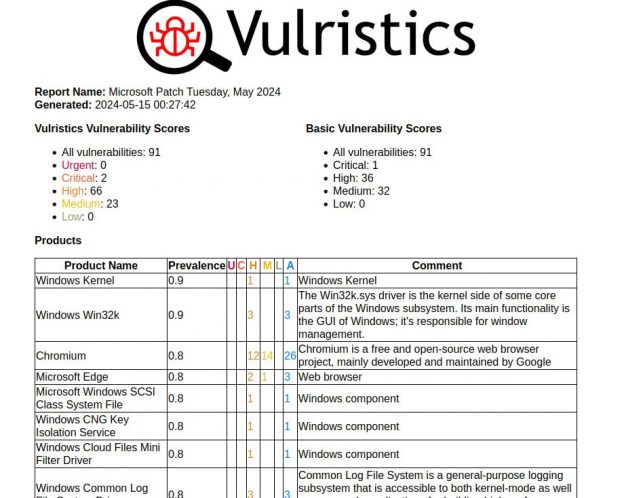
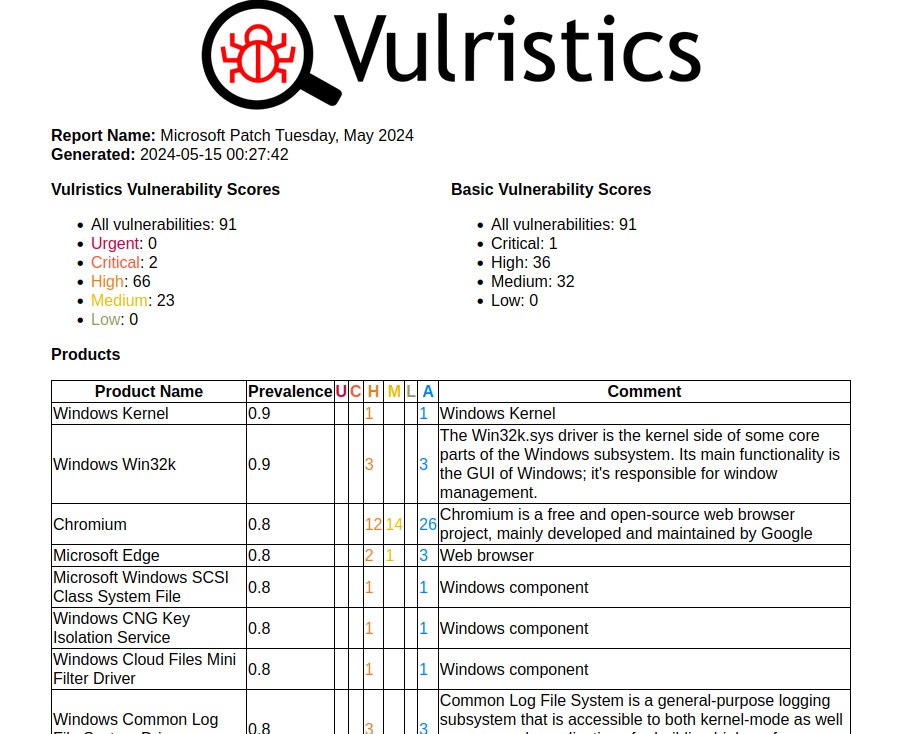
July Microsoft Patch Tuesday. There are 175 vulnerabilities in total, 33 of which appeared between June and July Patch Tuesday.
There are 2 vulnerabilities with the sign of exploitation in the wild:
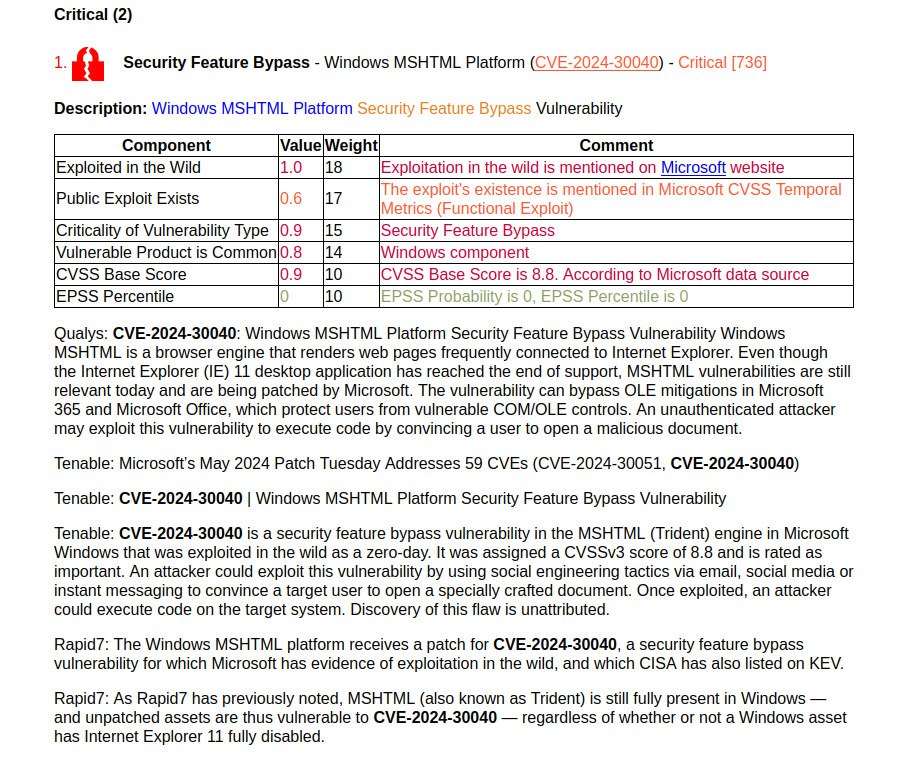
🔻 Spoofing – Windows MSHTML Platform (CVE-2024-38112). It’s not clear what exactly is being spoofed. Let’s wait for the details. It is currently known that to exploit the vulnerability, an attacker must send the victim a malicious (MSHTML?) file, which the victim must somehow run/open.
