes. It seems that Qualys Agents was written from scratch (Read more at “Dealing with Qualys Cloud Agents“).
In the case of Tenable Agents, vulnerability detections occurs on the host. Tenable Agent sends vulnerability data to the Nessus Cloud (Manager). In the case of Qualys, Agent collects a minimum set of data from the host and then sends it to Cloud Platform/Private Cloud Platform/Private Cloud Appliance for the further analysis.
Vulners Agents are similar to Qualys ones. And I think Vulners will evolve towards Qualys Asset View and Qualys ThreatPROTECT. Dashboards, vulnerability reporting, asset management will be in the cloud (private cloud), and Vulners agents will be only responsible for data collection.
The main advantage of Vulners is openness of the agent. Vulners Agents use the same open Vulners Audit API. This openness may provide greater flexibility of VM solutions: user will be able to restrict or modify the data, which Agent sends to the server, for example, to mask host names and IP addresses or even import data from other sources, like IT monitoring systems. It may be an advantage both in terms of functionality and in terms of privacy.
3. Do we really need third-party tools for vulnerability analysis, if there are utilities like debsecan for Debian or yum list-security for RHEL?
Indeed, there are a lot of vulnerability testing tools for different platforms. However, Vulnerability Management solution allow you to track of vulnerabilities for many platforms in a uniform manner and they don’t connect to the repository during the assessment. Solutions of this type provide detailed information about found vulnerabilities, how vulnerabilities may be exploited, patched etc. Working with separate linux utilities has its own quirks, e.g. ‘yum list-security’ works in RHEL, but does not work in CentOS. If small number of operating systems and devices are in use in organization, it is possible to live without Vulnerability Scanner/Management.
Limitations
Of course, Vulners Vulnerability Audit has some limitations:
- It’s all about Linux yet. And it will be difficult to add similar functionality for Windows and Mac. And for for network devices only agentless scanning is available.
- Web interface for working with scan results is still in developing and vulnerabilities can be viewed only in the agent’s console.
- There are some fundamental limitations of Vulnerability Assessment using package versions. Some of them I mentioned in “Vulnerability Assessment without Vulnerability Scanner“. What if the software was installed from self-made packages (with some non-standard name and version) or was installed from the sources? This issues are out of scope for most VM solutions.
Vulnerability Alerting
Another important free service, that was recently presented by Vulners Team, is email subscriptions. It makes possible to receive messages about new vulnerabilities as soon they appear in the Vulners database. To subscribe, just specify search query (see how to use queries in “Vulners – Google for hacker. How the best vulnerability search engine works and how to use it“) you are interested in, and your email.
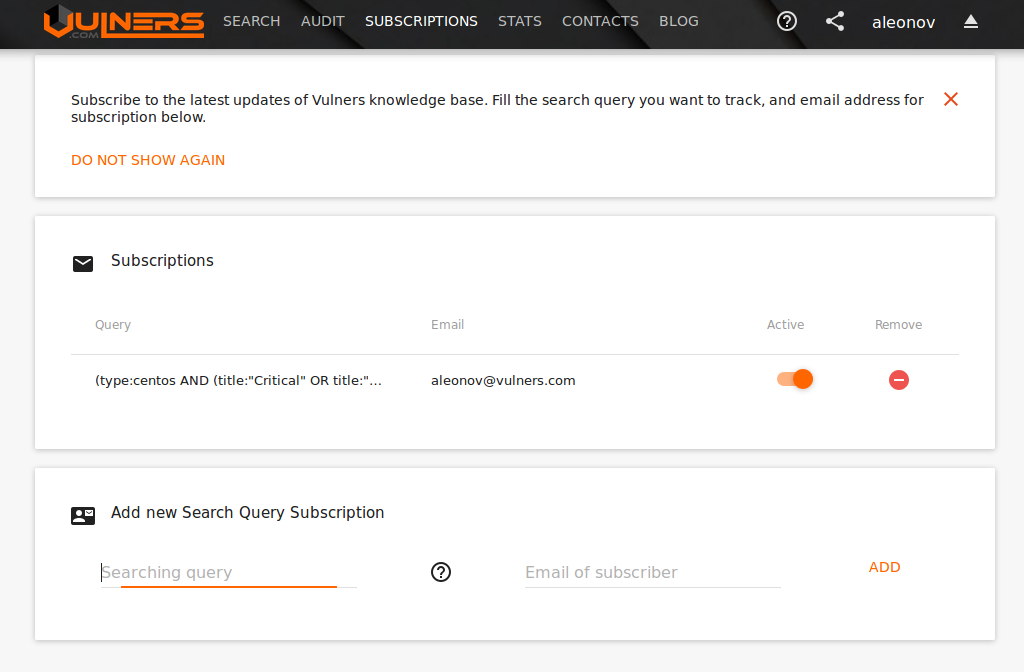
The database is updated every 4 hours. You will receive an email when there will be something new in results of your search query.
