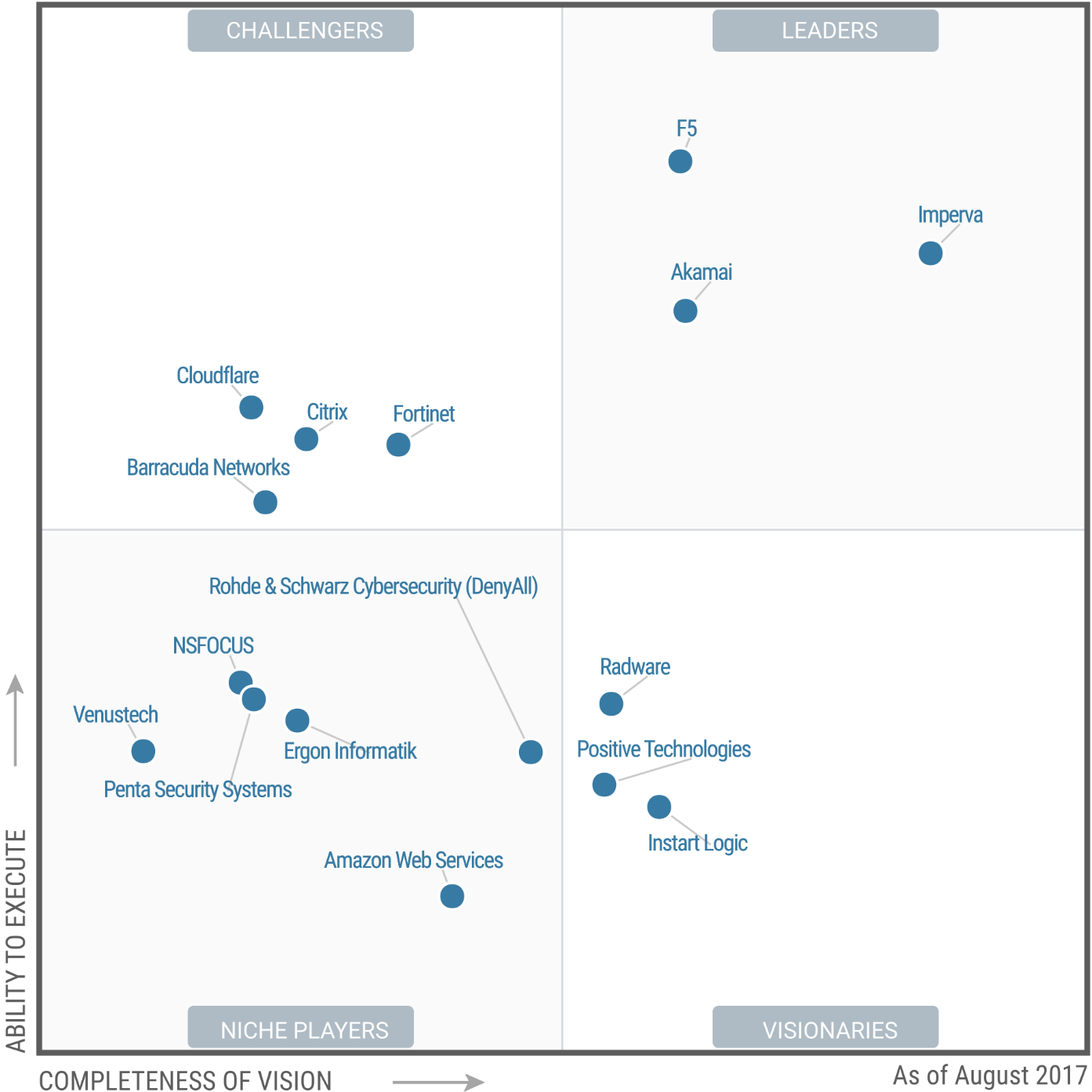
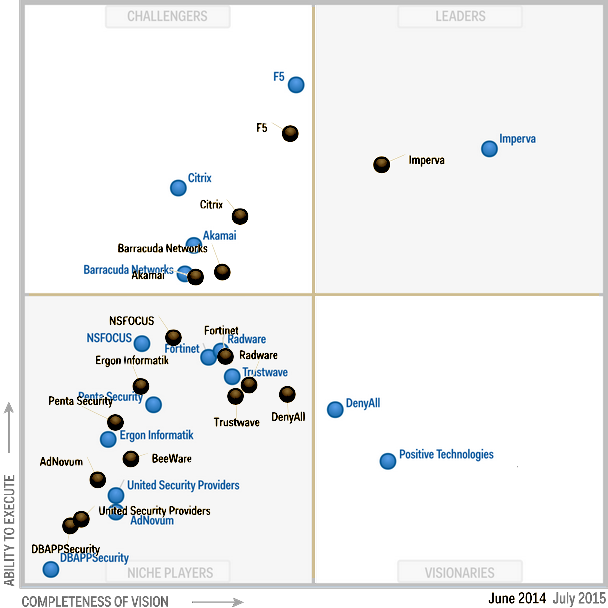
Continuing the story about recent CUPS vulnerabilities: vulnerable hosts will be used by attackers to amplify DDoS attacks.
Researchers from Akamai Technologies wrote about this. An attacker can send a special packet to a vulnerable host with CUPS: “add a printer located at this IP address”. CUPS will start sending large IPP/HTTP requests to the specified IP address. Thus, vulnerable hosts can be organized in such a way that they start DDoSing IP addresses chosen by the attacker.
Akamai has discovered more than 198,000 vulnerable hosts with CUPS, of which more than 58,000 (34%) can be used for DDoS attacks. Of these, hundreds demonstrated an “infinite loop” of requests in response to HTTP/404.
Assuming that all 58,000+ vulnerable hosts are used for the attack, they can cause a traffic flow of 1 GB to 6 GB per attacker’s udp packet. The victim will have to handle 2.6 million TCP connections and HTTP requests.