OpenVAS plugins in Vulners.com. Great news! Vulners.com vulnerability search engine now supports OpenVAS detection plugins.
Why OpenVAS is important?
OpenVAS is the most advanced open source vulnerability scanner and is the base for many Vulnerability Management products.
Key vendors that produce OpenVAS-based products are Greenbone and Acunetix. There are some local vendors, such as Scaner VS by Russian company NPO Echelon.
“Vanilla” OpenVAS is also widely used when there is no budget for a commercial solution or it’s necessary to solve some specific problems, including developing own plugins for vulnerability detection. OpenVAS is integrated with wide range of information security systems, for example it is a default VM solution for AlienVault SIEM.
OpenVAS is well suited for education purposes as it is well documented and uses only open source code. For OpenVAS it’s always clear how the it works.
Critics
It is natural that commercial vendors criticize OpenVAS. Primarily, of course Tenable Network Security doing it. They need to justify why a proprietary and paid Nessus is better than the free and open source OpenVAS. Considering the fact that OpenVAS was created on the same Nessus code base, when it was an open project. It’s difficult to add more functionality to Nessus, because it can hurt the sales of Enterprise Tenable products then.
What remains?
- Ease of installation, configuration and updating
- Speed. “We rewrote the scanner and increased speed by several times.”
- Knowledge base. “We are able to identify larger number of vulnerabilities for larger number of platforms.”
OpenVAS is harder to install, configure and update then Nessus. Compare it yourself: Nessus installation and OpenVAS installation.
It’s hard to measure scanner’s speed. Do fewer checks, and the scan will end faster. You also can’t use comparisons of Nessus 2 and Nessus 3 engines made by Tenable. OpenVAS scanning engine has been heavily reworked and improved since the time it was forked.
The knowledge base is a more concrete thing. You can compare KBs of two competitive VM products if they use common vulnerability IDs. But we need a tool for this.
Here comes Vulners.com
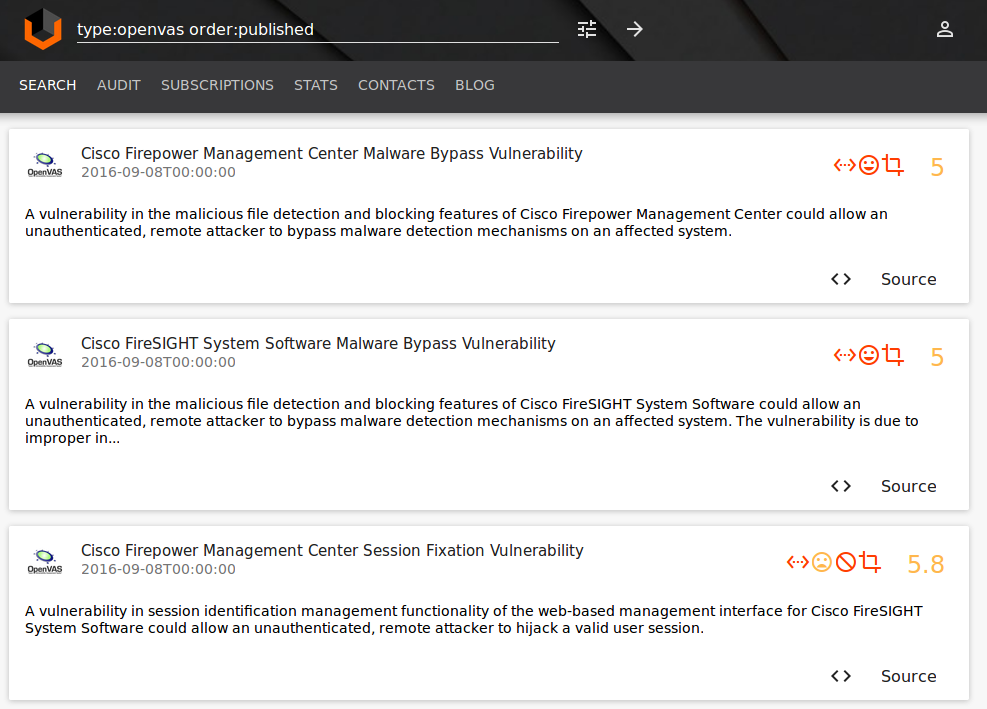
With Vulners.com you can search plugins for Nessus and OpenVAS.
