Vulnerability Management for Network Perimeter. Network Perimeter is like a door to your organization. It is accessible to everyone and vulnerability exploitation does not require any human interactions, unlike, for example, phishing attacks. Potential attacker can automate most of his actions searching for an easy target. It’s important not to be such of target. 😉
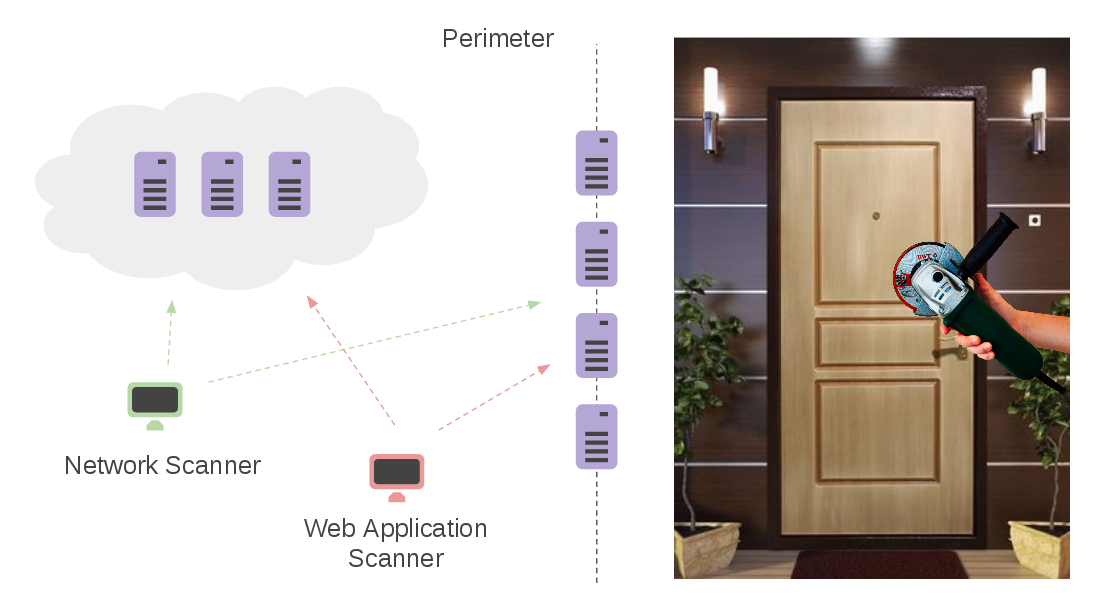
What does it mean to control the network perimeter? Well, practically this process consist of two main parts:
- Assessing network hosts that are facing Internet using some Network Scanner (Nessus, OpenVAS, Qualys, MaxPatrol. F-Secure Radar, etc.)
- Assessing application servers, e.g. Web Servers, on these hosts using some special tools, e.g. Web Application Scanners (Acunetix, Burp Suite, Qualys WAS, Tenable.io WAS, High-Tech Bridge ImmuniWeb, etc.)
Active scanning is a good method of perimeter assessment. Dynamics of the assets is relatively low, comparing with the Office Network. Perimeter hosts usually stays active all the time, including the time when you are going to scan scanning them. 😉
Most of the dangerous vulnerabilities can be detected without authorization: problems with encryption (OpenSSL Heartbleed, Poodle, etc.). RCE and DoS of web servers and frameworks (Apache Struts and Equifax case)
The best results can be achieved with scanners deployed outside of your network. Thus, you will see your Network Perimeter the same way a potential attacker sees it. But certainly, you will be in a better position:
- You can ask your IT administrators to add your network and WAS scanners in white list, so they will not be banned.
- You can check and correlate scan results of remote scanner with (authenticated?) scan results produced by the scanner deployed in your organization’s network and thus filtering false positives.
What about the targets for scanning? How should you get them?
Continue reading →