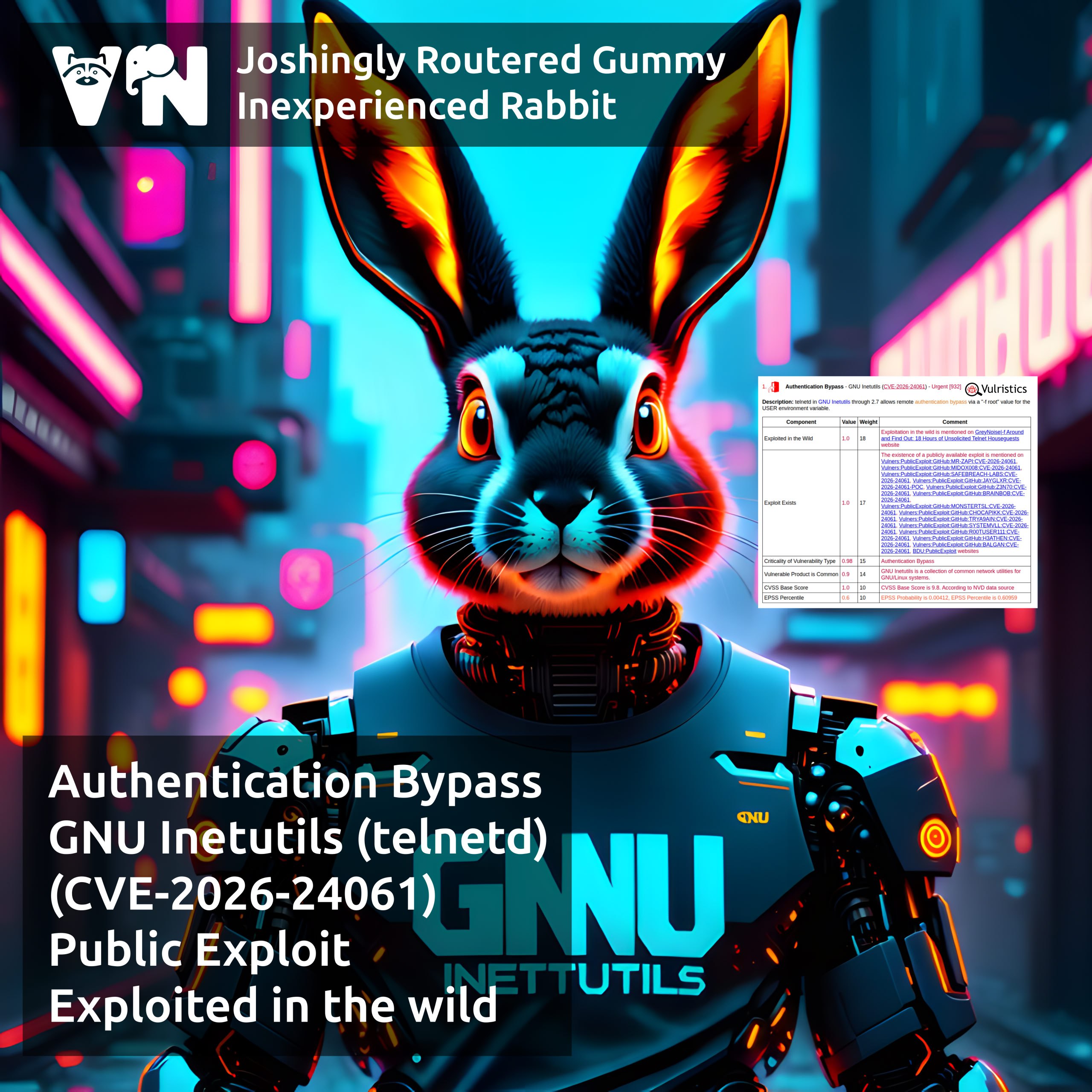
About Information Disclosure – Desktop Window Manager (CVE-2026-20805) vulnerability. Desktop Window Manager is a compositing window manager that has been part of Windows since Windows Vista. Exploitation of the vulnerability, which was addressed in the January Microsoft Patch Tuesday, allows a local attacker to disclose the “section address from a remote ALPC port which is user-mode memory”.
👾 Microsoft noted that this vulnerability is being exploited in attacks. The vulnerability was added to CISA’s KEV catalog on January 13. There are no public details about the attacks yet, but Rapid7 experts suggest that the disclosed memory address can be used to bypass ASLR, “increasing the chance of developing a stable elevation of privilege exploit for DWM”.
🛠 Public exploit PoCs have been available on GitHub since January 14.