October 2023: back to Positive Technologies, Vulristics updates, Linux Patch Wednesday, Microsoft Patch Tuesday, PhysTech VM lecture. Hello everyone! October was an interesting and busy month for me. I started a new job, worked on my open source Vulristics project, and analyzed vulnerabilities using it. Especially Linux vulnerabilities as part of my new Linux Patch Wednesday project. And, of course, analyzed Microsoft Patch Tuesday as well. In addition, at the end of October I was a guest lecturer at MIPT/PhysTech university. But first thing first.
Alternative video link (for Russia): https://vk.com/video-149273431_456239138
Back to Positive Technologies

On October 3, I joined the Positive Technologies team. There I will work on developing Vulnerability Management practices. I have already worked at PT for 6 years, from June 2009 to October 2015. And now, exactly 8 years later, I’m here again. I feel very pleasant emotions about this and have many plans. 🤩 I am sure that in the PT team I will be able to implement many cool things for the development of Vulnerability Management in Russia and abroad. 🙂
Vulristics
As for my open source Vulristics vulnerability prioritization project, I’ve made a few important updates.
NVD Data Source
I corrected the NVD data source, because NVD has become much less tolerant in the use of its API. After 5 consecutive requests, the API returns an error:
<html><body><h1>403 Forbidden</h1>
Request forbidden by administrative rules.
</body></html>Request forbidden by administrative rules.
According to the documentation:
“The public rate limit (without an API key) is 5 requests in a rolling 30 second window; the rate limit with an API key is 50 requests in a rolling 30 second window”.
For Vulristics, I made support for authentication using the NVD API key and sleeps of 0.6 seconds when using the key and 6 seconds without using the key.
To obtain an NVD API key, you need to specify your organization, organization type, and email in the form. After a few seconds, you will receive a one-time link via email, which will give you the key.
I also started using the NVD API v2.0 in Vulristics, which allowed me to get CISA KEV data on vulnerabilities being exploited in the wild. I also take links to exploits from NVD (however, be careful, these links are not always good enough).
Custom Data Source
I added a custom data source to Vulristics. This is a small but quite useful improvement. Sometimes you know for sure that there is an exploit for a vulnerability or a sign of exploitation in the wild. But the sources that Vulristics supports do not contain this data. 🤷♂️ How to take into account such facts in a Vulristics report?
Vulristics now has a custom data source. It does not make any requests to external sources. It simply reads JSON files from the data/custom_cve directory. You can add your JSON file for some CVE to this directory. And you can set the parameters in this file that you want to define for this CVE. You don’t have to set all the parameters. You can only set the ones you want. For example, only links to exploits.
Of course, you don’t have to do this manually. You can generate such files using a script based on the data you have. 😉
File example:
{
"description": "Remote Code Execution in Chromium",
"cvss_base_score": 9.2,
"wild_exploited": true,
"wild_exploited_sources": [
{"type": "ransomware_info_source", "text": "RansomwareINFO", "url": "https://www.some-site-about-ransomware-attacks.com/12345"}
],
"public_exploit": true,
"public_exploit_sources": [
{"type": "exploit_info_source", "text": "ExploitINFO", "url": "https://www.some-site-about-exploits.com/12345"}
],
"epss": 0.97434,
"epss_percentile": 0.99924
}Linux Patch Wednesday
I launched my new project – Linux Patch Wednesday! 🚀🥳 For Microsoft products we have a single day of increased attention – Microsoft Patch Tuesday, and for Linux there is no such day. Everything is too fragmented there and patches are released literally every day. But what’s stopping us from independently generating a list of CVEs fixed during the month and highlighting critical issues? Let’s try!
If Microsoft Patch Tuesday occurs every second Tuesday of the month, then Linux Patch Wednesday will occur every third Wednesday of the month!
