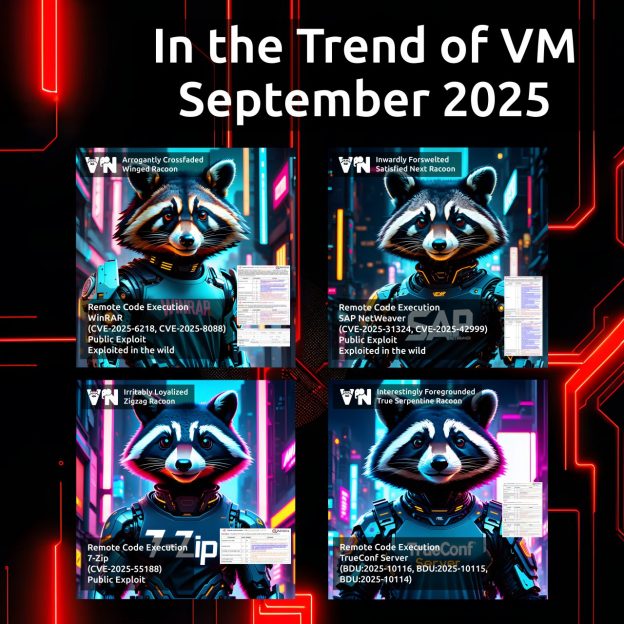
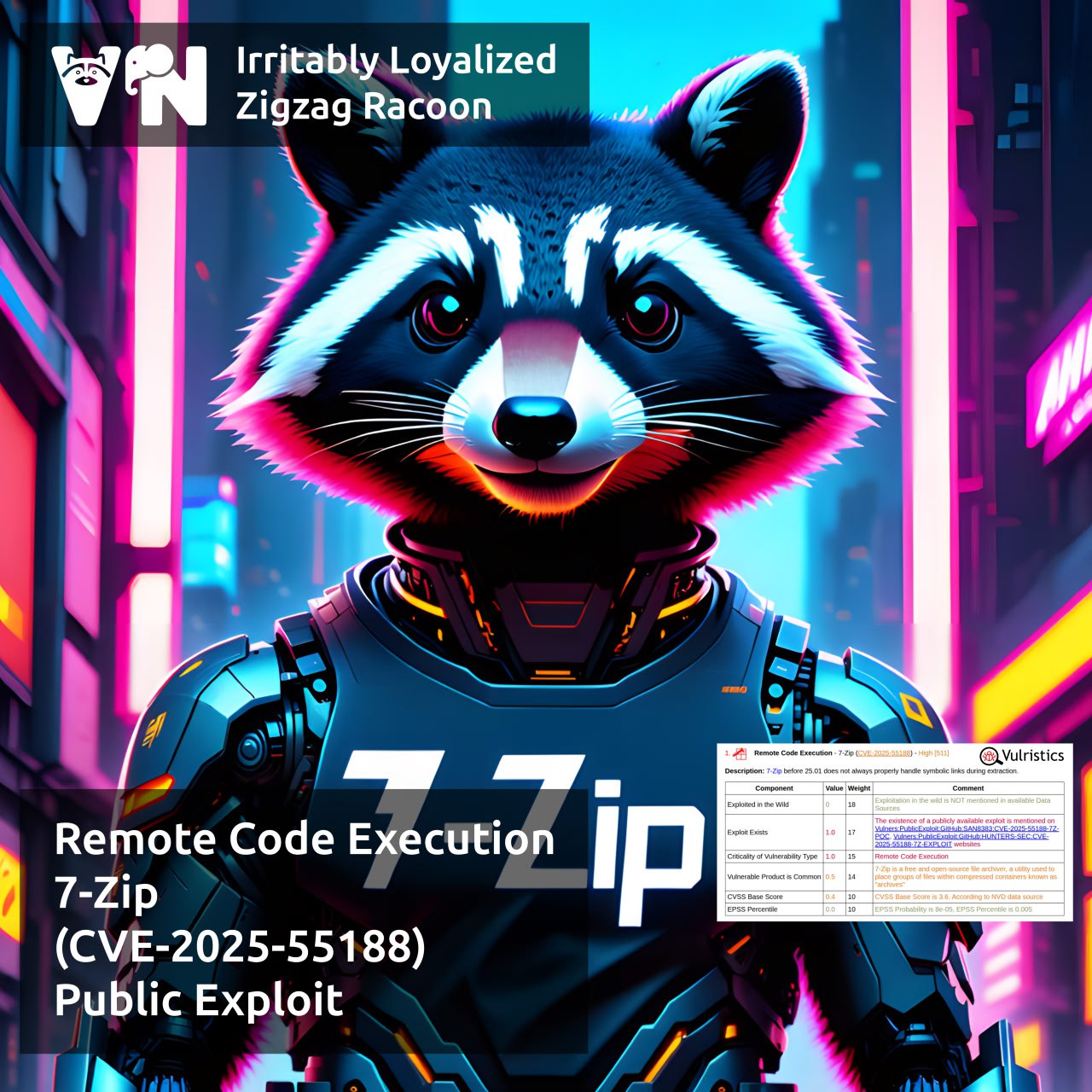
About Elevation of Privilege – Sudo (CVE-2025-32463) vulnerability. Sudo is a utility in Unix-like operating systems that allows a user to run a program with the privileges of another user, by default the superuser (root).
🔻 The vulnerability allows a local attacker to escalate privileges by forcing sudo to load an arbitrary dynamic library when using a root directory specified via the -R (–chroot) option. An attacker can execute arbitrary commands as root on systems that support (Name Service Switch configuration file).
⚙️ The vulnerability was fixed in sudo 1.9.17p1, released on June 30, 2025.
🛠 On the same day, a write-up by researcher Rich Mirch was published with a PoC exploit.
🐧 I noted Linux vendors’ remediation of this vulnerability in July Linux Patch Wednesday. Multiple public exploits for the vulnerability were available.
👾 On September 29, the vulnerability was added to CISA KEV.