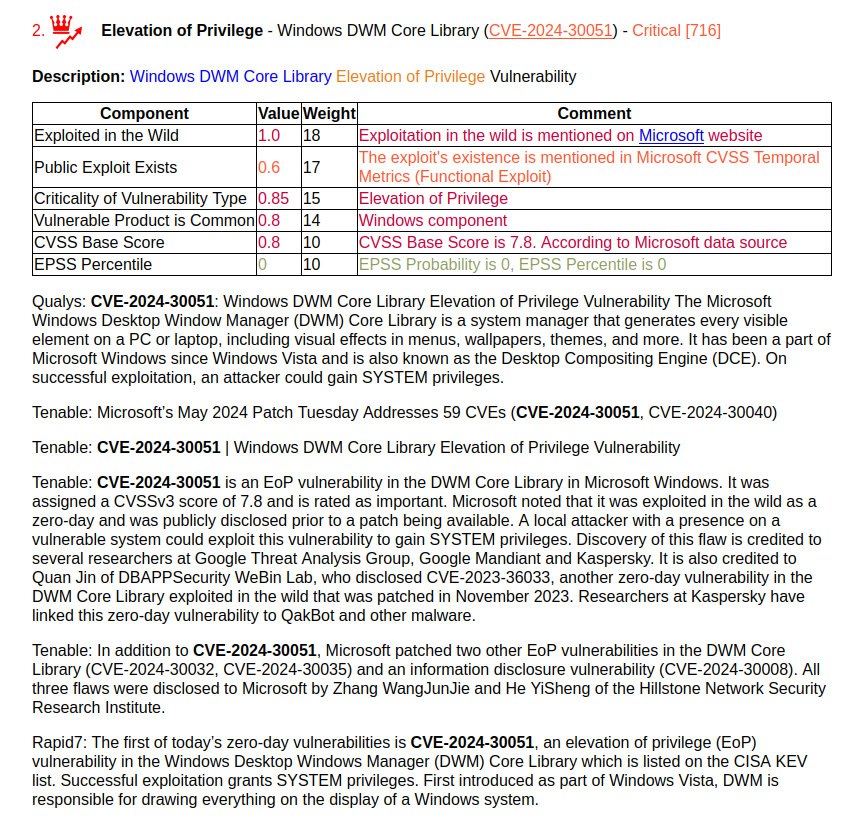
🔻 Elevation of Privilege – Windows Hyper-V (CVE-2024-38080). This vulnerability allows an authenticated attacker to execute code with SYSTEM privileges. Again, no details. This could be interpreted that the guest OS user can gain privileges in the host OS (I hope this is not the case).
From the rest we can highlight:
🔸 Elevation of Privilege – various Windows components (CVE-2024-38059, CVE-2024-38066, CVE-2024-38100, CVE-2024-38034, CVE-2024-38079, CVE-2024-38085, CVE-2024-38062, CVE-2024-30079, CVE-2024-38050). EoPs quite often become exploitable.
🔸 Remote Code Execution – Windows Remote Desktop Licensing Service (CVE-2024-38074, CVE-2024-38076, CVE-2024-38077)
🔸 Remote Code Execution – Microsoft Office (CVE-2024-38021)
🔸 Remote Code Execution – Windows Imaging Component (CVE-2024-38060). All you need to do is upload a malicious TIFF file to the server.
🔸 Remote Code Execution – Microsoft SharePoint Server (CVE-2024-38023, CVE-2024-38024). Authentication is required, but “Site Owner” permissions are sufficient.
🗒 Vulristics report on July Microsoft Patch Tuesday
Vulristics shows an exploit existence for Spoofing – RADIUS Protocol (CVE-2024-3596) on GitHub, but in reality it is just a detection utility.
На русском