I analyzed the public OVAL content of 5 Linux distribution vendors and uploaded the resulting monthly Linux Patch Wednesday bullruetins to Github. From March 2007 to November 2023. I invite you to check it out and, if you like it, give it a star. 🙂⭐️
I analyzed first October Linux Patch Wednesday bulletin using Vulristics! 🥳
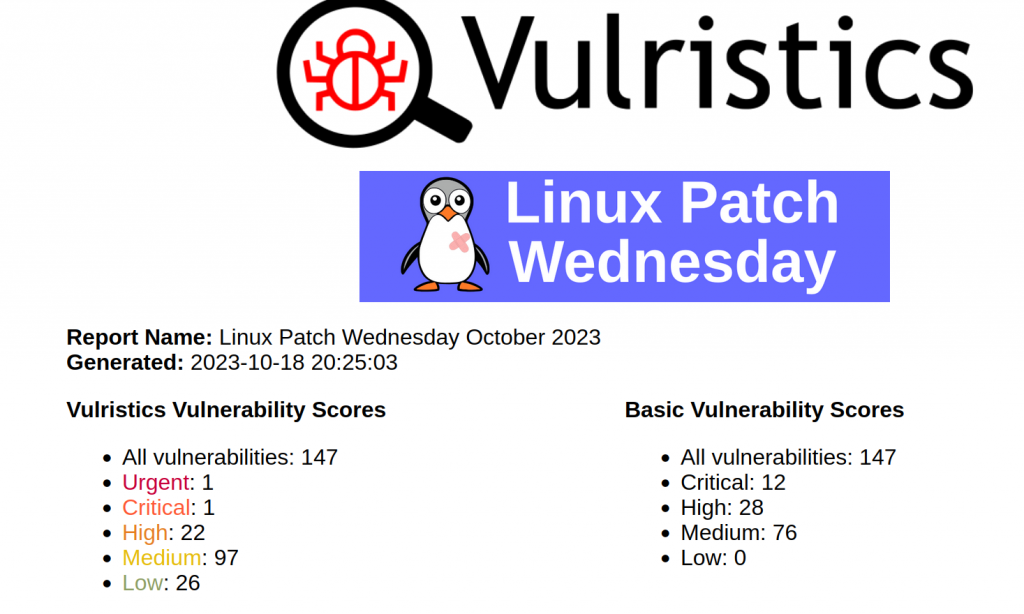
I’m pleased with the result. The top looks adequate and corresponds to what I highlighted in my Russian-language telegram channel avleonovrus and blog avleonov.ru.
- Memory Corruption – Chromium (CVE-2023-5217). This is a vulnerability in the libvpx library, which was the most critical in the October Microsoft Patch Tuesday. There is a PoC on Github and signs of exploitation in the wild.
- Elevation of Privilege / Remote Code Execution – GNU C Library (CVE-2023-4911). This is Qualys Looney Tunables. There has been a PoC for this vulnerability for a long time, but there are no signs of exploitation in the wild yet.
- Denial of Service – Golang Go (CVE-2023-29409). There is a PoC. Vulristics detected the software as TLS, since there is no hint of Go in the description of the CVE vulnerability. 🤷♂️
- Denial of Service – HTTP/2 protocol (CVE-2023-44487). Will also be in MSPT.
… - Memory Corruption – Curl (CVE-2023-38545). Not a very critical vulnerability, but PoCs have appeared for it on Github.
The rest of the vulnerabilities are without exploits or signs of exploitation in the wild.
Full Vulristics report: linux_patch_wednesday_october2023
Microsoft Patch Tuesday October 2023
I also released the Vulristics report on October’s Microsoft Patch Tuesday.
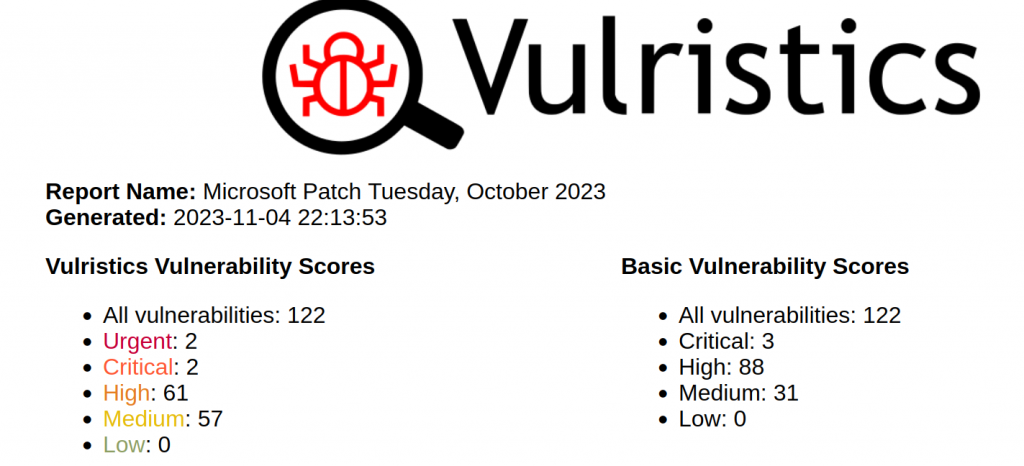
What is in the TOP:
- Memory Corruption – Microsoft Edge (CVE-2023-5217). This is a vulnerability in the libvpx library, which is used to play video in VP8 format. As in the recent libwebp case, this vulnerability affects many software products, but primarily web browsers. There is no public exploit yet, but there are signs of exploitation in the wild.
