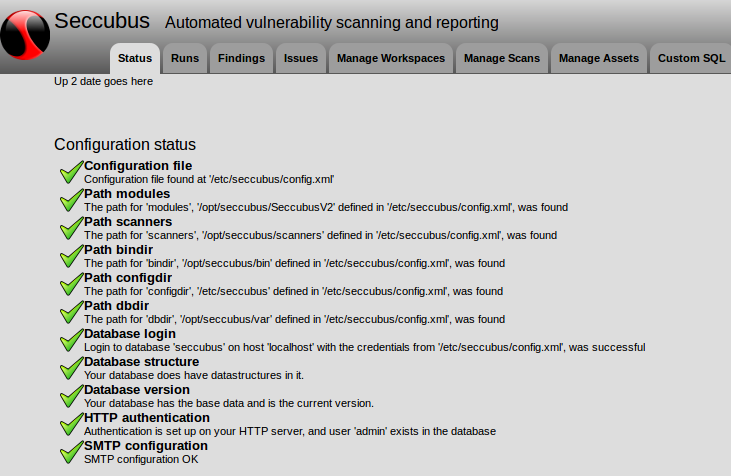
Retrieving Palo Alto NGFW security events via API. It may seem like NGFW topic is not really related to vulnerability assessment and vulnerability management. In fact, correlation of security events in traffic with vulnerability scan data sometimes may give very interesting results. For example, if we have a Windows desktop host with critical vulnerabilities, it won’t be a big surprise to detect some botnet activity related to this host. Fixing of this hosts should be a high priority task. Moreover, Palo Alto NGFW now supports signatures for vulnerability detection, like Tenable PVS. It’s pretty logical: if you are already searching something in the network traffic, why not to look also for vulnerable software versions in the packet headers?
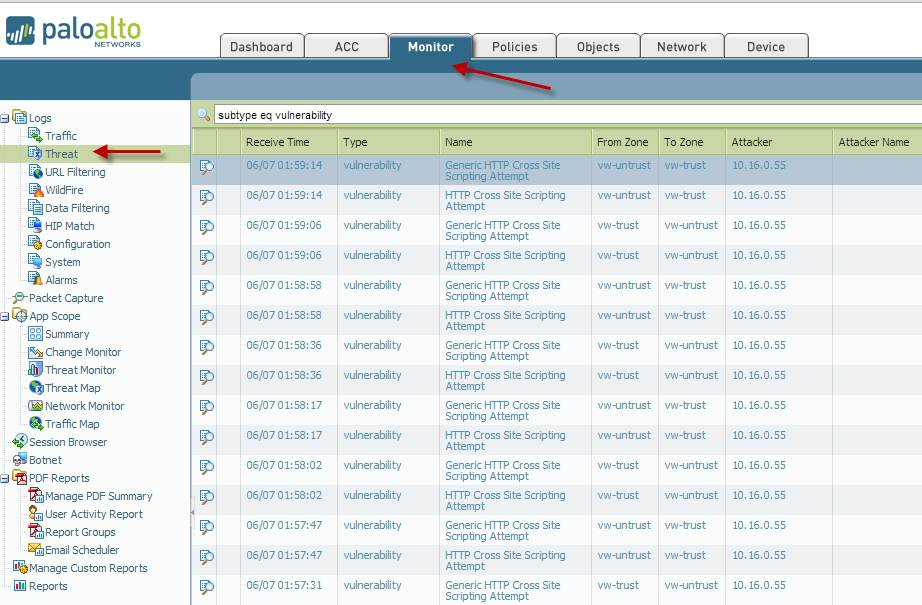
I took this image from the official manual
At the “Monitoring” tab of Palo Alto NGFW GUI web-interface you can see a flow of security events, produced by Palo Alto security rules, standard or custom. With PA query language you may easily filter this events. It is also possible to produce reports. However, the standard reports Palo Alto are not very informative and only represent some statistics of attacks without any additional information. Much more interesting reports you can make using Palo Alto API.