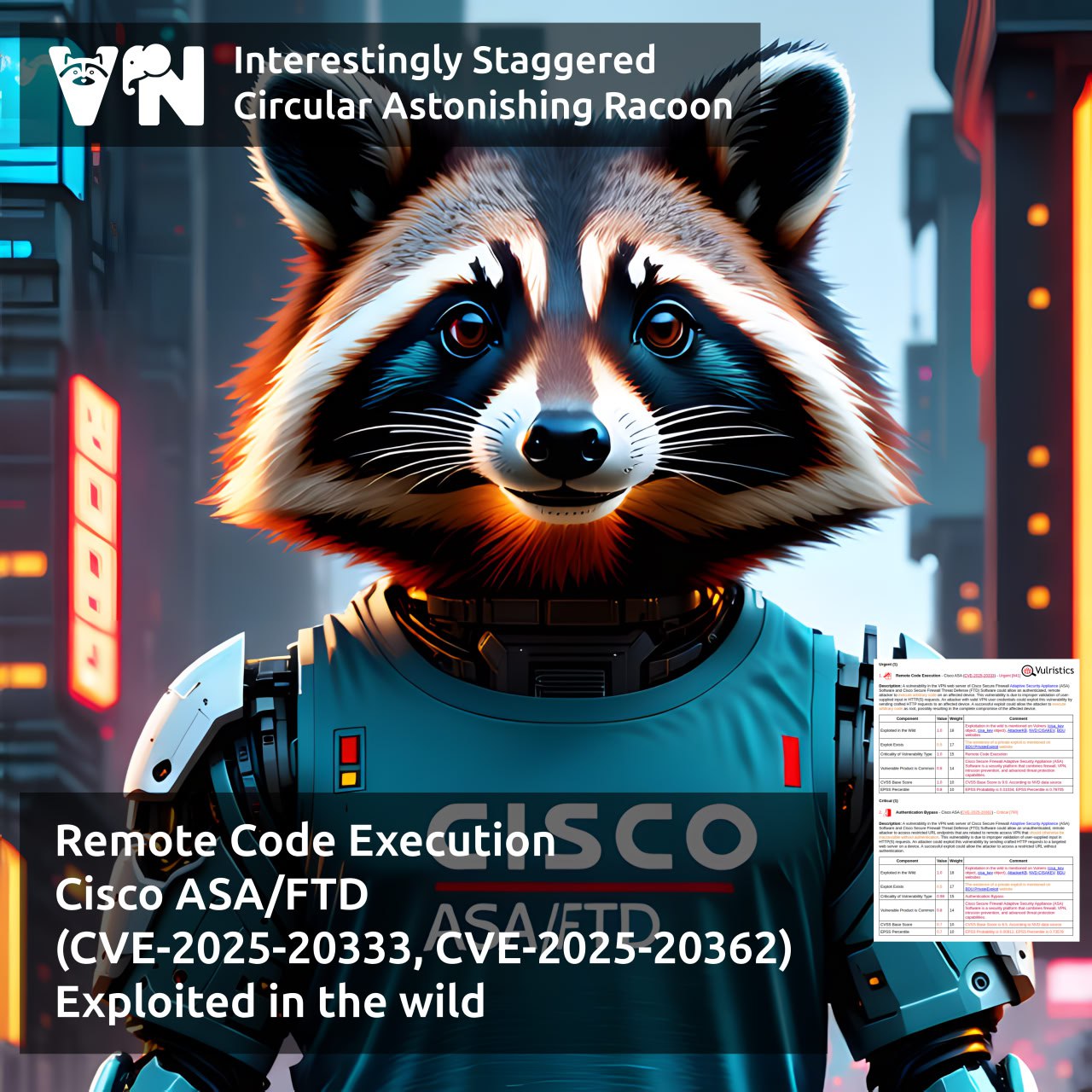
About Remote Code Execution – Cisco ASA/FTD (CVE-2025-20333, CVE-2025-20362) vulnerability. Cisco ASA and FTD are among the most widely used solutions for perimeter protection and for providing remote access to corporate infrastructure. 🔗 On September 25, Cisco released updates addressing a chain of vulnerabilities that could allow attackers take full control of affected devices:
🔻 Vulnerability CVE-2025-20362 allows an unauthenticated attacker to access a restricted URL.
🔻 Vulnerability CVE-2025-20333 allows an authenticated attacker to execute arbitrary code as root.
👾 Cisco reports that the vulnerability chain has been exploited in attacks since May 2025. The attacks are linked to the ArcaneDoor campaign and use the LINE VIPER and RayInitiator malware.
🛠 There are no public exploits yet.
🌐 Shadowserver shows over 45,000 vulnerable hosts, with more than 2,000 of them in Russia.