- Elevation of Privilege – Skype for Business (CVE-2023-41763). In fact, this is an information disclosure vulnerability. An unauthenticated attacker may send a special request to a vulnerable Skype for Business server and this will lead to the disclosure of confidential information. Such information may be used to gain access to internal networks. 🤷♂️ There are signs of exploitation in the wild and there are no public exploits yet. Several RCEs have also been released for Skype for Business.
- Information Disclosure – Microsoft WordPad (CVE-2023-36563). Exploiting this vulnerability could allow the disclosure of NTLM hashes. An attacker must send the user a malicious file and convince him to open it. Or, if an attacker has access to the host, he himself can run a special program on the host with the same result. This looks dangerous. There are signs of exploitation in the wild and there are no public exploits yet.
- Denial of Service – HTTP/2 protocol (CVE-2023-44487). Microsoft has released fixes for IIS (HTTP.sys), .NET (Kestrel) and Windows against the new effective DDoS attack “HTTP/2 Rapid Reset”. The problem is universal. Amazon, Cloudflare and Google recently reported that they were attacked via “HTTP/2 Rapid Reset”. So there are signs of exploitation in the wild.
There were no more vulnerabilities in Patch Tuesday that showed signs of exploitation in the wild or had a publicly exploit. You can also pay attention to:
🔻 20 Microsoft Message Queuing vulnerabilities, including some RCEs.
