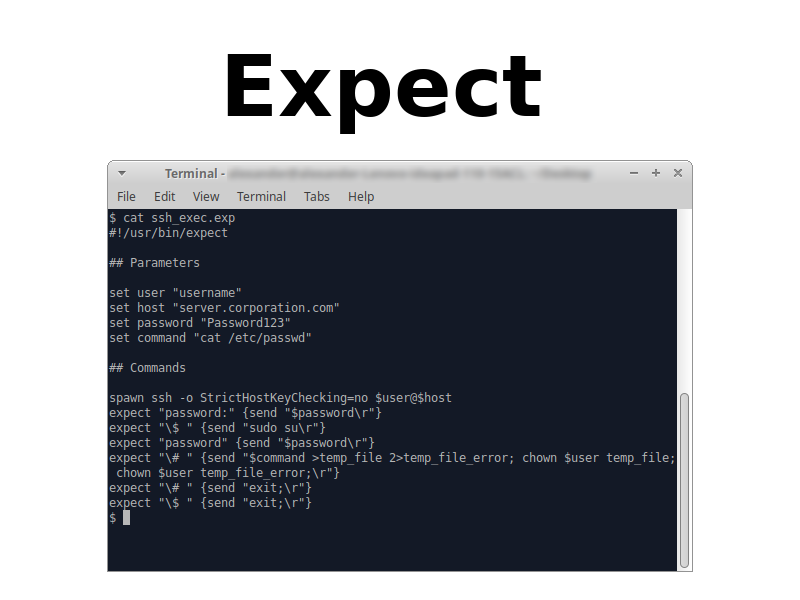
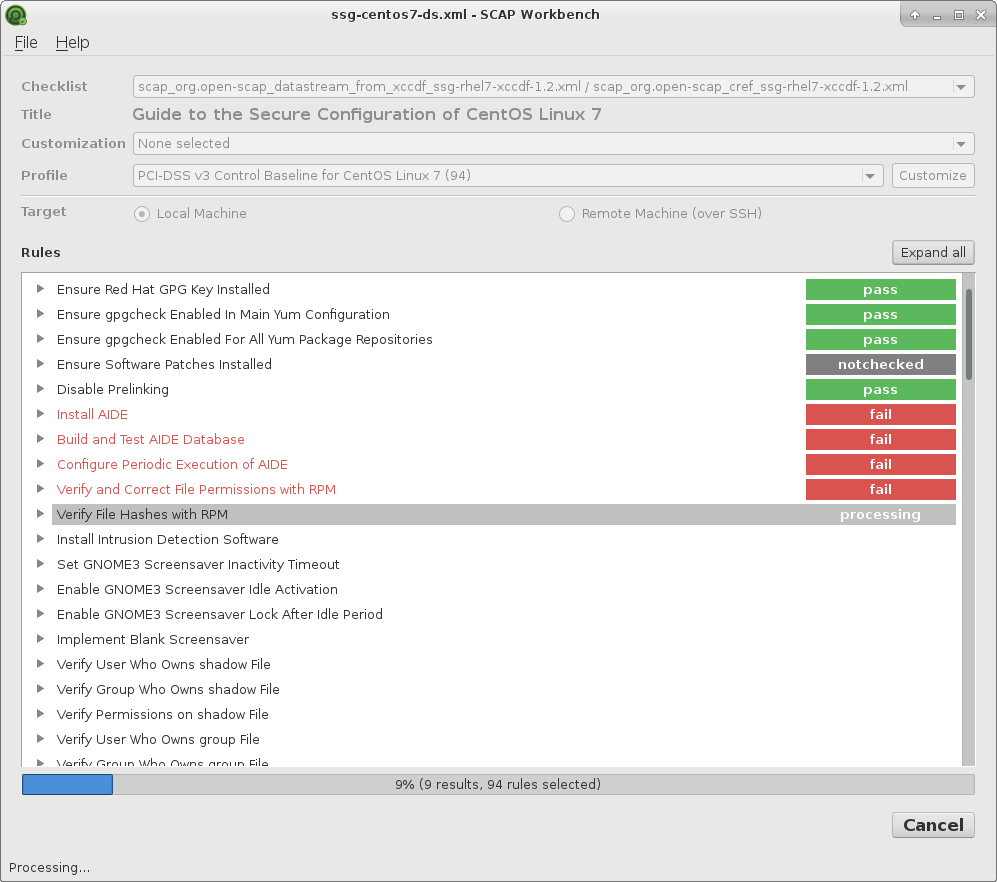
Publicly available Tenable .audit scripts. This is most likely a slowpoke news, but I just found out that Tenable .audit files with formalized Compliance Management checks are publicly available and can be downloaded without any registration. ?? However, you must accept the looooong license agreement.
So, I have two (completely theoretical!) questions ?:
- What if someone supports the .audit format in some compliance tool and gives the end user an ability to use this content by Tenable to asses their systems? Will it be fair and legal?
- What if someone uses this content as a source of inspiration for his own content, for example, in a form of OVAL/SCAP or some scripts? Will it be fair and legal?