May Linux Patch Wednesday. Last month, we jointly decided that it was worth introducing a rule for Unknown dates starting from May 2024. Which, in fact, is what I implemented. Now, if I see an oval definition that does not have a publication date (date when patches for related vulnerabilities were available), then I nominally assign today’s date. Thus, 32406 oval definitions without a date received a nominal date of 2024-05-15. One would expect that we would get a huge peak for vulnerabilities that “started being patched in May” based on the nominal date. How did it really turn out?
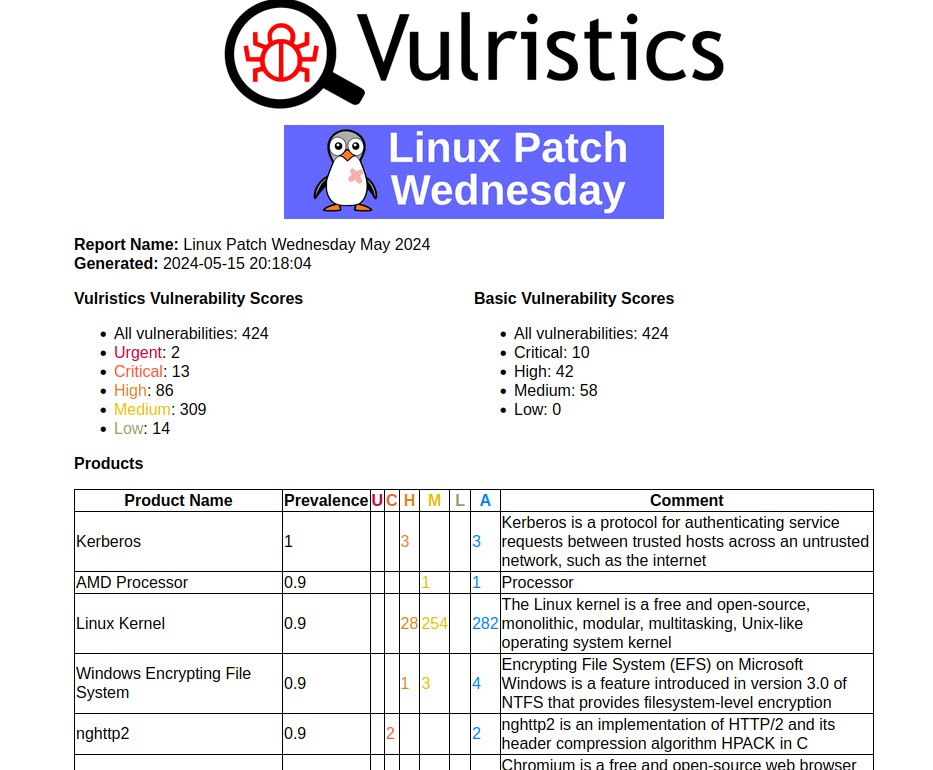
In fact, the peak was not very large. There are 424 CVEs in the May Linux Patch Wednesday. While in April there were 348. It’s comparable. Apparently the not very large peak is due to the fact that most of the vulnerabilities had patch dates older than the nominal one set (2024-05-15). And this is good. 🙂 It should get even better in June.
As usual, I generated a Vulristics report for the May vulnerabilities. Most of the vulnerabilities (282) relate to the Linux Kernel. This is due to the fact that Linux Kernel is now a CNA and they can issue CVEs for all sorts of things like bugs with huge traces right in the vulnerability descriptions.
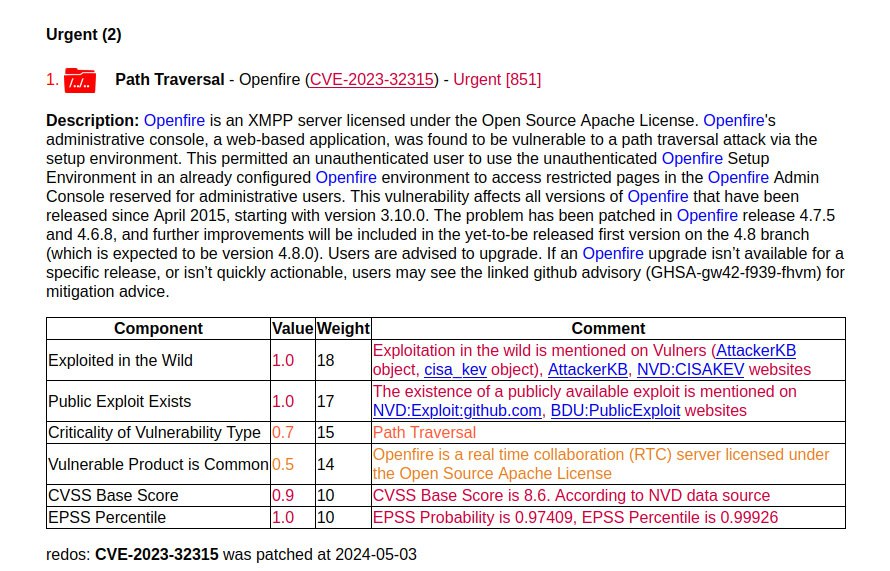
The vulnerability from CISA KEV comes first.
🔻Path Traversal – Openfire (CVE-2023-32315). This is the August 2023 trending vulnerability. It was included in the report due to a fix in RedOS 2024-05-03. Has it not been fixed in other Linux distributions? It looks like this. In Vulners, among the related security objects, we can only see the RedOS bulletin. Apparently there are no Openfire packages in the repositories of other Linux distributions.