🔻 Remote Code Execution – Microsoft Exchange (CVE-2023-36778). “Successful exploitation requires that the attacker be on the same network as the Exchange Server host, and use valid credentials for an Exchange user in a PowerShell remoting session”. It doesn’t seem particularly critical, however “Exploitation More Likely.”
🔻 Elevation of Privilege – Windows IIS Server (CVE-2023-36434). This is achieved through simplified password brute-force attack. 🤷♂️
🔻 A pack of Elevation of Privilege vulnerabilities in Windows Win32k and Windows Graphics Component. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
Full Vulristics report: ms_patch_tuesday_october2023_report
Other Vulnerabilities
And finally, let’s note other important vulnerabilities, which I also wrote about in October in Russian
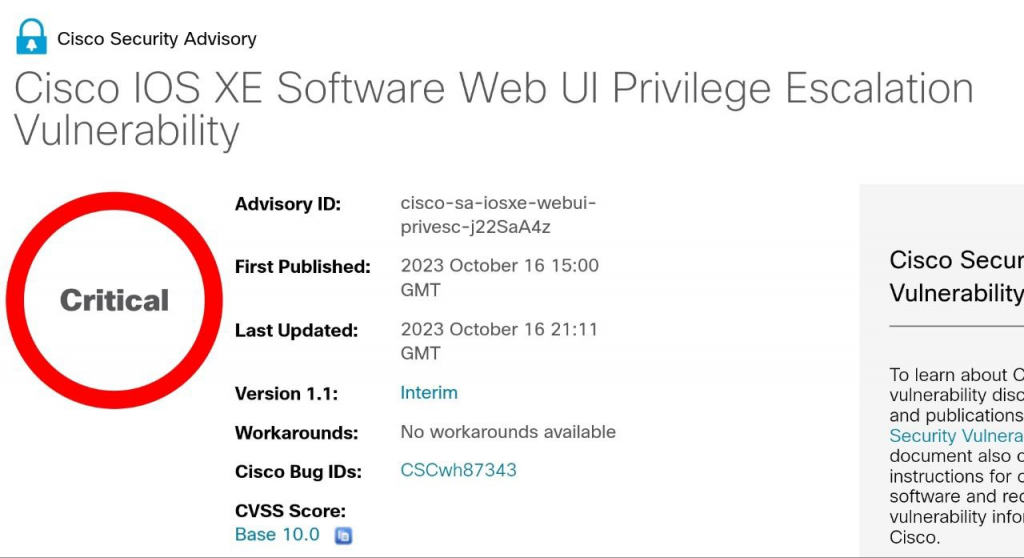
1. Authentication Bypass / Privilege Escalation – Cisco IOS XE (CVE-2023-20198)
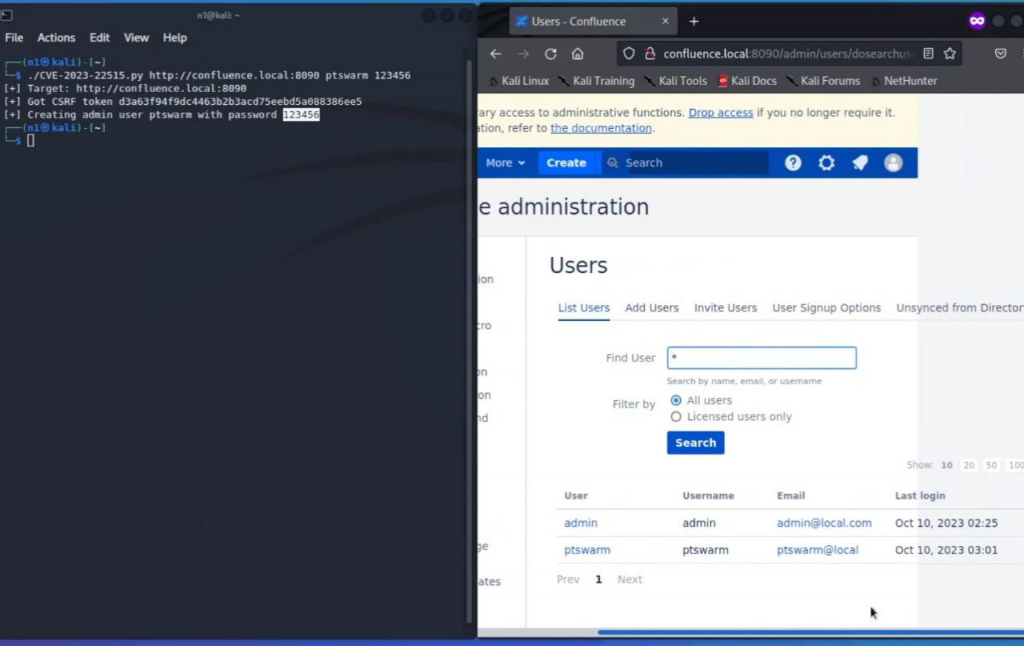
2. Authentication Bypass – Confluence (CVE-2023-22515)
3. VMware vulnerabilities: Remote code execution – vCenter Server (CVE-2023-34048) and Authentication Bypass – Aria Operations for Logs (CVE-2023-34051).

4. “Citrix Bleed“: Information Disclosure – NetScaler ADC/Citrix ADC and NetScaler Gateway (CVE-2023-4966)

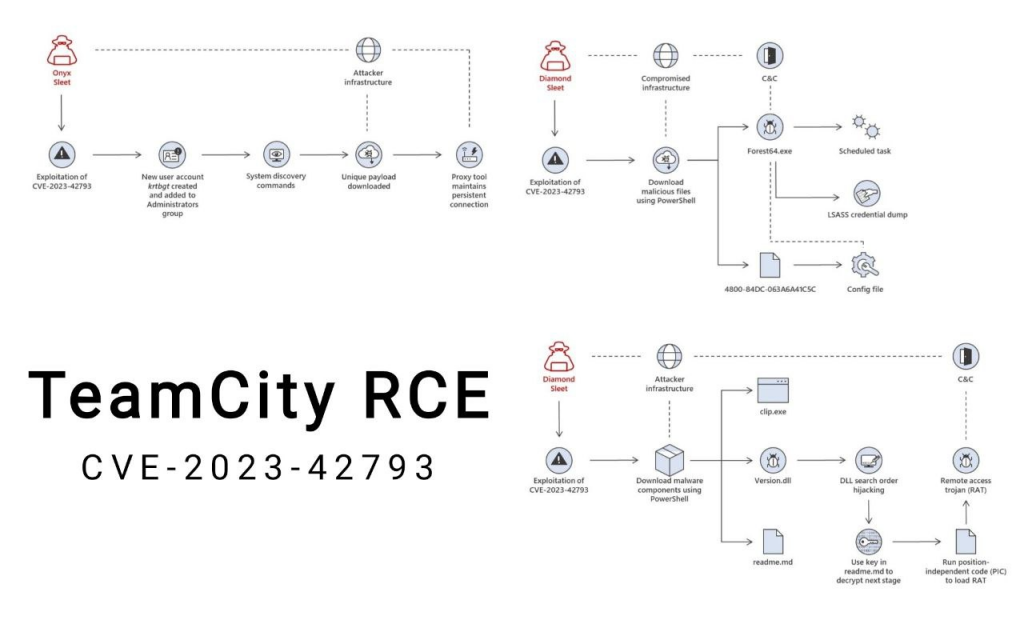
5. JetBrains: Remote code execution – TeamCity (CVE-2023-42793).
6. Full disclosure for unfixed Squid vulnerabilities.

VM Vendors news
From VM vendor news, I would like to highlight the following.