As Nessus is a commercial scanner, you can only see the general description of Nessus plugins, and for OpenVAS description and complete code of plugins are available:
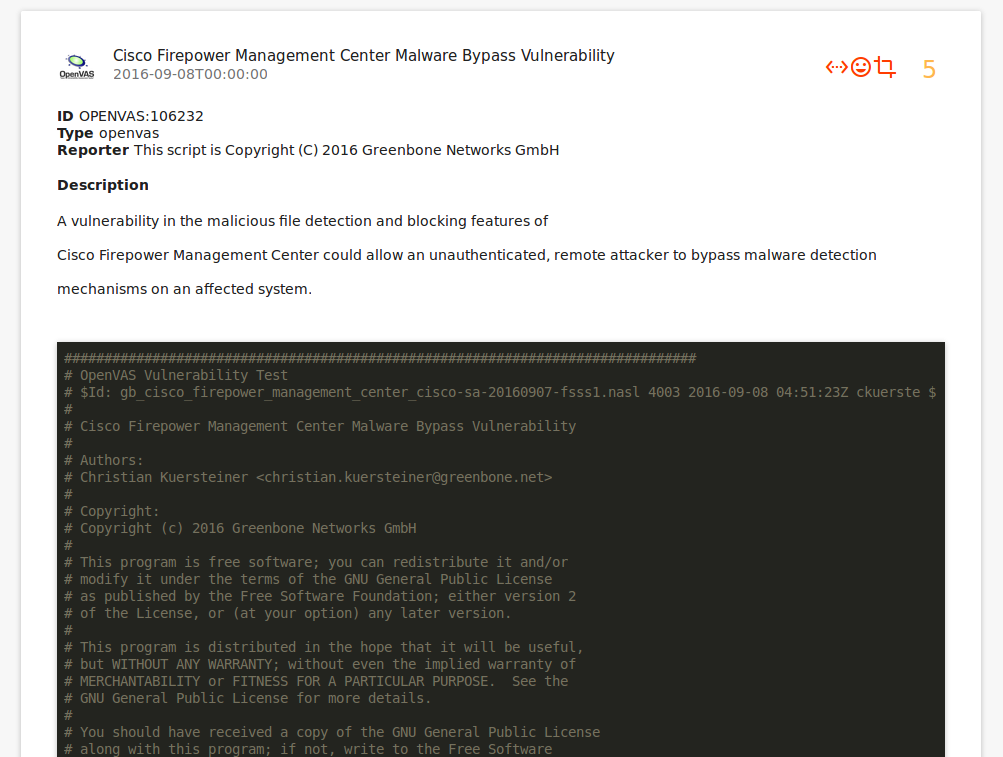
All linked objects:
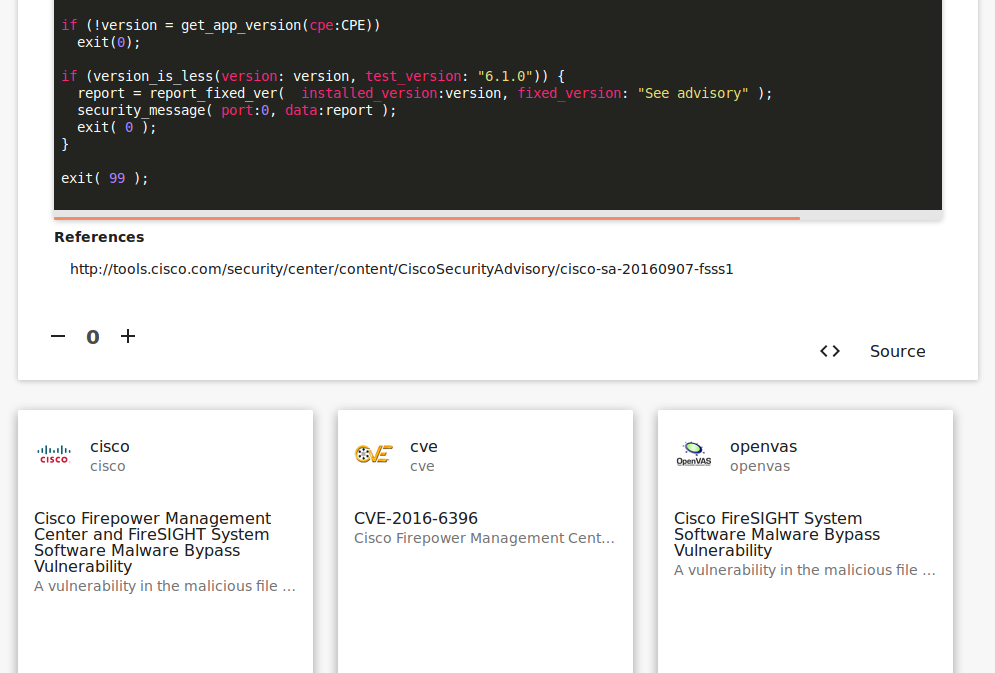
Only OpenVAS can detect this CVE-2016-6396 vulnerability.