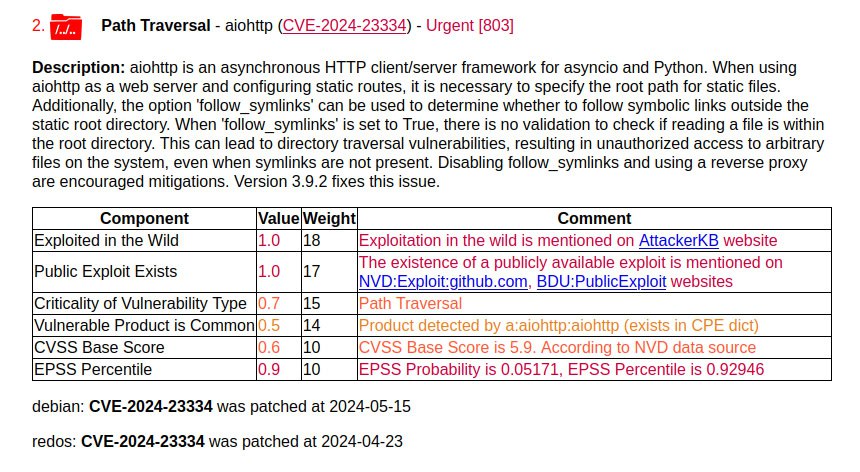
In second place is a vulnerability with a sign of active exploitation according to AttackerKB.
🔻 Path Traversal – aiohttp (CVE-2024-23334). The bug allows unauthenticated attackers to access files on vulnerable servers.
According to data from the FSTEC BDU, another 16 vulnerabilities have signs of active exploitation in the wild.
🔻 Memory Corruption – nghttp2 (CVE-2024-27983)
🔻 Memory Corruption – Chromium (CVE-2024-3832, CVE-2024-3833, CVE-2024-3834, CVE-2024-4671)
🔻 Memory Corruption – FreeRDP (CVE-2024-32041, CVE-2024-32458, CVE-2024-32459, CVE-2024-32460)
🔻 Memory Corruption – Mozilla Firefox (CVE-2024-3855, CVE-2024-3856)
🔻 Security Feature Bypass – bluetooth_core_specification (CVE-2023-24023)
🔻 Security Feature Bypass – Chromium (CVE-2024-3838)
🔻 Denial of Service – HTTP/2 (CVE-2023-45288)
🔻 Denial of Service – nghttp2 (CVE-2024-28182)
🔻 Incorrect Calculation – FreeRDP (CVE-2024-32040)
Another 22 vulnerabilities have an exploit (public or private), but so far there are no signs of active exploitation in the wild. I won’t list them all here, but you can pay attention to:
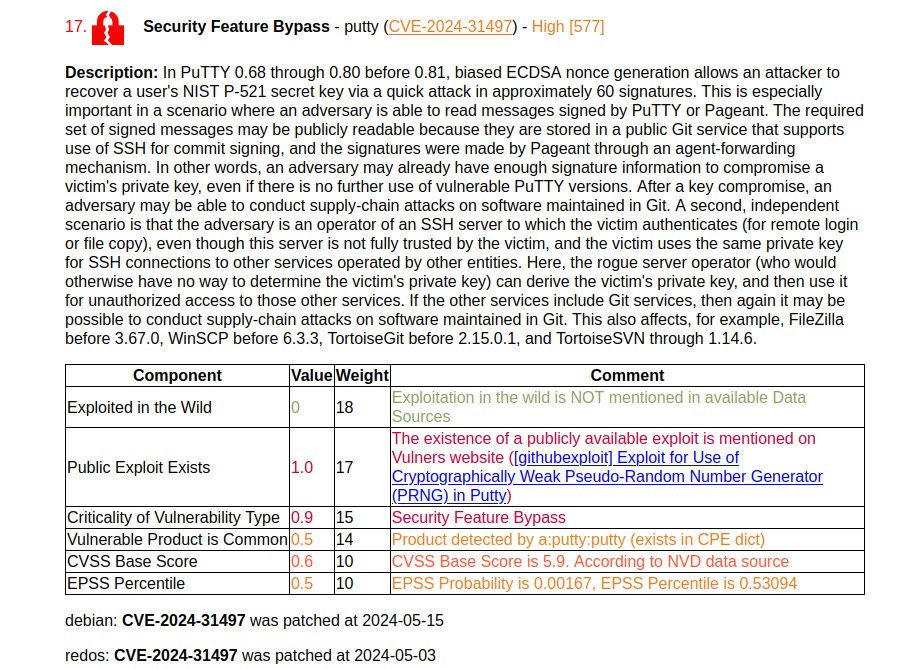
🔸 Security Feature Bypass – putty (CVE-2024-31497). A high-profile vulnerability that allows an attacker to recover a user’s private key.
🔸 Remote Code Execution – GNU C Library (CVE-2014-9984)
🔸 Remote Code Execution – Flatpak (CVE-2024-32462)
🔸 Command Injection – aiohttp (CVE-2024-23829)
🔸 Security Feature Bypass – FreeIPA (CVE-2024-1481)
I think that to improve the Vulristics report, it makes sense to separately group vulnerabilities with public exploits and private exploits, since this still greatly affects the criticality. Put 🐳 if you would like to see this feature.
🗒 Vulristics report on the May Linux Patch Wednesday
На русском