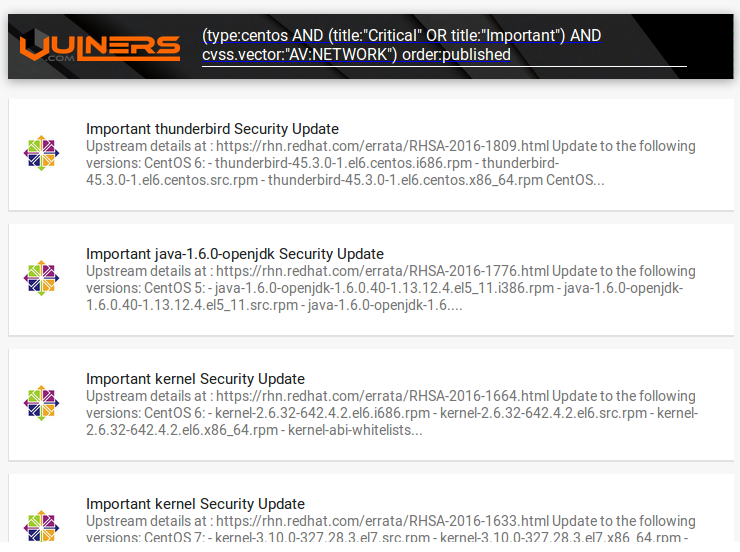
For example, CentOS bulletins with critical and important vulnerabilities, that can be exploited remotely:
In the Enterprise version you can subscribe other people and you can track more than 5 requests.
I use the following queries:
- CentOS bulletins with remotely exploited vulnerabilities:
(type:centos AND (title:”Critical” OR title:”Important”) AND cvss.vector:”AV:NETWORK”) order:published - Important CVE vulnerabilities in Microsoft software: (type:cve AND cvss.score:[6 TO 10] AND description:”Microsoft”) order:published
- Nessus plugins for remotely exploited vulnerabilities: (type:nessus AND cvss.score:[6 TO 10] AND cvss.vector:”AV:NETWORK” AND (NOT naslFamily:”Local” AND NOT naslFamily:”Windows : Microsoft Bulletins” AND NOT naslFamily:”Windows” )) order:published
- Exploits: (bulletinFamily:”exploit” AND (NOT type:nessus)) order:published
- OpenSSL and OpenSSH vulnerabilities: (type:openssl OR ( type:cve AND cpe:*openssh* ) ) order:published
It will be great if you share your queries in the comments to this post.
In conclusion
As you can see, Vulners is actively developing towards Vulnerability Management and Vulnerability Intelligence/Alerting. New functionality appears regularly. Almost all functionality is provided free of charge, even without advertising. And I hope that in the future this concept will stay the same: basic services will remain free for regular users and monetization will be made by adding new enterprise-level features.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Vulners Cloud Agents for Vulnerability Management | Alexander V. Leonov
Pingback: Problems of Vulnerability Prioritization and Detection | Alexander V. Leonov
Pingback: SSH, SFTP, public key authentication and python | Alexander V. Leonov
Pingback: Vulchain scan workflow and search queries | Alexander V. Leonov
Pingback: First steps with Docker: installation in CentOS 7, vulnerability assessment, interactive mode and saving changes | Alexander V. Leonov
Pingback: Can a Vulnerability Scan break servers and services? | Alexander V. Leonov
Pingback: Vulners Linux Audit API for Host Vulnerability Detection: Manual Auditing, Python Scripting and Licensing | Alexander V. Leonov
Pingback: Vulchain Scanner: 5 basic principles | Alexander V. Leonov