This CVE-2016-4270 Adobe Reader vulnerability, can be detected by Nessus, and OpenVAS:
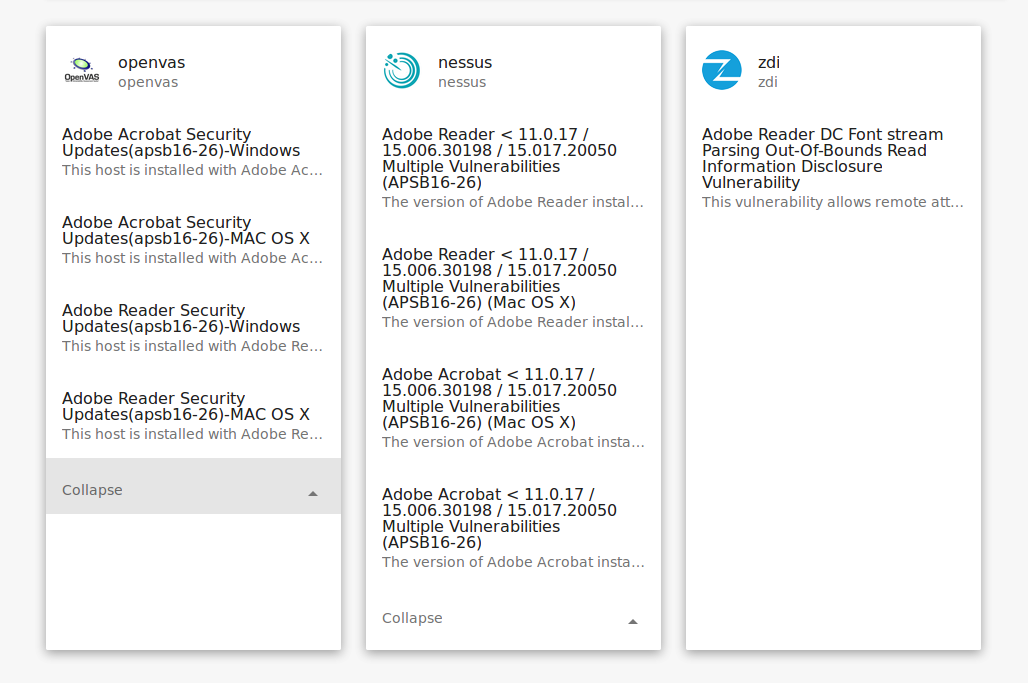
Now you can analyze knowledge bases easier and ask uncomfortable questions to your VM vendors.
Another usage scenario – the enrichment of OpenVAS scan results with Vulners data. If you have a list of vulnerabilities (OpenVAS plugin IDs), you can search for related exploits.
For example, exploitdb reference for the plugin OPENVAS:807869:

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Tenable doesn’t want to be Tenable anymore | Alexander V. Leonov
Pingback: Fast comparison of Nessus and OpenVAS knowledge bases | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov