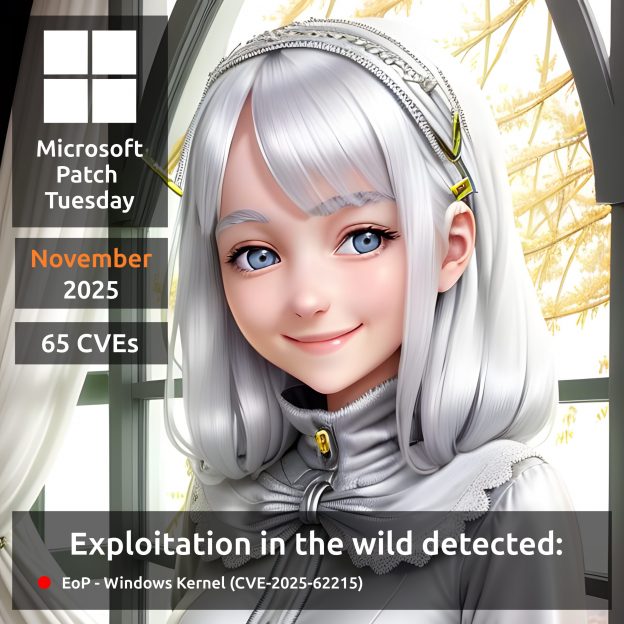
November Microsoft Patch Tuesday. A total of 65 vulnerabilities. I’m not comparing this with the October report because I’ve decided to cover only MSPT-day vulnerabilities. The thing is, Microsoft has started massively adding Linux-product vulnerabilities to their official website, and these clutter the “extended” MSPT reports. 🤷♂️
There is one vulnerability with evidence of in-the-wild exploitation:
🔻 EoP – Windows Kernel (CVE-2025-62215)
No vulnerabilities have publicly available exploits yet. Notable ones include:
🔹 RCE – GDI+ (CVE-2025-60724), Microsoft Office (CVE-2025-62199), Microsoft Office (CVE-2025-62205, CVE-2025-62216), Agentic AI and Visual Studio Code (CVE-2025-62222), Visual Studio (CVE-2025-62214)
🔹 EoP – Windows Client-Side Caching (CVE-2025-60705), Windows Ancillary Function Driver for WinSock (CVE-2025-60719, CVE-2025-62213, CVE-2025-62217), Microsoft SQL Server (CVE-2025-59499)