Miercom released a report “Vulnerability Management Competitive Assessment“. They did the research at the request of Tenable, so there couldn’t be much intrigue about who among Tenable, Qualys and Rapid7 would win. 😏 Unlike similar marketing comparisons, Miercom decided not to ask customers of the vendors or compare on high-level features. They compared based on basic functionality, namely the completeness of the detection databases. It’s nice to know that I myself was involved in comparing CVE knowledge bases and identifying blind spots before it became mainstream. 😅
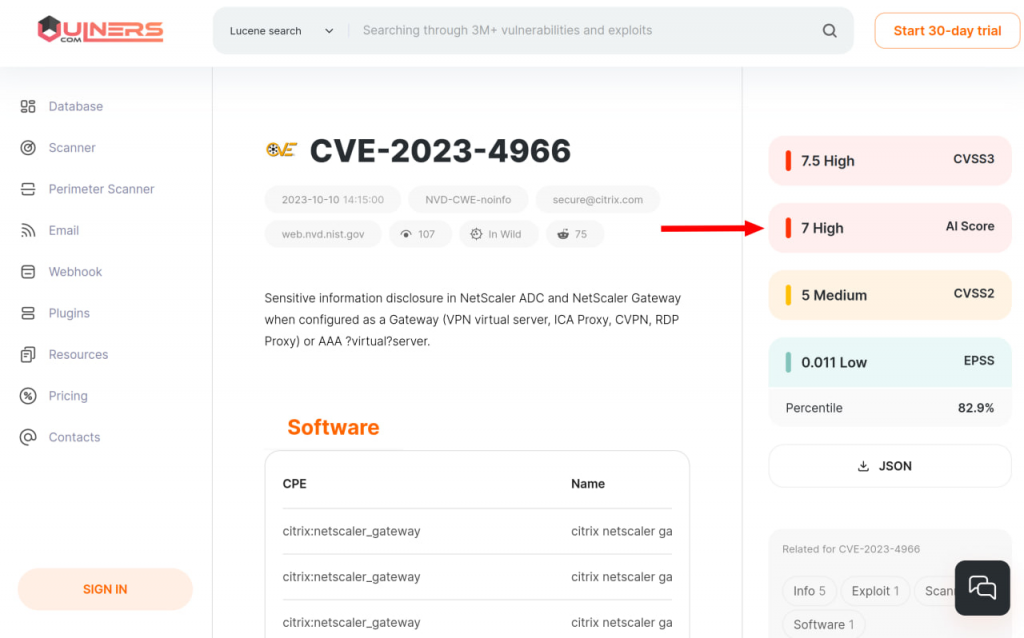
The guys from the Vulners team presented a new version of the automatic metric for assessing the criticality of vulnerabilities – AI Score v2. As the name implies, data processing there is carried out using machine learning, and specifically using the CatBoost library. Relationships between objects (there are more than 3 million objects in Vulners), CVSS Base Score values of ancestor objects, object type, text description of the object, etc. are analyzed. Give it a try, this feature is available for free to all Vulners users.
PhysTech Lecture
At the end of the month, I gave a lecture on Vulnerability Management at the Moscow PhysTech university. This is the second time, the first was 5 years ago. This time remotely.
On occasion, I updated my educational presentation. I separated 4 approximately equal parts:
🔹 Security Analysis – vulnerabilities and vulnerability detection
🔹 Asset Management – getting rid of chaos in infrastructure
🔹 Vulnerability Management – building a process with a focus on prioritizing vulnerabilities
🔹 Patch Management – everything related to patching vulnerabilities and relationships with IT
I primarily reworked the Asset Management and Vulnerability Management parts. It seems that I managed to combine the effective safety approach (by Positive Technologies), the guidelines of regulators and my own considerations quite well. This presentation would be good for guest lectures, and it is clear how it could usefully be expanded to 4 separate lectures (or even more). I’m satisfied. 🙂
By the way, PhysTech is under sanctions of the EU, USA, UK, Japan, Switzerland and New Zealand. A decent place. 🙂👍

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Выпустил ролик на 12 минут по итогам октября для своих англоязычных ресурсов | Александр В. Леонов
Pingback: November 2023 – January 2024: New Vulristics Features, 3 Months of Microsoft Patch Tuesdays and Linux Patch Wednesdays, Year 2023 in Review | Alexander V. Leonov