Seccubus installation and GUI overview. Seccubus can be roughly described as an open source analogue of Tenable SecurityCenter. Look, it can launch scans via APIs of Nessus, OpenVAS, and some other scanning tools, retrieve scan results, parse them and put in MySQL database. Then you can make SQL queries and work with scans in asset-based way (as you know, it is trending now).
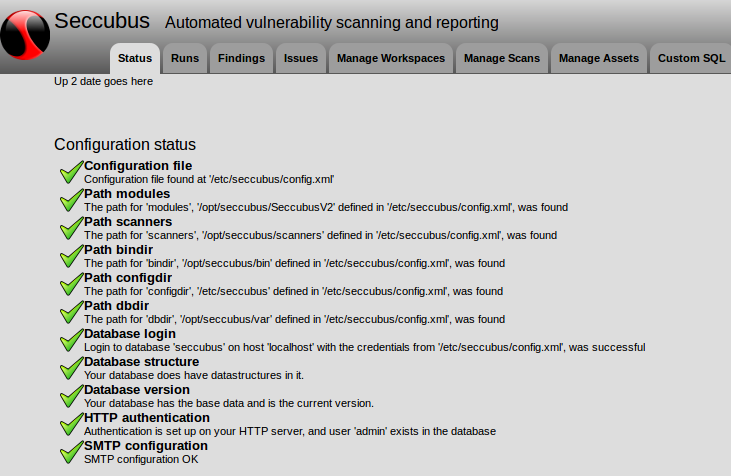
Well, Seccubus is not yet a fancy-looking security product. You will need to spend some time to install and configure it, but still it is a very interesting project with a great potential.
Seccubus also may serve as open project that will accumulate expertise in API usage for various Vulnerability Scanners. Another project of such kind is OpenVAS, it’s OSPd scripts and connectors.
In this post I will describe installation process an show elements of GUI web-interface.
I installed Seccubus in CentOS 6 x86_64. I also tried CentOS 6 i386 and it worked fine. However, I can’t recommend you to install official Seccubus packages in CentOS 7 and the latest Debian-based systems. I had some issues with dependencies and Apache configuration. It seems like these systems are not fully supported yet. Security patches for CentOS 6.8 will be available until 30 Nov 2020, so anyway we have time.