ZeroNights 2017: back to the cyber 80s. Last Friday, 17th of November, I attended the ZeroNights 2017 conference in Moscow. And it was pretty awesome. Thanks to the organizers! Here I would like to share some of my impressions.

First of all, I want to say that two main Moscow events for information security practitioners, PHDays and ZeroNights, provide an excellent opportunity to meet all of the colleagues at once and to synchronize current views on important information security issues, including, of course, Vulnerability Management, the most relevant for me. My opinion is that this year’s behind-the-scene conversations were especially good. And this is the most valuable characteristic for the event.
Every ZeroNights event has it’s own style. This time it was some geeky cyber retro from 1980s, like in popular cult movie Kung Fury. The place was also changed from familiar Cosmos Hotel to ZIL Culture Centre. It is the largest Palace of Culture from the Soviet Moscow times. The combination of US 80s cultural artifacts, RETROWAVE music with Soviet-style interiors (including, for example, statue of Lenin) made a pretty weird combination, but I liked it =)
I was unintentionally taking photos using some strange mode in camera and recorded a very short video fragment (3-5 seconds) for each photo. I decided to combine this fragments in a small video. This does not make much sense, but, perhaps, someone will find this “time-lapse” interesting 😉
Among the great presentations and workshops, there were also a small exhibition. This year there was two Vulnerability Management vendors: Beyond Security and Qualys.
Beyond Security, however, mainly promoted theirs SecuriTeam program at ZeroNights and not the AVDS VM solution.

The idea of SecuriTeam is that a security researcher can find a vulnerability in some software product and sell it to Beyond Security. Beyond Security is acting as middleman: collects the vulnerabilities and passes them to the software vendors.



As I understand this can be useful for the researches, who don’t want to contact with vendors directly. Because there is always a risk that a requests of bounty will be potentially perceived as kind of blackmailing.
I missed Qualys Security Conference this year. So, at ZeroNights I’ve heard news that FIM and IOC (I mentioned IOC data in “Vulnerability Management vendors and massive Malware attacks“) modes are not in beta any more and soon Qualys will have patching capabilities via Qualys Cloud Agents. Vulnerability Assessment and Patching in one solution, isn’t this great? =)

I spent only one day at ZeroNights and have seen only a part of Defensive Track. Here are TOP 3 reports, which I liked the most:
- Kheirkhabarov from Kaspersky Lab SOC “Hunting for Credentials Dumping in Windows Environment“. Very useful materials on retrieving passwords from memory (mimikatz and so on). It seems that Teymur really knows how to detect the usage of such utilities. I am really looking forward to study this slides carefully when they will be publicly available. Download slides here.

- Eldar Zaitov, Andrey Abakumov from Yandex “Automation of Web Application Scanning With Burp Suite“. Guys from Yandex finally abandoned w3af and now write plug-ins for Burp and commit them to opensource. The most interesting slide was about the limitations of Burp. Download slides here.
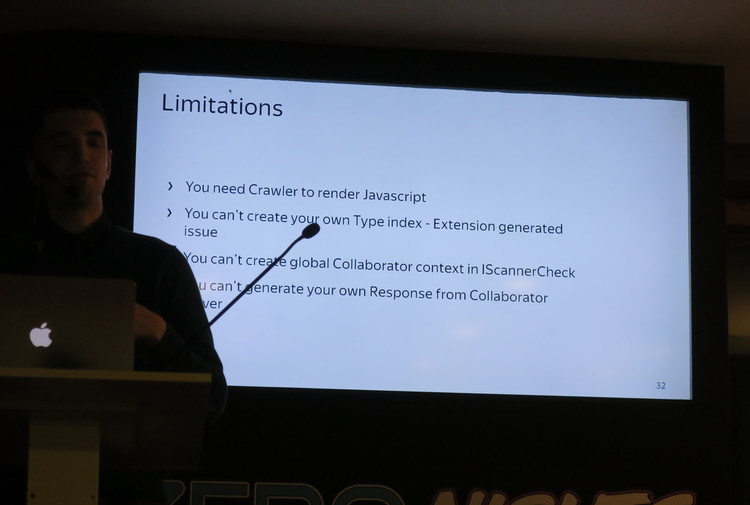
- Andrey Kovalev from Yandex Browser team “How to Implement SDL and Not Turn Grey“. I liked the criticism of SAST and the detailed description of the assessment stages. Download slides here.
Once again, a great conference. Thanks to the organizers! I hope to visit ZeroNights next year. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov
Pingback: U.S. sanctions against Russian cybersecurity companies | Alexander V. Leonov